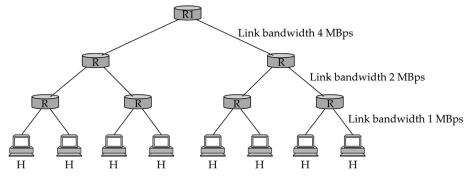
Consider the arrangement of host H and routers R and R1 in Figure 6.28. All links are
Question:
Consider the arrangement of host H and routers R and R1 in Figure 6.28. All links are full duplex, and all routers are faster than their links. Show that R1 cannot become congested, and for any other router R, we can find a traffic pattern that congests that router alone.
Figure 6.28)
Transcribed Image Text:
R H H H H RI H Link bandwidth 4 MBps H Link bandwidth 2 MBps H Link bandwidth 1 MBps H
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 0% (1 review)
The network topology in Figure 628 shows a hierarchical arrangement with a top router R1 connected to other routers R which in turn are connected to s...View the full answer

Answered By

JAPHETH KOGEI
Hi there. I'm here to assist you to score the highest marks on your assignments and homework. My areas of specialisation are:
Auditing, Financial Accounting, Macroeconomics, Monetary-economics, Business-administration, Advanced-accounting, Corporate Finance, Professional-accounting-ethics, Corporate governance, Financial-risk-analysis, Financial-budgeting, Corporate-social-responsibility, Statistics, Business management, logic, Critical thinking,
So, I look forward to helping you solve your academic problem.
I enjoy teaching and tutoring university and high school students. During my free time, I also read books on motivation, leadership, comedy, emotional intelligence, critical thinking, nature, human nature, innovation, persuasion, performance, negotiations, goals, power, time management, wealth, debates, sales, and finance. Additionally, I am a panellist on an FM radio program on Sunday mornings where we discuss current affairs.
I travel three times a year either to the USA, Europe and around Africa.
As a university student in the USA, I enjoyed interacting with people from different cultures and ethnic groups. Together with friends, we travelled widely in the USA and in Europe (UK, France, Denmark, Germany, Turkey, etc).
So, I look forward to tutoring you. I believe that it will be exciting to meet them.
3.00+
2+ Reviews
10+ Question Solved
Related Book For 

Computer Networks A Systems Approach
ISBN: 9780128182000
6th Edition
Authors: Larry L. Peterson, Bruce S. Davie
Question Posted:
Students also viewed these Computer science questions
-
Planning is one of the most important management functions in any business. A front office managers first step in planning should involve determine the departments goals. Planning also includes...
-
During the month of January, Learnstream Company conducted the following transactions: Jan 1 Jan 2 Jan 5 Jan 17 Jan 20 Customers purchased $1,200 in gift cards. Sold merchandise for $8,600 cash plus...
-
Investigate the challenges and solutions associated with managing I/O devices in a multitasking operating system, including topics such as device drivers, interrupt handling, DMA (Direct Memory...
-
Evaluate and simplify the following derivatives. d dx -(x Inx)
-
A solid conducting sphere of radius R carries a charge Q. Calculate the electric-field energy density at a point a distance r from the center of the sphere for (a) r < R and (b) r > R. (c) Calculate...
-
Compare and contrast styles of conflict management along the dimensions of assertiveness and cooperativeness. LO.1
-
What is the basis for setting tolerance? LO.1
-
You run a regression of monthly returns of Mapco, an oil-and gas-producing firm, on the S&P 500 Index and come up with the following output for the period 19911995. Intercept of the regression =...
-
The first audit of the books of Vaughn Company was made for the year ended December 31,2026. In examining the books, the auditor found that certain items had been overlooked or incorrectly handled in...
-
Suppose a congestion control scheme results in a collection of competing flows that achieve the following throughput rates: 100 kBps, 60 kBps, 110 kBps, 95 kBps, and 150 kBps. (a) Calculate the...
-
Is it possible for TCP Reno to reach a state with the congestion window size much larger than (e.g., twice as large as) RTT bandwidth? Is it likely?
-
Refer to the following financial statements for Kodak: Liabilities and shareholders equity Current liabilities Required: Prepare forecasts of its income statement, balance sheet, and statement of...
-
What is the discount rate? PV = 7 0 0 ; t = 5 year period; FV = 1 0 0 0
-
How is planning illustrated in this case story? How is strategic management illustrated in this case story? The new CEO stated that the CEO's job is to give employees a point of view. Explain what...
-
Explain the Following Questions: 1. What essential characteristics exist in a proper understanding of "personal mastery," so that as an individual achieves greater progress in this discipline, they...
-
Few people want to eat discolored french fries. Potatoes are kept refrigerated before being cut for french fries to prevent spoiling and preserve flavor. But immediate processing of cold potatoes...
-
Part 3 of 4 Points: 0.49 of 1 Compute P(X) using the binomial probability formula. Then determine whether the normal distribution can be used to estimate this probability. If so, approximate P(X)...
-
Recall that a fictitious brand of a healthy food product- sliced apples-was packaged to appeal to children (a smiling cartoon apple was on the front of the package). The researchers compared the...
-
Willingness to pay as a measure of a person's value for a particular good measures the maximum a person would be willing to pay requires that payment actually be made depends on the satisfaction that...
-
Consider sending a stream of packets from Host A to Host B using IPsec. Typically, a new SA will be established for each packet sent in the stream. True or false?
-
Consider the example in Figure 8.28. Suppose Trudy is a woman-in-the middle. Who can insert data-grams into the stream of data-gram going from Rl and R2. As part of a reply attack, Trudy sends a...
-
The following true/false questions pertain to Figure 8.28. a. When a host in 172.16.1/24 sends a data-gram to an Amazon.con, server, the router Rl will encrypt the data-gram using IPsec. b. When a...
-
Berbice Inc. has a new project, and you were recruitment to perform their sensitivity analysis based on the estimates of done by their engineering department (there are no taxes): Pessimistic Most...
-
#3) Seven years ago, Crane Corporation issued 20-year bonds that had a $1,000 face value, paid interest annually, and had a coupon rate of 8 percent. If the market rate of interest is 4.0 percent...
-
I have a portfolio of two stocks. The weights are 60% and 40% respectively, the volatilities are both 20%, while the correlation of returns is 100%. The volatility of my portfolio is A. 4% B. 14.4%...

Study smarter with the SolutionInn App


