Buffers are employed between different levels of memory hierarchy to reduce access latency. For this given configuration,
Question:
Buffers are employed between different levels of memory hierarchy to reduce access latency. For this given configuration, list the possible buffers needed between L1 and L2 caches, as well as L2 cache and memory.
Recall that we have two write policies and write allocation policies, and their combinations can be implemented either in L1 or L2 cache.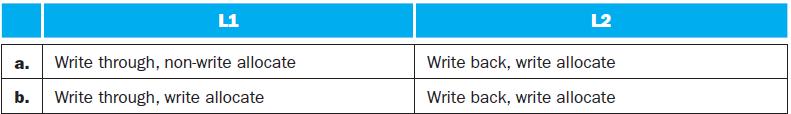
Transcribed Image Text:
L1 a. Write through, non-write allocate b. Write through, write allocate L2 Write back, write allocate Write back, write allocate
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 75% (4 reviews)
The following are the possible buffers needed between L1 and L2 caches as well as L2 cache and memory for the given configuration Between L1 and L2 ca...View the full answer

Answered By

Gauri Hendre
I worked as EI educator for Eduphy India YT channel. I gave online tutorials to the students who were living in the villages and wanted to study much more and were preparing for NEET, TET. I gave tutions for topics in Biotechnology. I am currently working as a tutor on course hero for the biochemistry, microbiology, biology, cell biology, genetics subjects. I worked as a project intern in BAIF where did analysis on diseases mainly genetic disorders in the bovine. I worked as a trainee in serum institute of India and Vasantdada sugar institute. I am working as a writer on Quora partner program from 2019. I writing on the topics on social health issues including current COVID-19 pandemic, different concepts in science discipline. I learned foreign languages such as german and french upto A1 level. I attended different conferences in the science discipline and did trainings in cognitive skills and personality development skills from Lila Poonawalla foundation. I have been the member of Lila poonawalla foundation since 2017. Even I acquired the skills like Excel spreadsheet, MS Office, MS Powerpoint and Data entry.
5.00+
4+ Reviews
10+ Question Solved
Related Book For 

Computer Organization And Design The Hardware Software Interface
ISBN: 9780123747501
4th Revised Edition
Authors: David A. Patterson, John L. Hennessy
Question Posted:
Students also viewed these Computer science questions
-
Recall that we have two write policies and write allocation policies, and their combinations can be implemented either in L1 or L2 cache. Assume the following choices for L1 and L2 caches: L1...
-
For a multilevel exclusive cache (a block can only reside in one of the L1 and L2 caches), configuration, describe the procedure of handling an L1 write-miss, considering the component involved and...
-
Describe the procedure of handling an L1 write-miss, considering the component involved and the possibility of replacing a dirty block. Recall that we have two write policies and write allocation...
-
Giroud plc is considering two alternative investment opportunities. Each of the two projects has an expected life of five years and requires an initial investment of $100,000. A feasibility study...
-
Valentins Acting School produces annual cash flows of $5,000 and is expected to continue doing so in the infinite future. The cost of equity capital for Valentins is 16 percent, and the firm is...
-
Two-tailed test, n = 17, and t = 2.733 a. Use Table IV in Appendix A to estimate the P-value. b. Based on your estimate in part (a), state at which significance levels the null hypothesis can be...
-
The financial information below was taken from the records of White Bones, Inc. 1997 1996 Balance Sheet t Equipment Less: Accumulated depreciation Net book value $37,500 17,600 $19,900 $32,700 14,300...
-
The trial balance columns of the worksheet for Firmament Roofing at March 31, 2014, are as follows. Other data: 1. A physical count reveals only $550 of roofing supplies on hand. 2. Depreciation for...
-
29. The strategy of making bolt-on acquisitions to accelerate product offerings a. has not been proven to create value. b. can create positive but average value compared to other intrinsic product...
-
Assuming that the L1 hit time determines the cycle times for P1 and P2, what are their respective clock rates? In this exercise, we will look at the different ways capacity affects overall...
-
What is the cache line size (in words)? For a direct-mapped cache design with a 32-bit address, the following bits of the address are used to access the cache. a. b. Tag 31-10 31-12 Index 9-5 11-6...
-
Explain why D must be a right angle. B 12 15 9 C 6 10 D E
-
7.) In 1999, the average percentage of women who received prenatal care per country is 80.1%. Table #7.3.9 contains the percentage of woman receiving prenatal care in 2009 for a sample of countries...
-
Describe A demographic profile of the population and community that will be served through the reinvented Human Service program. The description must include all eligibility requirements (i.e.,...
-
You work for a major financial institution. Your branch handles customer calls from a wide variety of individuals. Recently, you've noticed an increase in calls from individuals from African...
-
Pop Company holds 70% of Son Company stock. Pop has sold inventory to Son Company as follows: Percent of Sold Sales Inventory Cost to Price to Held at Year Pop Son Year end 2018 $203,000 $355,000 30%...
-
A B C D E F G H J K L 1 Cost Mortgage Payments 2 Cost Description The upscale hotel's building was acquired for $10 million, leading to monthly mortgage payments of $60,000. Behavior Dollar Amount...
-
A curve in a stretch of highway has radius R. The road is banked at angle to the horizontal. The coefficient of static friction between the tires and road is s. What is the fastest speed that a car...
-
Interest Compounded Annually. When P dollars is invested at interest rate i, compounded annually, for t years, the investment grows to A dollars, where A = P(1 + i) t . Trevor's parents deposit $7800...
-
What are some reasons that CSMA/CD cannot be used in a wireless LAN?
-
Write and test a program that simulates the bit stuffing and bit unstuffing as shown in Figure 11.4. Figure 11.4 Bit stuffing and unstuffing Data from upper layer 0001111111001111101000 Stuffed Frame...
-
In Figure 15.24, two wireless networks, BSS1 and BSS2, are connected through a wired distribution system (DS), an Ethernet LAN. Assume station A in BSS1 needs to send a data frame to station C in...
-
I am struggling with understanding how to correctly solve this problem. If you could give general direction with the answer that would be amazing. Thank you! Homework:Module 2 Exercises DeWitt...
-
ACC 241 Uses of Accounting Information II (1) Zach Walden & 12/03/21 3:59 PM | = Homework: HW #10 - Chapter 11 Question 10, E11-31A (si. Part 1 of 6 1 HW Score: 0%, 0 of 10 points O Points: 0 of 1 0...
-
Walton Auto Repair, Inc. Is evaluating a project to purchase equipment that will not only expand the company's capacity but also Improve the quality of its repair services. The board of directors...

Study smarter with the SolutionInn App


