Question: Assume you have the following jobs to execute with one processor: Suppose a system uses RR scheduling with a quantum of 15. a. Create a
Assume you have the following jobs to execute with one processor:
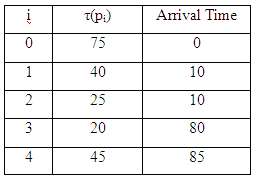
Suppose a system uses RR scheduling with a quantum of 15.
a. Create a Gantt chart illustrating the execution of these processes.
b. What is the turnaround time for process p3?
c. What is the average wait time for the processes?
T(p:) Arrival Time 75 1 40 10 25 10 3 20 80 4 45 85 2.
Step by Step Solution
3.49 Rating (162 Votes )
There are 3 Steps involved in it
RR scheduling with a time quantum of 15 a Gantt cha... View full answer

Get step-by-step solutions from verified subject matter experts
Document Format (1 attachment)
34-E-CE-OS (441).docx
120 KBs Word File


