Question: , ( ) ( ) .
ɪɴ ᴛʜᴇ ꜰᴏʟʟᴏᴡɪɴɢ ꜰɪɢᴜʀᴇ, ɢɪᴠᴇɴ ᴛʜᴇ ᴘᴀɪʀ ᴏꜰ ᴀᴅᴅʀᴇꜱꜱᴇꜱ ( ʟᴏɢɪᴄᴀʟ ᴀɴᴅ ᴘʜʏꜱɪᴄᴀʟ) ꜰᴏʀ ᴇᴀᴄʜ ᴅᴇᴠɪᴄᴇ (ᴄᴏᴍᴘᴜᴛᴇʀ ᴏʀ ʀᴏᴜᴛᴇʀ) ꜰᴏʀ ᴇᴀᴄʜ ᴄᴏɴɴᴇᴄᴛɪᴏɴ. ᴡʀɪᴛᴇ ᴅᴏᴡɴ ᴛʜᴇ ᴘʜʏꜱɪᴄᴀʟ ᴀɴᴅ ʟᴏɢɪᴄᴀʟ ᴀᴅᴅʀᴇꜱꜱᴇꜱ ᴏꜰ ᴛʜᴇ ᴅᴀᴛᴀ ʟɪɴᴋ ʟᴀʏᴇʀ ᴀᴛ ᴇᴀᴄʜ ᴅᴇᴠɪᴄᴇ .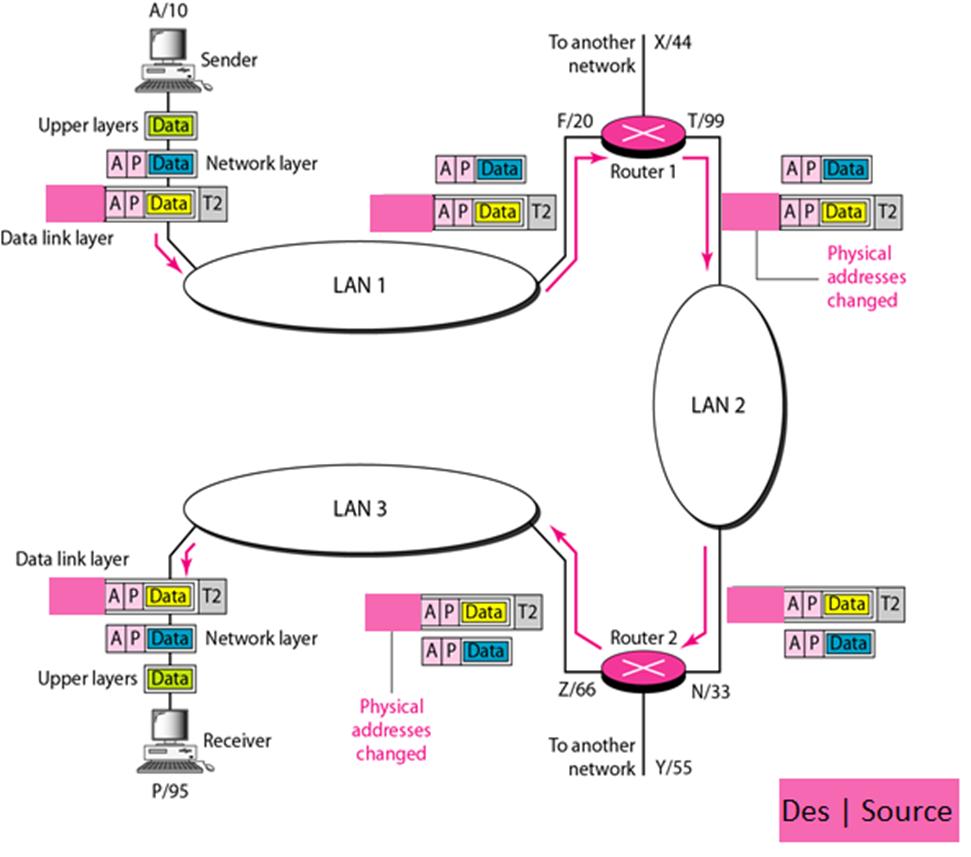
A/10 To another | X/44 Sender network Upper layers Data F/20 T/99 AP Data Network layer AP Data Router 1 AP Data AP Data T2 AP Data T2 AP Data T2 Data link layer Physical addresses changed LAN 1 LAN 2 LAN 3 Data link layer AP Data T2 AP Data T2 AP Data T2 AP Data Network layer AP Data Router 2 AP Data Upper layers Data Z/66 N/33 Physical addresses Receiver To another network I Y/55 changed P/95 Des | Source
Step by Step Solution
3.45 Rating (168 Votes )
There are 3 Steps involved in it
ANSWER x19 Destination host To andher netwoak D... View full answer

Get step-by-step solutions from verified subject matter experts


