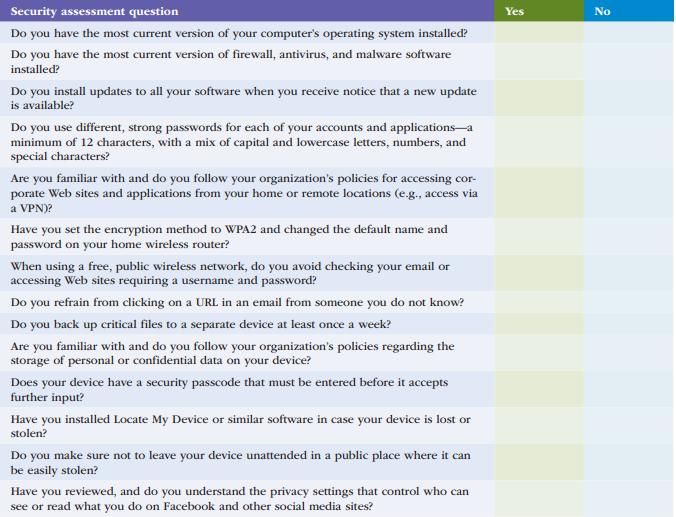
Use Table 2.6 to conduct a security self-assessment. Identify specific follow-up actions you need to take. Data
Question:
Use Table 2.6 to conduct a security self-assessment. Identify specific follow-up actions you need to take.
Data in Table 2.6
Transcribed Image Text:
Security assessment question Do you have the most current version of your computer's operating system installed? Do you have the most current version of firewall, antivirus, and malware software installed? Do you install updates to all your software when you receive notice that a new update is available? Do you use different, strong passwords for each of your accounts and applications-a minimum of 12 characters, with a mix of capital and lowercase letters, numbers, and special characters? Are you familiar with and do you follow your organization's policies for accessing cor- porate Web sites and applications from your home or remote locations (e.g., access via a VPN)? Have you set the encryption method to WPA2 and changed the default name and password on your home wireless router? When using a free, public wireless network, do you avoid checking your email or accessing Web sites requiring a username and password? Do you refrain from clicking on a URL in an email from someone you do not know? Do you back up critical files to a separate device at least once a week? Are you familiar with and do you follow your organization's policies regarding the storage of personal or confidential data on your device? Does your device have a security passcode that must be entered before it accepts further input? Have you installed Locate My Device or similar software in case your device is lost or stolen? Do you make sure not to leave your device unattended in a public place where it can be easily stolen? Have you reviewed, and do you understand the privacy settings that control who can see or read what you do on Facebook and other social media sites? Yes No
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 60% (15 reviews)
Table 26 Security SelfAssessment Security Domain Assessment FollowUp Actions Access Control Limited access to authorized ...View the full answer

Answered By

Monette Taban
I am currently studying Computer Science Engineering, Due to my interest in programming languages and coding, I am interesetd on Technology so I search about it read about different types of technologies, I think my this habbis will help me to solve problems of students and that is why I am signing as a question answer expert.
0.00
0 Reviews
10+ Question Solved
Related Book For 

Principles Of Information Systems
ISBN: 9780357112410
14th Edition
Authors: Ralph Stair, George Reynolds
Question Posted:
Students also viewed these Computer science questions
-
List three specific parts of the Case Guide, Objectives and Strategy Section (See below) that you had the most difficulty understanding. Describe your current understanding of these parts. Provide...
-
Planning is one of the most important management functions in any business. A front office managers first step in planning should involve determine the departments goals. Planning also includes...
-
Case Study: Quick Fix Dental Practice Technology requirements Application must be built using Visual Studio 2019 or Visual Studio 2017, professional or enterprise. The community edition is not...
-
Ski Aus is a company that makes fashionable, high performance and expensive ski clothing (ski wear). Ski Aus has traditionally segmented the market by clothing type (e.g., ski pants, ski jackets,...
-
A real estate agent wants to know how many owners of homes worth over $1,000,000 might be considering putting their home on the market in the next 12 months. He surveys 40 of them and finds that 10...
-
Research designed to determine the effectiveness of advertising would be considered a market measurement study. T F
-
Describe the application of behavior modification to worker motivation. LO.1
-
On September 1, the balance of the Accounts Receivable control account in the general ledger of Johns Produce, Inc., was $11,960.The customers subsidiary ledger contained account balances as follows:...
-
Dorsey Company manufactures three products from a common input in a joint processing operation. Joint processing costs up to the split-off point total $300,000 per quarter. For financial reporting...
-
You are going to perform a security risk assessment for your small company. What steps must be taken?
-
Discuss how the CIS security triad can be implemented at the organizational level to safeguard against cyberattacks.
-
In about 100 words, explain what a card not present transaction is and why it presents a greater risk than card present transactions for a retail business.
-
In Exercises 29 and 30, find the probabilities and indicate when the "5% guideline for cumbersome calculations" is used. 29. Medical Helicopters In a study of helicopter usage and patient survival,...
-
Introduction to Internetworking Project 1: Ctrl-Alt-Del Inc. INTRODUCTION You have accepted a contract to participate in the design of the network infrastructure of a company called Ctrl-Alt-Del Inc....
-
Construct Arguments Tell whether each statement is always true, sometimes true, or never true. Explain. a. An integer is a whole number. b. A natural number is a rational number. c. An irrational...
-
Please answer the following Questions : 1. Who are the competitors for Whole Foods? 2. Do you consider traditional supermarkets to be competitors for natural and organic supermarkets? 3. How would...
-
LNC Corp is trying to determine the effect of its inventory turnover ratio and DSO on its cash conversion. Credit sales in 2016 is $101,000, cost of goods sold will be 70% of sales and it earned a...
-
The Internet Use data file on the books website contains data on the number of individuals in a country with broadband access and the population size for each of 32 nations. When using population...
-
Research corporate acquisitions using Web resources and then answer the following questions: Why do firms purchase other corporations? Do firms pay too much for the acquired corporation? Why do so...
-
What is a knowledge repository?
-
Identify the basic components of an expert sys- tem and describe the role of each.
-
Describe the roles of the domain expert, the knowledge engineer, and the knowledge user in expert systems.
-
When direct materials are issued from the storeroom, are any entries made in the subsidiary records? Question 2 options: Increase raw material item record Decrease raw material item record No entry...
-
Riverrun Co. provides medical care and insurance benefits to its retirees. In the current year, Riverrun agrees to pay $5,500 for medical insurance and contribute an additional $9,000 to a retirement...
-
DETAILS 1. [-/1 Points) SMITHNM13 11.2.025. MY NOTES Convert the credit card rate to the APR. Oregon, 2% per month % Need Help? ReadIt Watch

Study smarter with the SolutionInn App


