Question: 1 6 points Two cryptographers encrypt a secret password consisting only of nonnegative integers less than min (11, 17) using an affine cipher. They
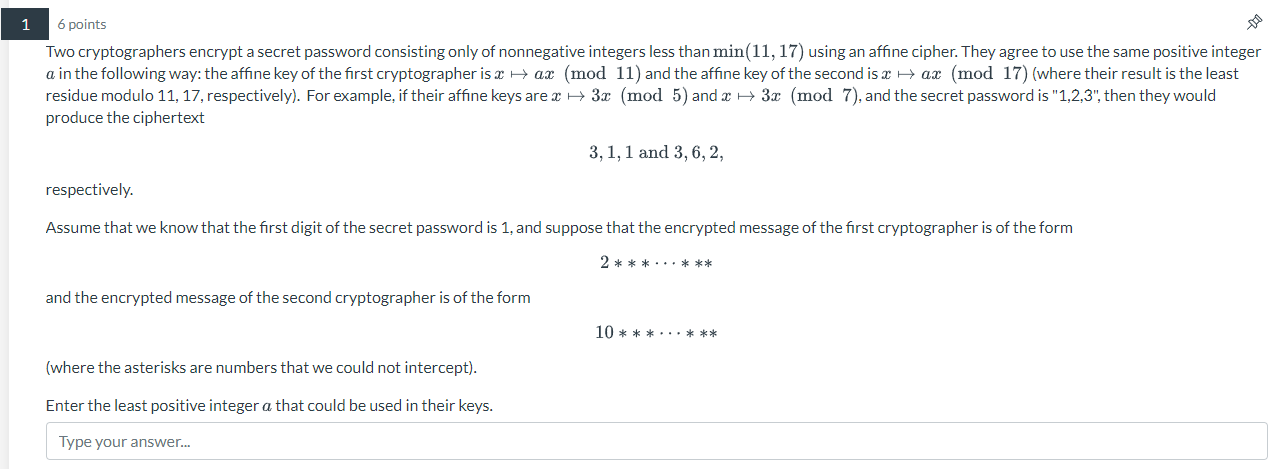
1 6 points Two cryptographers encrypt a secret password consisting only of nonnegative integers less than min (11, 17) using an affine cipher. They agree to use the same positive integer a in the following way: the affine key of the first cryptographer is ax (mod 11) and the affine key of the second is xax (mod 17) (where their result is the least residue modulo 11, 17, respectively). For example, if their affine keys are 3x (mod 5) and x3x (mod 7), and the secret password is "1,2,3", then they would produce the ciphertext respectively. Assume that we know that the first digit of the secret password is 1, and suppose that the encrypted message of the first cryptographer is of the form 2***... *** and the encrypted message of the second cryptographer is of the form 3, 1, 1 and 3, 6, 2, (where the asterisks are numbers that we could not intercept). Enter the least positive integer a that could be used in their keys. Type your answer... 10***... *** 1 6 points Two cryptographers encrypt a secret password consisting only of nonnegative integers less than min(11, 17) using an affine cipher. They agree to use the same positive integer a in the following way: the affine key of the first cryptographer is ax (mod 11) and the affine key of the second is xax (mod 17) (where their result is the least residue modulo 11, 17, respectively). For example, if their affine keys are 3x (mod 5) and x3x (mod 7), and the secret password is "1,2,3", then they would produce the ciphertext respectively. Assume that we know that the first digit of the secret password is 1, and suppose that the encrypted message of the first cryptographer is of the form 2***... *** and the encrypted message of the second cryptographer is of the form 3, 1, 1 and 3, 6, 2, (where the asterisks are numbers that we could not intercept). Enter the least positive integer a that could be used in their keys. Type your answer... 10***... ***
Step by Step Solution
3.46 Rating (156 Votes )
There are 3 Steps involved in it
From the problem we know that two cryptographers are using an affine cipher where the encryption function is x mapsto ax mod m and that they have agre... View full answer

Get step-by-step solutions from verified subject matter experts


