Question: The DiffieHellman key exchange protocol is vulnerable to a manin-the-middle attack as shown in Figure 8.7. Outline how DiffieHellman can be extended to protect against
The Diffie–Hellman key exchange protocol is vulnerable to a “manin-the-middle” attack as shown in Figure 8.7. Outline how Diffie–Hellman can be extended to protect against this possibility.
Figure 8.7)
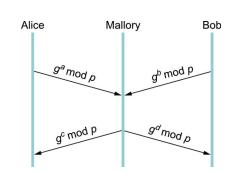
Alice g mod p gf mod p Mallory g mod p go mod p Bob
Step by Step Solution
3.42 Rating (155 Votes )
There are 3 Steps involved in it
The DiffieHellman key exchange protocol is a method for two parties to jointly establish a shared secret key over an insecure communication channel Ho... View full answer

Get step-by-step solutions from verified subject matter experts


