Answered step by step
Verified Expert Solution
Question
1 Approved Answer
1. The home position is at (240, 360, 180) from the origin. The origin lies on the top of the part as shown in
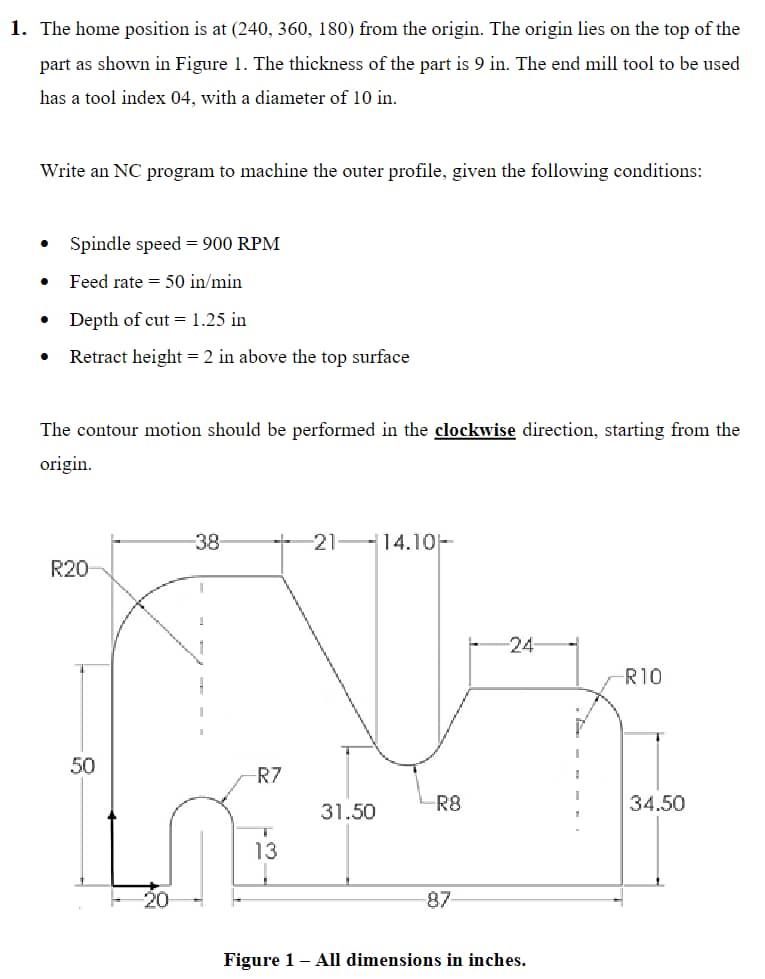
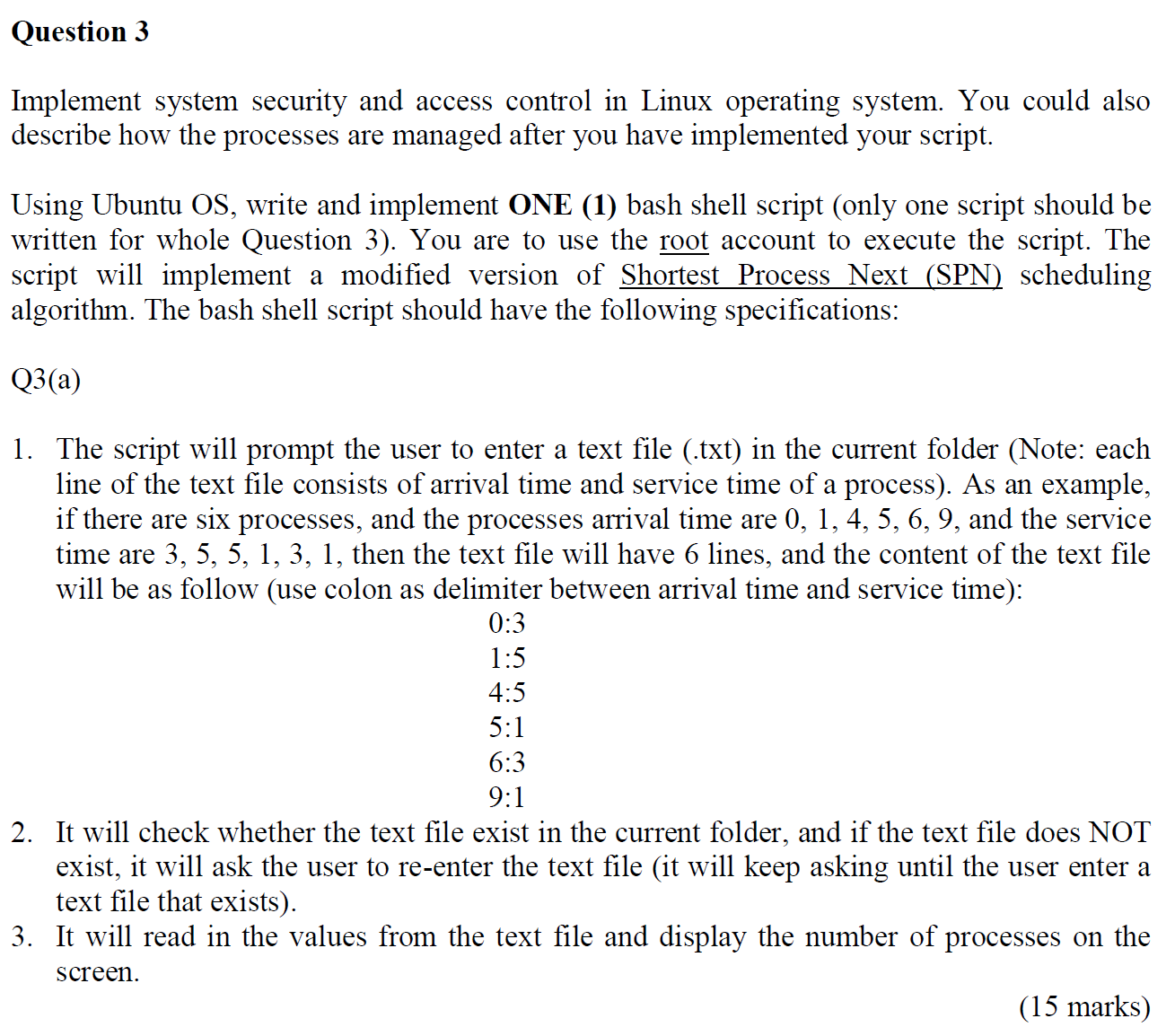

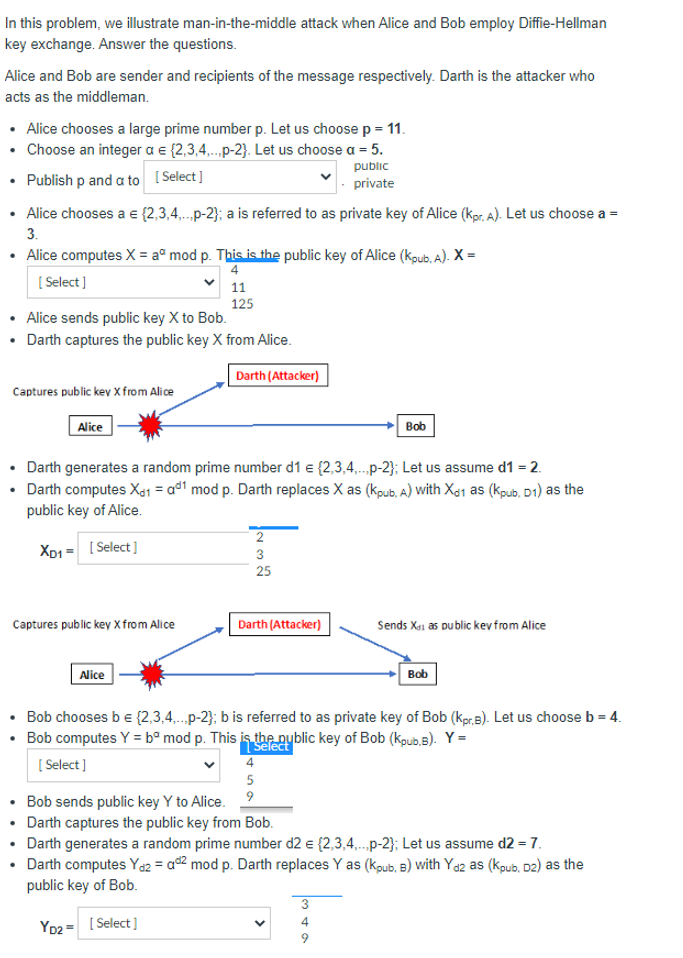
1. The home position is at (240, 360, 180) from the origin. The origin lies on the top of the part as shown in Figure 1. The thickness of the part is 9 in. The end mill tool to be used has a tool index 04, with a diameter of 10 in. Write an NC program to machine the outer profile, given the following conditions: Spindle speed 900 RPM Feed rate 50 in/min Depth of cut = 1.25 in Retract height = 2 in above the top surface The contour motion should be performed in the clockwise direction, starting from the origin. R20 50 -38 -R7 13 -21-14.10- 31.50 R8 87 -24- Figure 1 - All dimensions in inches. I -R10 34.50 Question 3 Implement system security and access control in Linux operating system. You could also describe how the processes are managed after you have implemented your script. Using Ubuntu OS, write and implement ONE (1) bash shell script (only one script should be written for whole Question 3). You are to use the root account to execute the script. The script will implement a modified version of Shortest Process Next (SPN) scheduling algorithm. The bash shell script should have the following specifications: Q3(a) 1. The script will prompt the user to enter a text file (.txt) in the current folder (Note: each line of the text file consists of arrival time and service time of a process). As an example, if there are six processes, and the processes arrival time are 0, 1, 4, 5, 6, 9, and the service time are 3, 5, 5, 1, 3, 1, then the text file will have 6 lines, and the content of the text file will be as follow (use colon as delimiter between arrival time and service time): 0:3 1:5 4:5 5:1 6:3 9:1 2. It will check whether the text file exist in the current folder, and if the text file does NOT exist, it will ask the user to re-enter the text file (it will keep asking until the user enter a text file that exists). 3. It will read in the values from the text file and display the number of processes on the screen. (15 marks) Q3(b) 1. It will then calculate the finish time for each process and display each process finish time on the screen (the time needs to be displayed in ascending order). 2. It will also calculate the turnaround time for each process and display each process turnaround time on the screen (the time needs to be displayed in the order as correspond to point 1). 3. The average turnaround time for all processes will then be appended to a file "avetime.txt" (note that the average turnaround time should NOT be displayed on the screen). (15 marks) Q3(c) 1. 2. The following will then be changed: Owner and group of "avetime.txt" to root user. Permissions of "avetime.txt" to the owner can read, write and execute, group can read and execute, and others can read. Validation check needs to be done in the bash shell script whenever possible (e.g. when inputting the text file, the script should check whether the text file is empty or not). (10 marks) Q3 (d) A documentation (with appropriate screenshots and explanations) needs to be produced on the execution of the bash shell script with different conditions (e.g. text file existed, text file does not exist, etc.). Necessary checking needs to be done (e.g. check that the permissions of the file "avetime.txt" has changed, etc.). Appropriate comments should be added in the script to make it easier to understand. (15 marks) In this problem, we illustrate man-in-the-middle attack when Alice and Bob employ Diffie-Hellman key exchange. Answer the questions. Alice and Bob are sender and recipients of the message respectively. Darth is the attacker who acts as the middleman. Alice chooses a large prime number p. Let us choose p = 11. Choose an integer a = {2,3,4,...p-2). Let us choose a = 5. public Publish p and a to [Select] private Alice chooses a = {2,3,4,..,p-2); a is referred to as private key of Alice (Kpr. A). Let us choose a = 3. Alice computes X = a mod p. This is the public key of Alice (kpub. A). X = 4 [Select] Alice sends public key X to Bob. Darth captures the public key X from Alice. Captures public key X from Alice Alice 11 125 Captures public key X from Alice Alice Darth (Attacker) Darth generates a random prime number d1 = {2,3,4,..,p-2}; Let us assume d1 = 2. Darth computes X1 = a mod p. Darth replaces X as (kpub. A) with Xd1 as (kpub. D1) as the public key of Alice. XD1 = [Select] 2 3 25 Darth (Attacker) 5 9 Bob sends public key Y to Alice. Darth captures the public key from Bob. Bob chooses b = {2,3,4,...,p-2); b is referred to as private key of Bob (kpr.B). Let us choose b = 4. Bob computes Y = ba mod p. This is the public key of Bob (kpub.B). Y = [Select] Bob V 3 4 Sends Xa as public key from Alice Darth generates a random prime number d2 = {2,3,4,...p-2}; Let us assume d2 = 7. Darth computes Yd2 = qd mod p. Darth replaces Y as (Kpub, B) with Yd2 as (Kpub, D2) as the public key of Bob. YD2 = [Select] 9 Bob
Step by Step Solution
There are 3 Steps involved in it
Step: 1
G17 G21 G40 G49 G80 G90 M3 S900 G54 T04 M06 G43 H04 G00 X240 Y360 Z180 G01 Z125 F500 G02 X221 Y114 R020 F500 X224 Y124 X231 Y150 X240 Y187 X249 Y224 X...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


