Question: The following table shows further pairs of decimal numbers. Write the loop in MIPS assembly language. a. b. A 8.625 x 10 1.84375 x 10
The following table shows further pairs of decimal numbers.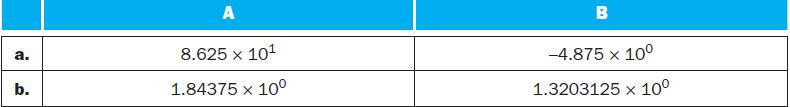
Write the loop in MIPS assembly language.
a. b. A 8.625 x 10 1.84375 x 10 B -4.875 x 10 1.3203125 x 10
Step by Step Solution
3.35 Rating (155 Votes )
There are 3 Steps involved in it
MIPS Assembly Language is a textual humanreadable representat... View full answer

Get step-by-step solutions from verified subject matter experts


