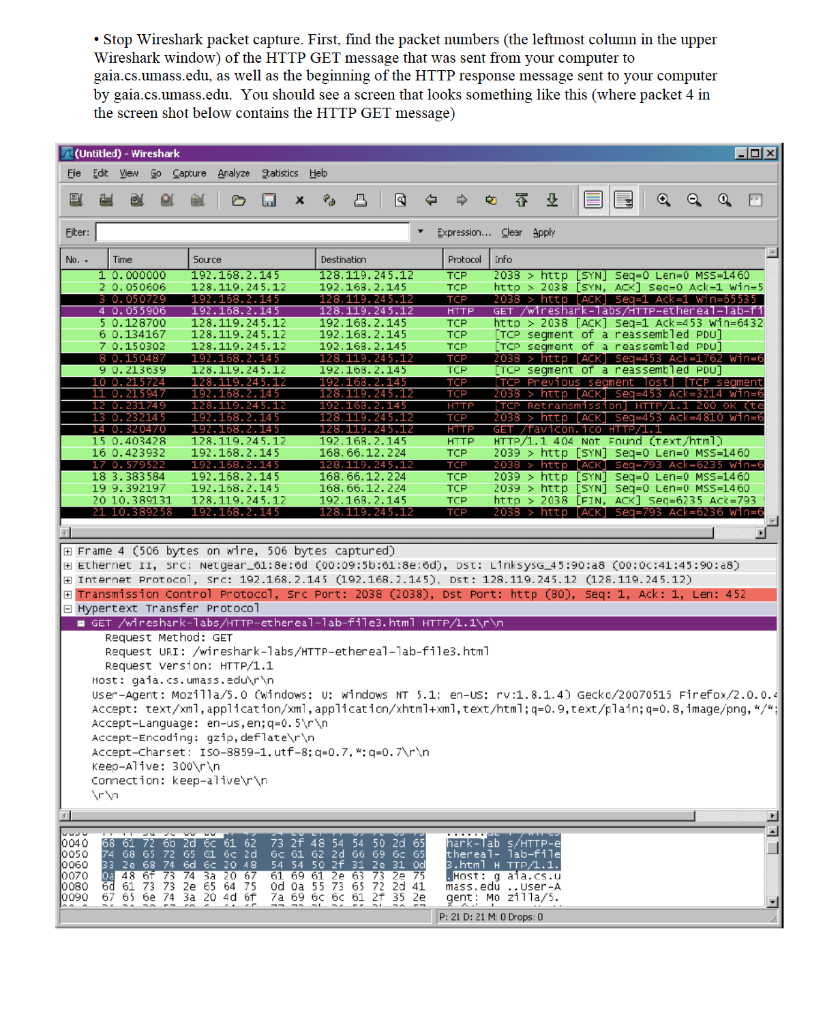


1. (14pts) If all the links in the Internet were to provide reliable delivery service, would the TCP reliable delivery service be redundant? Why or why not? 2. (16pts) Suppose two nodes start to transmit at the same time a packet of length L over a broadcast channel of rate R. Denote the propagation delay between the two nodes as dprop Will there be a collision if dprop L/R? Why or why not? 3. (14pts) Recall that with the CSMA/CD protocol, the adapter waits K*512bit times after a collision, where K is drawn randomly. For K 100, how long does the adapter wait until returning to Step 2 for a 10 Mbps broadcast channel? 4. (56pts) Do the Wireshark assignment in the next page. . Capturing and analyzing Ethernet frames Let's begin by capturing a set of Ethernet frames to study. Do the following First, make sure your browser's cache is empty. To do this under Mozilla Firefox V3, select Tools-> Clear Recent History and check the box for Cache. For Internet Explorer, select Tools->Internet Options->Delete Files. Start up the Wireshark packet sniffer Enter the following URL into your browser http://gaia.cs.umass.edu/wireshark-labs/HTTP- ethereal-lab-file3.html Your browser should display the rather lengthy US Bill of Rights. If you are unable to run Wireshark live on a computer, you can download the zip file http: gaa.cs.umass.edu wireshark-labs wireshark-traces zip and extract the file ethernet-ethereal-trace.. The traces in this zip file were collected by Wireshark running on one of the author's computers, while performing the steps indicated in the Wireshark lab. Once you have downloaded the trace, you can load it into Wireshark and view the trace using the File pull down menu, choosing Open, and then selecting the ethernet-ethereal-trace-1 trace file. You can then use this trace file to answer the questions below mnesn or the author's computers, while perfoming the sreps 1ac Stop Wireshark packet capture. First, find the packet numbers (the leftmost column in the upper Wireshark window) of the HTTP GET message that was sent from your computer to gaia.cs.umass.edu, as well as the beginning of the HTTP response message sent to your computer by gaia.cs.umass.edu. You should see a screen that looks something like this (where packet 4 in the screen shot below contains the HTTP GET message) (Untitled) - Wireshark Fie Edt Yew o Capcure Analyze tatisics Heb er Expression... Clear Appy Protocol nfo TCP TCP http 2038 [SYN, ACK] Seq-0 Ack-1 Win-5 No. Time Source 10.000000 192.168.2.145 2 o. 050606 128.119.245.12 192.163.2.145 3> http LSYN] Seq-0 Len-0 MSS-1460 128.119.245.12 192.163. 2.145 6 0.134167 128.119.245.12 192.163.2.145 192.163.2.145 TCP htto > 2038 [ACK] Seq-1 Ack 453 win-6432 TCP [TCP segment of a reassembled PDU] TCP 5 0.128700 128.119.245.12 7 0.150302 TCP segment of a reassembled PDU] 128.119.245.12 128, 119. 245. 192.168.2.145 192.168.2.145 128.119.245.12 TCP segment of a reassembled PDU 9 0.213639 11 0. 215947 13 0. 232145 192.163. 2.145 CP 128,119.245.12 TCP 2038 > http [ACK] Seq-453 Ack-3214 win-6 HTTP [TCP Retransmission] HTTP/1.1 200 oK (te TCP 128.119.245.12 038 > http [ACK] Seq 453 Ack 4810 win-6 15 0.40 16 0.423932 192.163.2.145 168. 66. 12. 224 HTTP HTTP/1.1 404 Not FOund (text/htm1 TCP 2039 > http [SYN] Seq=0 Len=0 MSS=1460 192.168.2.145 18 3.383 19 9. 392197192.168.2.145 20 10.389131 584 192.168.2.145 168.66.12.224 168. 66.12.224 192.163.2.145 TCP 2039> http [SYN] Seq-0 Len-0 MSS-1460 TCP 2039>http [SYN] Seq-0 Len-0 MSS-1460 TCP http >2038 LFIN, ACK] Seq-6235 Ack 793 128.119. 245.12 Frame 4 (506 bytes on wire, 506 bytes captured) Ethernet nternet protocol, src: 192.168.2.145 (192.168.2.145), Dst: 128.119.245.12 (128.119.245.12) 11, src: Netgear-o1 ; 8e ; 6d (00:09:5b:61 ; 8e ;od), Dst; LlnksysG_1 5:90:a8 (00:0( ;41:45:90;a8) Hypertext Transfer Protocol GET wireshark-labs/HTTP-Cthereal-1ab-fi1e3.htm1 HTTP/1.1trn Request Method: GET Request URI /wireshark-1abs/HTTP-ethereal-1ab-file3.html Request versionHTTP/1.1 Host: gaia.cs.umass.edur n User-Agent: Mozi1a/5.0 Cwindows: u: windows NT 5.1: en-US: rv:1.8.1.4) Gecko/20070515 Firefox/2.0.0.4 Accept : text/ml, application/xml, application/rhtnl +ml,text/html:geo. 9,text/plain; q-0.8 image/png "- Accept-Language : en-us , en;q=0.5 Accept-Encoding: gzip, deflatern Accept-Charset ISO-8859-1. utf-8:q-0.7. *:q-0.Artn Keep-Alve: 300 rn Connection: keep-livern 040 050 060 070 080 8 61 72 65 2d 6c 61 62 73 2f 48 54 54 50 2d 6 4 68 65 72 65 61 6c 2d 6c 61 62 2d 66 69 6c 65 3 2e 68 74 6d 6c 20 48 54 54 50 2f 31 2e 31 ark-lab s/HTTP- hereal lab-file .html H TTP/1.1. 61 73 73 2e 65 64 75 od Oa 55 73 65 72 2d 41 mass.ed.. user-A 090 67 65 6e 74 3a 2Q 4d 6f 7a 69 6c 6c 61 2f 35 2e gent. : M0 Z 11a/5. P: 21 D: 21 M 0 Drops: 0 0 So let's change Wireshark's "listing of captured packets" window so that it shows information only about protocols below IP. To have Wireshark do this, select Analyze-> Enabled Protocols. Then uncheck the IP box and select OK. You should now see an Wireshark window Frame 4 (5ce bytes on wr1re, 506 bytes captured) Destination : Linksys-45:9:18 (00:0c:41:45:00:aB) Add ess: LinksysG 45:90:8 (00:0c:41:45:90:48) = 1Gbit: Indtv1 dual address (unicast) source: Netgear, 61 : B2:6d (00:09 : 5b : 61:3e :60) Add-ess: Netgear 61:8e:ed (00:09:5b:61:8e:6d) - IG bit: nd1dual address (un cast) LG bit: Glohlly unique acdress (factary default) 2Eir contents windows (the middle and lower display windows in Wireshark) Select the Ethernet frame containing the HTTP GET message. (Recall that the HTTP GET message is carried inside of a TCP segment, which is carried inside of an IP datagram, which is carried inside 1 Ethernet frame (header as well as payload) are displayed in the packet contents window Answer the following questions, based on the contents of the Ethernet frame containing the HTTP GET message. Whenever possible, when answering a question you should hand in a printout of the packet(s) within the trace that you used to answer the question asked. Annotate the printout to explain your answer. To print a packet, use File->Print, choose Selected packet only, choose Packet summary line, and select the minimum amount of packet detail that you need to answer the question 1. 2. What is the 48-bit Ethernet address of your computer? What is the 48-bit destination address in the Ethernet frame? Is this the Ethernet address of gaia.cs.umass.edu? (Hint: the answer is no). What device has this as its Ethernet address? Note: this is an important question, and one that students sometimes get wrong. Re-read pages 468-469 in the text and make sure you understand the answer here.] Give the hexadecimal value for the two-byte Frame type field. What upper layer protocol does this correspond to? 4. How many bytes from the very start of the Ethernet frame does the ASCII "G" in "GET" appear in the Ethernet frame? Next, answer the following questions, based on the contents of the Ethernet frame containing the first byte of the HTTP response message. What is the value of the Ethernet source address? Is this the address of your computer, or of 6. What is the destination address in the Ethernet frame? Is this the Ethernet address of you 7. Give the hexadecimal value for the two-byte Frame type field. What upper layer protocol does 8. How many bytes from the very start of the Ethernet frame does the ASCII 0 in OK'' (i.e., gaia.cs.umass.edu (Hint: the answer is no). What device has this as its Ethernet address? computer? this correspond to? the HTTP response code) appear in the Ethernet frame











