Question: The output of Fig. 16.14 shows that Priority-Queue orders Double elements in ascending order. Rewrite Fig. 16.14 so that it orders Double elements in descending
The output of Fig. 16.14 shows that Priority-Queue orders Double elements in ascending order. Rewrite Fig. 16.14 so that it orders Double elements in descending order (i.e., 9.8 should be the highest-priority element rather than 3.2).
Fig. 16.14
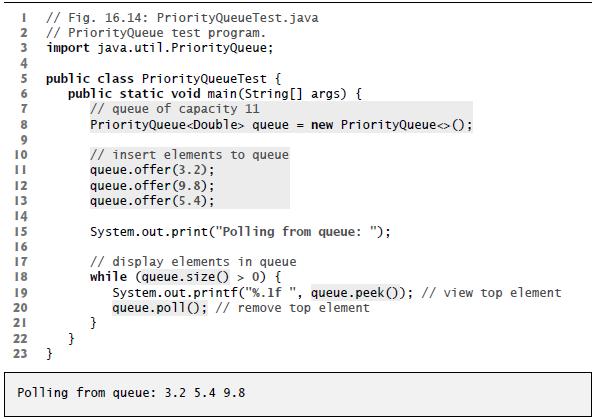
1 // Fig. 16.14: PriorityQueueTest.java 2 // PriorityQueue test program. 3 import java.util.PriorityQueue; 4 5 6 9 10 [] 12 13 14 15 16 17 18 public class PriorityQueue Test { public static void main (String[] args) { //queue of capacity 11 PriorityQueue queue = new PriorityQueue (); 19 20 21 22 23 } } // insert elements to queue queue. offer (3.2); queue.offer (9.8); queue. offer (5.4); System.out.print("Polling from queue: "); // display elements in queue while (queue.size() > 0) { } System.out.printf("%.1f ", queue.peek()); // view top element queue.poll(); // remove top element Polling from queue: 3.2 5.4 9.8
Step by Step Solution
3.46 Rating (162 Votes )
There are 3 Steps involved in it
To order the elements of the PriorityQueue in descending order you need to modify the code to provid... View full answer

Get step-by-step solutions from verified subject matter experts


