Answered step by step
Verified Expert Solution
Question
1 Approved Answer
1. Dr. Who decides to use public-key cryptography in his security class to report the midterm grades. Each student is asked to use 2048-bit
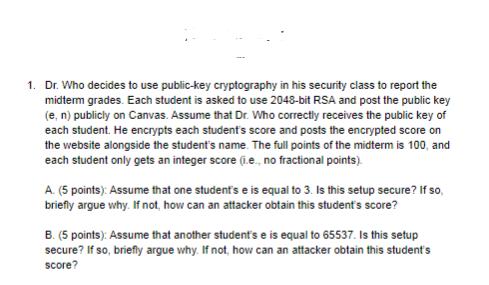
1. Dr. Who decides to use public-key cryptography in his security class to report the midterm grades. Each student is asked to use 2048-bit RSA and post the public key (e, n) publicly on Canvas. Assume that Dr. Who correctly receives the public key of each student. He encrypts each student's score and posts the encrypted score on the website alongside the student's name. The full points of the midterm is 100, and each student only gets an integer score (i.e. no fractional points) A. (5 points): Assume that one student's e is equal to 3. Is this setup secure? If so, briefly argue why. If not, how can an attacker obtain this student's score? B. (5 points): Assume that another student's e is equal to 65537. Is this setup secure? If so, briefly argue why. If not, how can an attacker obtain this student's score?
Step by Step Solution
There are 3 Steps involved in it
Step: 1
A Scenario with e3 If one student uses an RSA public key with the public exponent e equal to 3 the setup is not secure under certain conditions An att...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


