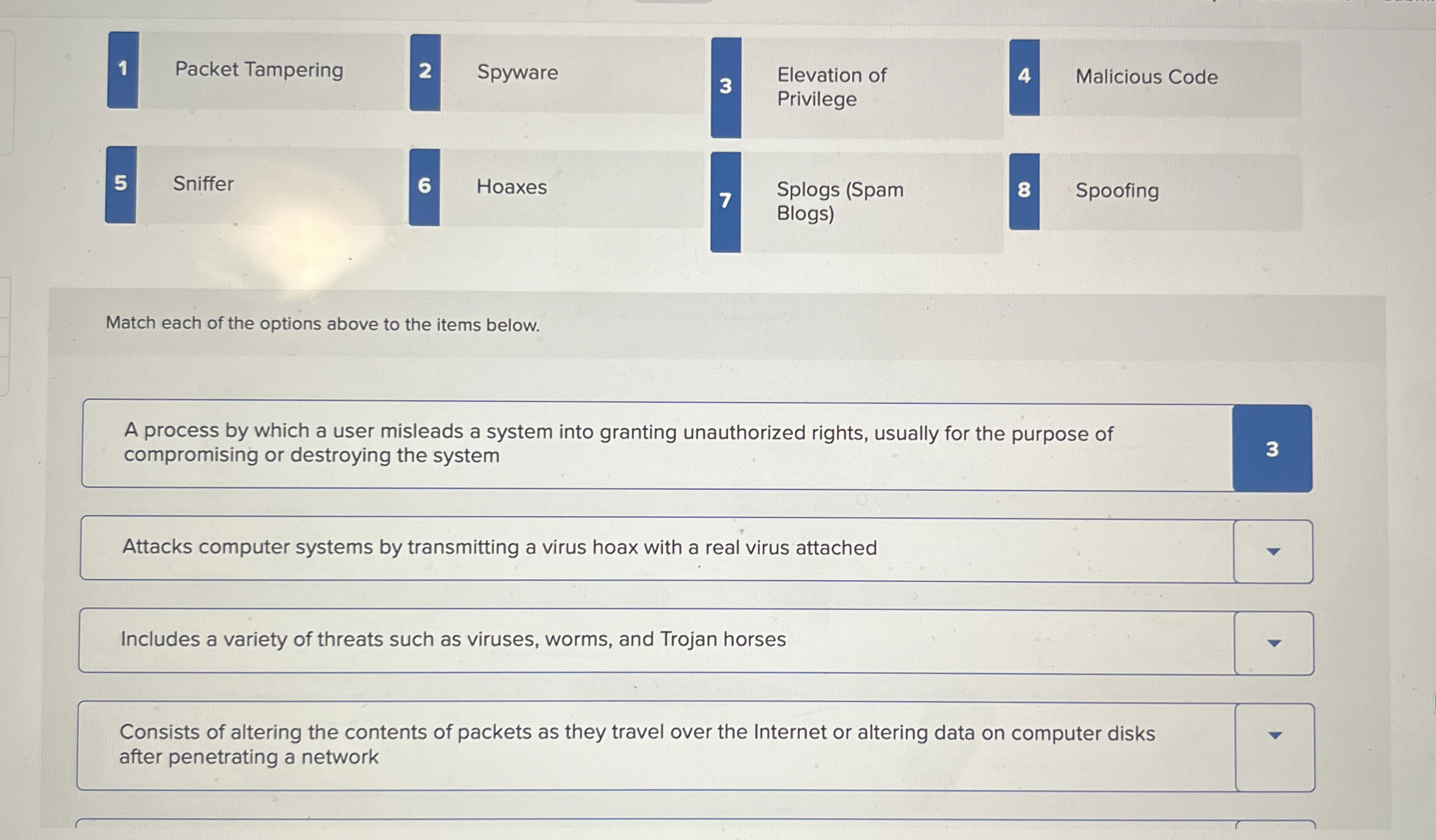
Question: 1 Packet Tampering 2 Spyware 3 Elevation of 4 Malicious Code 5 Sniffer 6 Hoaxes 7 Splogs ( Spam 8 Spoofing Match each of the
Packet Tampering
Spyware
Elevation of
Malicious Code
Sniffer
Hoaxes
Splogs Spam
Spoofing
Match each of the options above to the items below.
A process by which a user misleads a system into granting unauthorized rights, usually for the purpose of compromising or destroying the system
Attacks computer systems by transmitting a virus hoax with a real virus attached
Includes a variety of threats such as viruses, worms, and Trojan horses
Consists of altering the contents of packets as they travel over the Internet or altering data on computer disks after penetrating a network
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


