Question:
As the IT audit senior of the engagement, you are presenting to the IT manager and partner (as part of the planning meeting) the results of the risk assessment performed in Exhibit 3.3.
Exhibit 3.3.
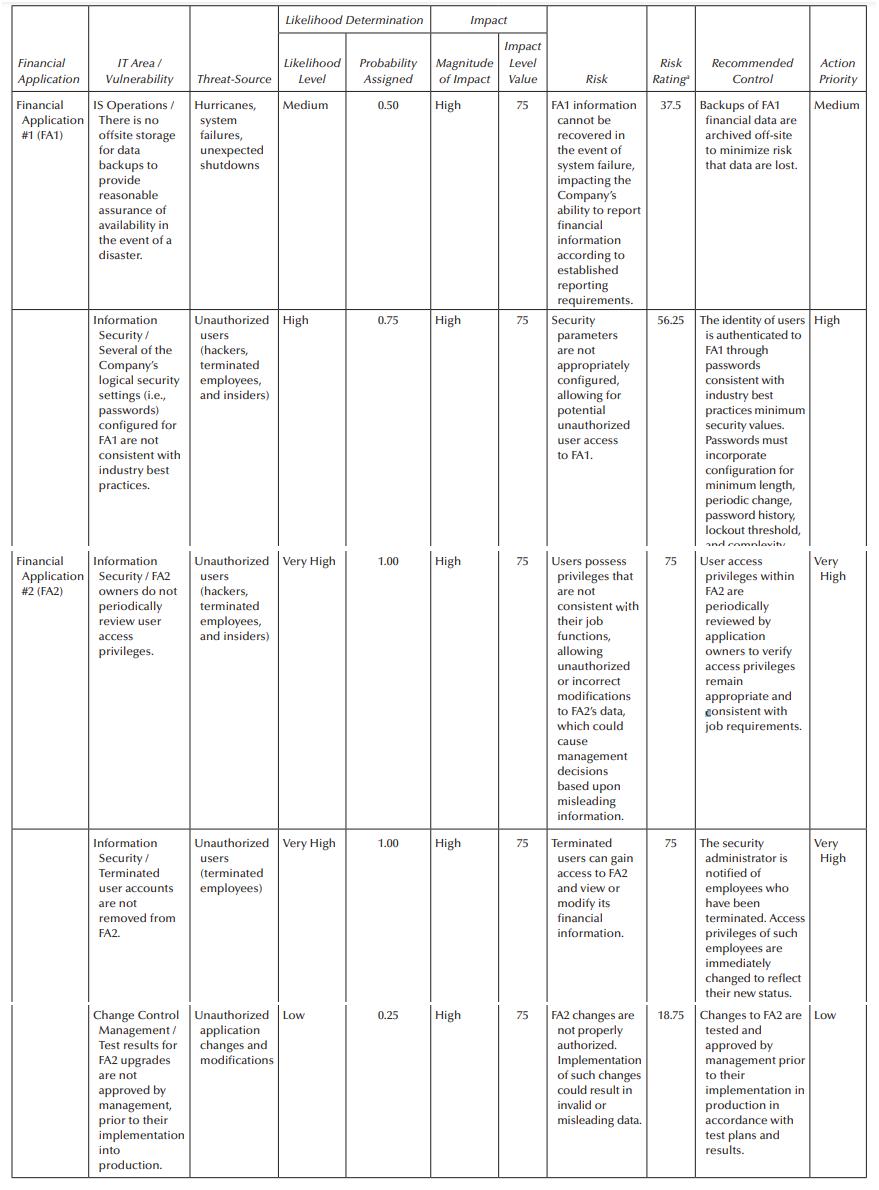
Based on such results (look at Exhibit 3.3, under the “Risk Rating” and “Action Priority” columns), it seems clear that the audit should focus on Financial Application #2 (FA2). Nevertheless, the IT manager and partner, based on previous relevant experience, believe that the audit should be performed on Financial Application #1 (FA1). The planning meeting is over, and you still feel doubtful on the decision just made. Your task: Prepare a two-page memo to the audit manager (copying the partner) stating your reasons why FA2 should be audited first. In order to convince the audit manager and partner, you are to think “outside the box.” In other words, think of additional information not necessarily documented in the risk assessment shown in Exhibit 3.3, and document in your memo information related to:
a. Any additional vulnerabilities or weaknesses that may currently be in place affecting FA2
b. Any additional threat-sources that can trigger the vulnerabilities or weaknesses you just identified for FA2
c. Any additional risks or situations involving exposure to loss for the financial information in FA2
d. Any additional controls or procedures that should be implemented to mitigate the risks just identified
Transcribed Image Text:
Financial
Application
Financial
Application
#1 (FA1)
IT Area /
Vulnerability
IS Operations /
There is no
offsite storage
for data
backups to
provide
reasonable
assurance of
availability in
the event of a
disaster.
Information
Security/
Several of the
Company's
logical security
settings (i.e.,
passwords)
configured for
FA1 are not
consistent with
industry best
practices.
Financial Information.
Application Security/FA2
#2 (FA2)
owners do not
periodically
review user
access
privileges.
Information
Security/
Terminated
user accounts
are not
removed from
FA2.
Change Control
Management/
Test results for
FA2 upgrades
are not
approved by
management,
prior to their
implementation
into
production.
Hurricanes,
system
failures,
Threat-Source Level
unexpected
shutdowns
Likelihood Determination
Likelihood
Medium
Unauthorized High
users
(hackers,
terminated
employees,
and insiders)
users
(terminated
employees)
Unauthorized Very High
users
(hackers,
terminated
employees,
and insiders)
Unauthorized Very High
Unauthorized Low
application
changes and
modifications
Impact
Probability
Probability Magnitude Level
Assigned
of Impact
Value
0.50
High
0.75
1.00
1.00
0.25
High
High
High
Impact
High
75
75
75
75
75
Risk
FA1 information
cannot be
recovered in
the event of
system failure.
impacting the
Company's
ability to report
financial
information
according to
established
reporting
requirements.
Security
parameters
are not
appropriately
configured,
allowing for
potential
unauthorized
user access
to FA1.
Users possess
privileges that
are not
consistent with
their job
functions,
allowing
unauthorized
or incorrect
modifications
to FA2's data,
which could
cause
management
decisions
based upon
misleading
information.
Terminated
users can gain
access to FA2
and view or
modify its
financial
information.
FA2 changes are
not properly
authorized.
Implementation
of such changes
could result in
invalid or
misleading data.
Risk
Rating
37.5
75
75
Recommended
Control
18.75
Backups of FA1
financial data are
archived off-site
to minimize risk
that data are lost.
56.25 The identity of users High
is authenticated to
FA1 through
passwords
consistent with
industry best
practices minimum
security values.
Passwords must
incorporate
configuration for
minimum length,
periodic change,
password history,
lockout threshold,
and complavitu
User access.
privileges within
FA2 are
periodically
reviewed by
application
owners to verify
access privileges
remain
appropriate and
consistent with
job requirements.
The security
administrator is
notified of
employees who
have been
terminated. Access
privileges of such
employees are
immediately
changed to reflect
their new status.
Action
Priority
Medium
implementation in
production in
accordance with
test plans and
results.
Very
High
Very
High
Changes to FA2 are Low
tested and
approved by
management prior
to their







