Question: This books Web site includes a copy of the ACM Code of Professional Conduct from 1982. Compare this Code with the 1997 ACM Code of
This book’s Web site includes a copy of the ACM Code of Professional Conduct from 1982. Compare this Code with the 1997 ACM Code of Ethics and Professional Conduct (Figure 23.7).
a. Are there any elements in the 1982 Code not found in the 1997 Code? Propose a rationale for excluding these.
b. Are there any elements in the 1997 Code not found in the 1982 Code? Propose a rationale for adding these.
Figure 23.7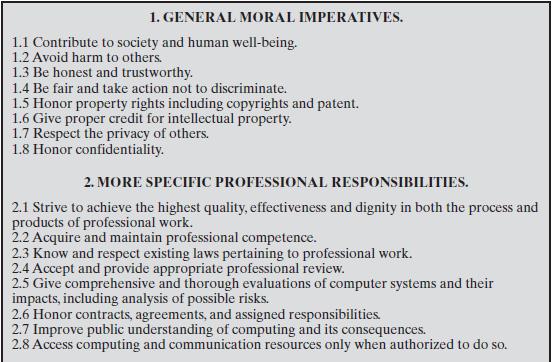
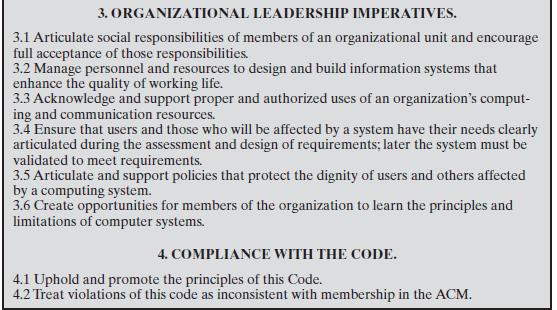
1. GENERAL MORAL IMPERATIVES. 1.1 Contribute to society and human well-being. 1.2 Avoid harm to others. 1.3 Be honest and trustworthy. 1.4 Be fair and take action not to discriminate. 1.5 Honor property rights including copyrights and patent. 1.6 Give proper credit for intellectual property. 1.7 Respect the privacy of others. 1.8 Honor confidentiality. 2. MORE SPECIFIC PROFESSIONAL RESPONSIBILITIES. 2.1 Strive to achieve the highest quality, effectiveness and dignity in both the process and products of professional work. 2.2 Acquire and maintain professional competence. 2.3 Know and respect existing laws pertaining to professional work. 2.4 Accept and provide appropriate professional review. 2.5 Give comprehensive and thorough evaluations of computer systems and their impacts, including analysis of possible risks. 2.6 Honor contracts, agreements, and assigned responsibilities. 2.7 Improve public understanding of computing and its consequences. 2.8 Access computing and communication resources only when authorized to do so.
Step by Step Solution
3.40 Rating (166 Votes )
There are 3 Steps involved in it
a EC12 EC22 and EC41 seem designed more to protect A... View full answer

Get step-by-step solutions from verified subject matter experts


