Question: 1. (8 pts) Pipelined network protocols are used every day by web browsers. a. Describe how pipelining and window size are related? b. Describe in
 1. (8 pts) Pipelined network protocols are used every day by web browsers.
1. (8 pts) Pipelined network protocols are used every day by web browsers.
a. Describe how pipelining and window size are related?
b. Describe in words why longer RTTs on a high capacity network link, (over 1000 Mbps), will hinder a reliable data transfer protocol?
2. (10 pts) Suppose four large ftp file transfers are established over a 6 Mbps WAN link. The only connections over this link are these four ftp sessions. The transmissions of the files start at the same time.
a. What approximate transmission rate will be given to each connection?
Now suppose there are two ftp file streams between two different clients and two different servers established at the same exact time over the same link. One stream is using a 1460 byte segment size the other a 576 byte segment size. Assume there are no drops and both streams are using a standard TCP and IP header. Assume both ftp streams are copying the same 3 MiB file (using the binary MB unit).
a. How many segments will be generated by the stream that is using the 1460 byte segment size?
b. How many bytes of the file will be in the last segment?
c. How many segments will be generated by the stream that is using the 576 byte segment size?
d. How many bytes of the file will be in the last segment of the second stream?
3. (4 pts) When developing a reliable data transfer protocol, why is it necessary to introduce timers?
4. (8 pts) The TCP protocol uses sequence numbers.
a. What does the value of a TCP sequence number represent?
b. Provide three reasons why sequence numbers are required in TCP?
5. (12 points) Suppose client PC named X initiates a telnet session to a server called S. At the same time a laptop client named Y initiates a telnet session to server S also. Provide possible source and destination port numbers for:
a. The segments sent from X to S
b. The segments sent from Y to S
c. The segments sent from S to X
d. The segments sent from S to Y
e. If X and Y are different hosts is it possible for them to both use the same source port number?
f. If X and Y are the same host, is it possible for them to both user the same source port number?
6. (8 pts) Host A and B are directly connected using a 1000 Mbps link that many other hosts use to transport data. Host A is sending Host B an enormous file over the 1000 Mbps link. Host A can send at a rate of 100 Mbps, but host B can receive data at a maximum rate of 50 Mbps. After a few seconds, Host A receives two ACKs with duplicate values from Host B. The value for the rwnd field in the first ACK is 4380 and 5840 in the second ACK.
a. What can you deduce about the reason Host A is receiving duplicate ACKs?
b. Why did the rwnd field increase?
7. (4 pts) Suppose a process in host C has a UDP socket with port number 6789. Suppose both host A and host B each send a UDP segment to host C with destination port number 6789.
a. Will both of these segments be directed to same socket at host C?
b. If so, how will the process at host C know that these two segments originated from two different hosts?
8. (4 pts) How many networked processes could theoretically be running on a host at once?
9. (6 pts) Consider a TCP connection between host B and server C. Suppose that the TCP segments traveling from host B to server C have source port number 2345 and destination port number 443.
a. What are the source and destination port numbers for the segments traveling from host C to host B?
b. What can you deduce about server C? What kind of server is it?
10. (8 pts) The text covers the saw tooth behavior that occurs between a sender and a receiver?
a. What protocol is associated with this behavior?
b. What specific algorithm is associated with saw tooth behavior?
11. (8 pts) Concerning methods for controlling congestion on a network.
a. What are the 2 approaches to congested control?
b. List a network technology or protocol covered in the textbook that uses the congestion control approaches you listed in part a.
12. (4 pts) Examine the tcp segment header. The flag field contains 9 bits in the segment structure.
a. What does the last bit, (reading the bits from left to right), signify?
b. When is it used?
13. (4 pts) Refer to page 257 in the text.
a. What portion of the tcp session is used as an attack?
b. What is the purpose of a SYN cookie?
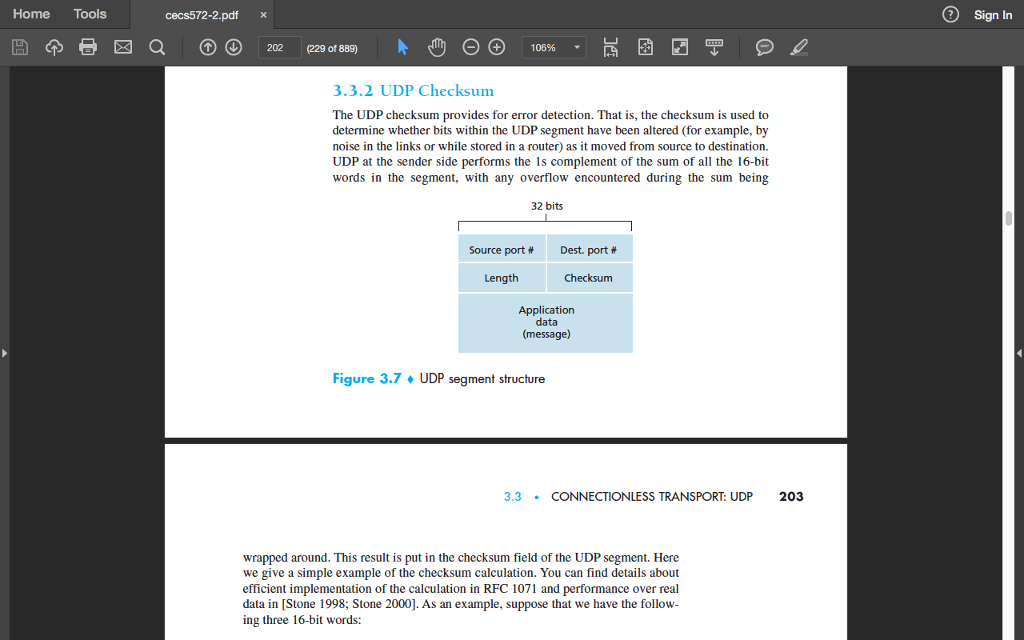
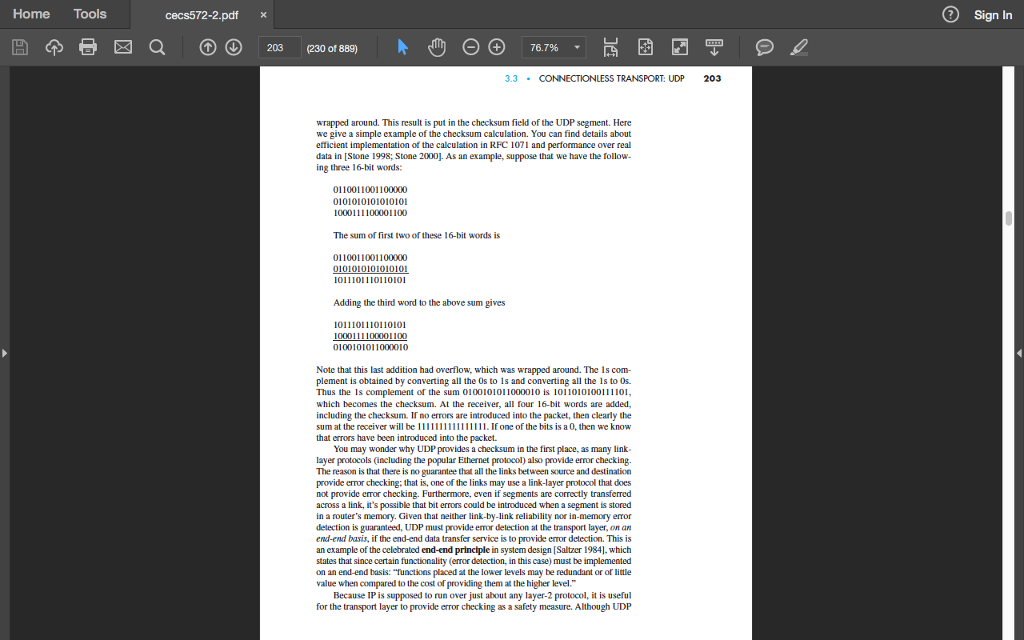
14. (12 total pts) Refer to section 3.3.2 in the textbook that starts on page 202-203 (attached screenshot above) to help you with this question. Answer questions a through d (the values used in the text book are 16 bits long, but 8 bit sequences will be easier to work with for this question)
a. Add these two 8 bit integers together and provide their sum in both binary and decimal:
0011 0111
0101 0011
b. What is the 1 complement of the binary number: 0000 1111 ?
c. Compute the checksum for the UDP segment with these 8 bit values:
0101 0111 Src port
0111 0001 Dst port
0001 1000 length
d. A receiver examines a UDP segment with the following 8 bit values. Will the receiver drop this packet?
0101 1000 Src port
0001 1100 Dst port
1100 1101 length
1011 1101 chksum
e. (4 pts) Validate your answer by showing your work. typed
cecs572-2.pdfx Sign In Home Tools (229 of 889) 106% 3.3.2 UDP Checksum The UDP checksum provides for error detection. That is, the checksum is used to determine whether bits within the UDP segment have been altered (for example, by noise in the links or while stored in a router) as it moved from source to destination. UDP at the sender side performs the Is complement of the sum of all the 16-bit words in the segment, with any overflow encountered during the sum being 32 bits Source port # Dest. port # Length Checksum Application data (message) Figure 3.7 UDP segment structure 3.3CONNECTIONLESS TRANSPORT: UDP 203 wrapped around. This result is put in the checksum field of the UDP segment. Here we give a simple example of the checksum calculation. You can find details about efficient implementation of the calculation in RFC 1071 and performance over real data in [Stone 1998; Stone 2000]. As an example, suppose that we have the follow ing three 16-bit words: cecs572-2.pdfx Sign In Home Tools (229 of 889) 106% 3.3.2 UDP Checksum The UDP checksum provides for error detection. That is, the checksum is used to determine whether bits within the UDP segment have been altered (for example, by noise in the links or while stored in a router) as it moved from source to destination. UDP at the sender side performs the Is complement of the sum of all the 16-bit words in the segment, with any overflow encountered during the sum being 32 bits Source port # Dest. port # Length Checksum Application data (message) Figure 3.7 UDP segment structure 3.3CONNECTIONLESS TRANSPORT: UDP 203 wrapped around. This result is put in the checksum field of the UDP segment. Here we give a simple example of the checksum calculation. You can find details about efficient implementation of the calculation in RFC 1071 and performance over real data in [Stone 1998; Stone 2000]. As an example, suppose that we have the follow ing three 16-bit words
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


