Question: In a transposition cipher the encryption and decryption keys are often represented as two one-dimension tables (arrays) and the cipher is represented as a piece
In a transposition cipher the encryption and decryption keys are often represented as two one-dimension tables (arrays) and the cipher is represented as a piece of software (a program).
a. Show the array for the encryption key in Figure 31.6 in the text.
b. Show the array for the decryption key in Figure 31.6 in the text.
Figure 31.6
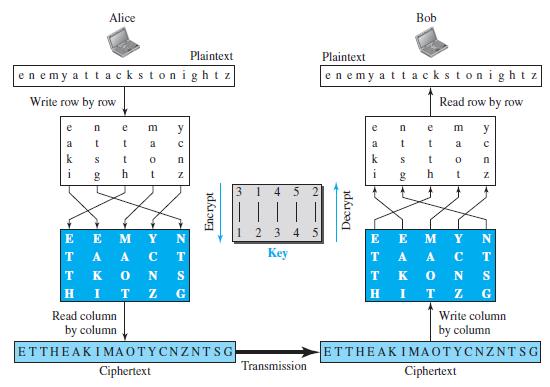
c. Explain, given the encryption key, how we can find the decryption key.
Alice Bob Plaintext Plaintext enemy attackstonightz enemy attackstonight z Write row by row Read row by row e e m y m y a a a k k h i h 3. 4 5 123 4 5 E E TA A T K E E M T ey A A. S T. K H G Read column Write column by column by column ETTHEAKIMAOTYCNZNTSG ETTHEAK IMAOTYCNZNTSG Transmission Ciphertext Ciphertext Z N OT Decrypt Encrypt NZ
Step by Step Solution
3.46 Rating (185 Votes )
There are 3 Steps involved in it
The content of each element represents the input col... View full answer

Get step-by-step solutions from verified subject matter experts


