Question: Assume that a database stores records consisting of a 2-byte integer key and a variable-length data field consisting of a string. Show the linear index
Assume that a database stores records consisting of a 2-byte integer key and a variable-length data field consisting of a string. Show the linear index (as illustrated by Figure 10.1) for the following collection of records:
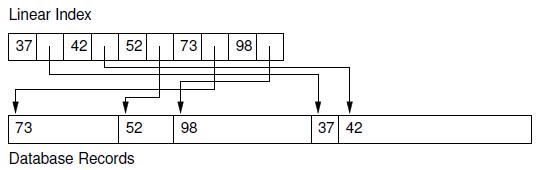

Linear Index 37 42 52 73 73 Database Records 52 98 98 37 42
Step by Step Solution
3.53 Rating (156 Votes )
There are 3 Steps involved in it
vbnet Linear Index 37 42 52 7... View full answer

Get step-by-step solutions from verified subject matter experts


