Question
1. Consider the following packet-filtering firewall. Suppose Alice wants to disallow access to her network 222.22.0.0/16 from the public Internet (rule R3 in the first
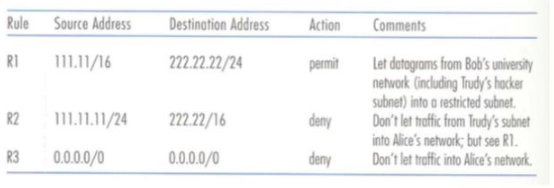
1. Consider the following packet-filtering firewall. Suppose Alice wants to disallow access to her network 222.22.0.0/16 from the public Internet (rule R3 in the first table below). Alice is collaborating with Bob and his colleagues, who are at a university, and so Alice want to let users from Bob's university (whose network address is 111.11/16) access a specific subnet, 222.22.22/24, within her company's network (rule R1 below). Alice knows that Trudy, a well-known hacker, is in Bob's university and that Trudy's subnet, 111.11.11/24, is an insecure hacker haven. So Alice doesn't want any traffic from 111.11.11/24 entering anywhere into her network (rule R2) except into the special subnet 222.22.22/24 (allowed under rule R1; this exception is the important difference from our example in class). Alice's packet-filtering rules are summarized in the table below.
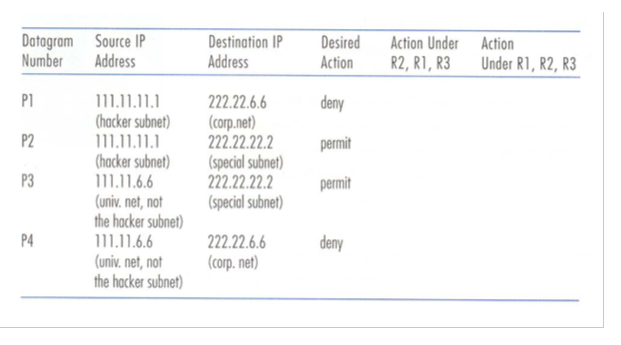
2. Fill in the table above for the actions taken for this scenario under ordering R1, R2, R3, and under ordering R2, R1, R3.
3. For packets P1, P2, P3, and P4, what would be the result of removing rule R2? Hint 1: Packet-filtering operates by sequentially checking filtering rules against the datagram being inspected; the first rule matching the datagram determines the action taken. Hint 2: the ordering of firewall rules is important. Clearly, careful thought is required-- imagine the difficulties involved in specifying firewalls with thousands of rules! One might be tempted to think that applying more specific rules first might always avoid unanticipated or unwanted behavior arising from ordering issues. However, we'll see in this homework problem that this is not necessarily the case. Hint 3: 222.22.0.0/16, where the "/16" notation, sometimes known as a network mask, indicates that the leftmost 16 bits of the 32-bit quantity define the network address. These leftmost bits that define the network address are also often referred to as the network prefix. Any hosts attached to the 222.22.0.0/16 network would be required to have an address of the form 222.22.xxx.xxx. So, 111.11/16 is a network with the leftmost
16 bits network mask, 222.22.22/24 is a network with the leftmost 24 bits network mask, and 111.11.11/24 is also a network with the leftmost 24 bits network mask.
Rule Source Address Destinotion Address Action Comments RI 111.11/16 222.22 22/24 permit let dotogoms from Bob's university network (including Trudy's hocker subnet) into orestricted subnet. R2 111.11.1 1/24 222.22/16 deny Don't let toffic from Trudy's subnet intoAlice's network but see R1. R3 0.0.0.0/0 0.0.0.0/0 deny Don't let traffic into Alice's network. Rule Source Address Destinotion Address Action Comments RI 111.11/16 222.22 22/24 permit let dotogoms from Bob's university network (including Trudy's hocker subnet) into orestricted subnet. R2 111.11.1 1/24 222.22/16 deny Don't let toffic from Trudy's subnet intoAlice's network but see R1. R3 0.0.0.0/0 0.0.0.0/0 deny Don't let traffic into Alice's network
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


