Answered step by step
Verified Expert Solution
Question
1 Approved Answer
1. Determine if the ITGC listed is a preventive or a detective and corrective control. ITGC Changes to the IT application are tested by
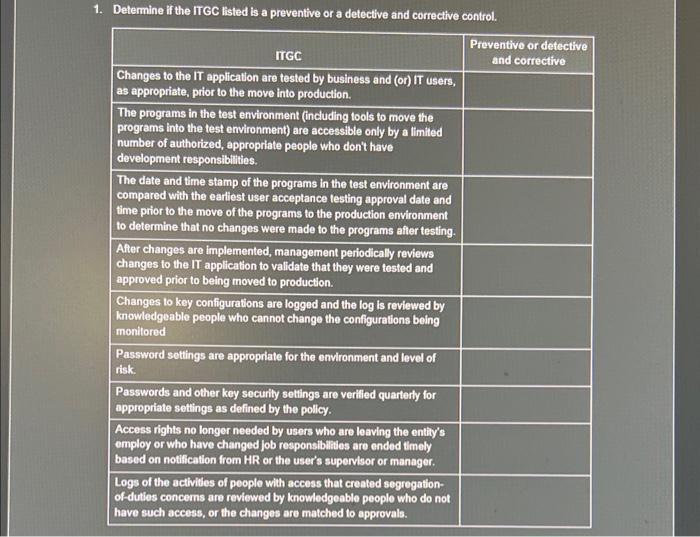
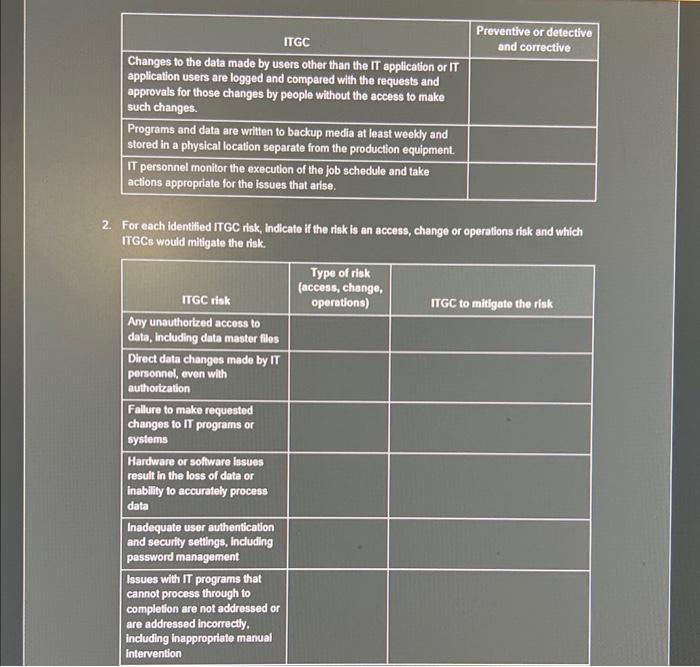
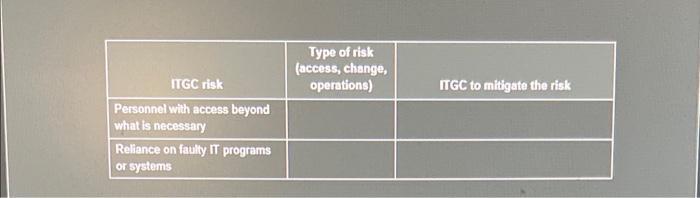
1. Determine if the ITGC listed is a preventive or a detective and corrective control. ITGC Changes to the IT application are tested by business and (or) IT users, as appropriate, prior to the move into production. The programs in the test environment (including tools to move the programs into the test environment) are accessible only by a limited number of authorized, appropriate people who don't have development responsibilities. The date and time stamp of the programs in the test environment are compared with the earliest user acceptance testing approval date and time prior to the move of the programs to the production environment to determine that no changes were made to the programs after testing. After changes are implemented, management periodically reviews changes to the IT application to validate that they were tested and approved prior to being moved to production. Changes to key configurations are logged and the log is reviewed by knowledgeable people who cannot change the configurations being monitored Password settings are appropriate for the environment and level of risk. Passwords and other key security settings are verified quarterly for appropriate settings as defined by the policy. Access rights no longer needed by users who are leaving the entity's employ or who have changed job responsibilities are ended timely based on notification from HR or the user's supervisor or manager. Logs of the activities of people with access that created segregation- of-duties concerns are reviewed by knowledgeable people who do not have such access, or the changes are matched to approvals. Preventive or detective and corrective ITGC Changes to the data made by users other than the IT application or IT application users are logged and compared with the requests and approvals for those changes by people without the access to make such changes. Programs and data are written to backup media at least weekly and stored in a physical location separate from the production equipment. IT personnel monitor the execution of the job schedule and take actions appropriate for the issues that arise. 2. For each identified ITGC risk, indicate if the risk is an access, change or operations risk and which ITGCS would mitigate the risk. ITGC risk Any unauthorized access to data, including data master files Direct data changes made by IT personnel, even with authorization Failure to make requested changes to IT programs or systems Hardware or software issues result in the loss of data or inability to accurately process data Inadequate user authentication and security settings, including password management Issues with IT programs that cannot process through to completion are not addressed or are addressed incorrectly. including Inappropriate manual intervention Preventive or detective and corrective Type of risk (access, change, operations) ITGC to mitigate the risk ITGC risk Personnel with access beyond what is necessary Reliance on faulty IT programs or systems Type of risk (access, change, operations) ITGC to mitigate the risk
Step by Step Solution
★★★★★
3.47 Rating (163 Votes )
There are 3 Steps involved in it
Step: 1
Answer First the necessary response 1 manage the process of transformation 2 ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


