Question
1. Which of the following is not one of the main traits that defines Big Data: Question options: A Multiple venues of data relationships B
1. Which of the following is not one of the main traits that defines Big Data:
Question options:
| A | Multiple venues of data relationships |
| B | Diverse variety in data formats |
| C | High velocity in data flow |
| D | Large volumes of digitally stored data |
2.
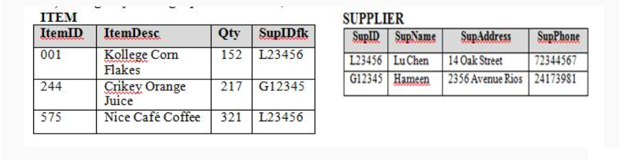
For the following tables, which SQL command would: List the Supplier Name and Item Description [ItemDesc] for each item the supermarket sales.
Question options:
| A | SELECT SupName, ItemDesc FROM ITEM JOIN SUPPLIER ON supIDfk = supID |
| B | SELECT * from ITEM, SUPPLIER |
| C | LIST SupName, ItemDesc FROM ITEM, SUPPLIER where supIDfk = supID |
| D | SELECT SupName, ItemDesc FROM ITEM, SUPPLIER |
3. ______________________ is a popular technology designed to efficiently process large amounts of diverse types of data. Words associated with this technology include 'Pig', 'Hive', 'Zookeeper'.
Question options:
| A | data warehousing |
| B | hadoop |
| C | high speed SQL processing |
| D | data mining |
4.
NoSQL databases are predicted to overtake relational database systems in the next few years.
Question options:
|
| True |
|
| False |
5.
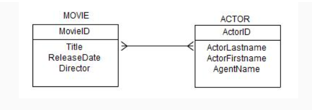
Choose the answer that best maps the following ERD to tables.
Question options:
| A | MOVIE(MovieID,Title,ReleaseDate,Director) ACTOR(ActorID,ActorLastname,ActorFirstName,AgentName) INTERSECTION(MovieID,ActorID) |
| B | MOVIE(MovieID,Title,ReleaseDate,Director) ACTOR(ActorID,ActorLastname,ActorFirstName,AgentName,MovieID) |
| C | MOVIE(MovieID,Title,ReleaseDate,Director,ActorID) ACTOR(ActorID,ActorLastname,ActorFirstName,AgentName) INTERSECTION(MovieID,ActorID,ActorLastName,ReleaseDate) |
| D | MOVIEINFO(MovieID, Title,ReleaseDate,Director, ActorLastname,ActorFirstName,AgentName) |
| E | MOVIE(MovieID,Title,ReleaseDate,Director,ActorID) ACTOR(ActorID,ActorLastname,ActorFirstName,AgentName) |
6.
When a transaction functions in such a way that either all of the transaction actions are completed or none of them will be, the transaction is said to be:
Question options:
| A | consistent |
| B | atomic |
| C | locked |
| D | logical |
| E | isolated |
7.
What concurrent processing problem occurs when a transaction reads a changed record that has not been committed to the database?
Question options:
| A | Unlocked reads |
| B | Serialized reads |
| C | Dirty reads |
| D | Nonrepeatable reads |
| E | Phantom reads |
8.
The purpose of concurrency control is to:
Question options:
| A | Ensure that no two SQL statements are executed at the same time. |
|
|
|
| B | Ensure that every input form has a corresponding output report. |
| C | Ensure that one user's work does not interfere with another's. |
| D | Ensure that resource locking is always used. |
9.
Serializable prevents which of the following?
Question options:
| A | Lost-update |
| B | Phantom read |
| C | Dirty read |
| D | Nonrepeatable read |
| E | All of the above |
10.
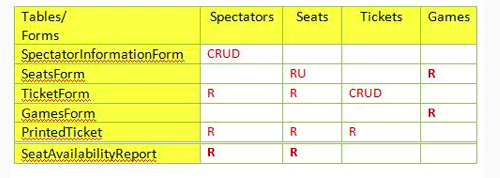
Given the following security matrix, the GAMES table is accessed by how many forms?
Question options:
| A | None |
| B | 1 |
| C | 2 |
| D | 3 |
| E | All tables |
11.
SELECT ALL THAT APPLY: Who is responsible for insuring the confidentiality of data in the Kennesaw Owlexpress database? Remember: SELECT ALL THAT APPLY.
Question options:
| A | Students |
| B | Database Administrators |
| C | Faculty |
| D | Database programmers |
12.
What concurrent processing problem occurs when a transaction rereads data and finds new rows that were inserted by a different transaction since the prior read?
Question options:
| A | Unlocked reads |
| B | Nonrepeatable reads |
| C | Phantom reads |
| D | Dirty reads |
| E | Serialized reads |
13.
Row level security is often implemented through the use of:
Question options:
| A | SQL views |
| B | Prepared Queries |
| C | User profiles and assigned processing rights |
| D | Username and password |
14.
HIPPA is related to:
Question options:
| A | Police records |
| B | DNA databases |
| C | Bank records |
| D | healthcare data |
15.
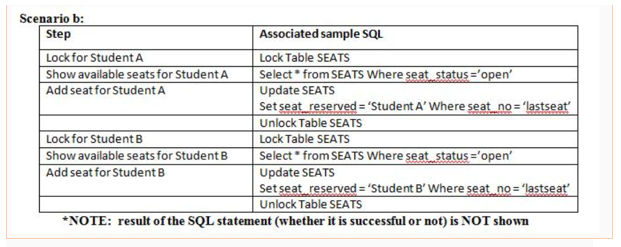
It is the KSU Fighting Owls football team's inaugural season and season tickets are in high demand. In fact, only one season ticket remains. Student A and Student B both want season tickets. Given the following, who gets the ticket?
Question options:
| A | Student A and Student B both get the ticket |
| B | Not enough information to tell. |
| C | Student B |
| D | Student A |
16.
SQL injections occur most often because of stolen passwords.
Question options:
| A | True |
| B | False |
17.
Which of the following about deadlocks is untrue?
Question options:
| A | Most database systems automatically check for and resolve deadlocks. |
| B | Deadlocks occur when two transactions are each waiting for access to a table that the other one has locked. |
| C | Deadlocks rarely happen. |
| D | Serialized locking of all resources utilized by a transaction helps to prevent deadlocks. |
18.
Which method can often tell if the backend of a web form is using SQL?
Question options:
| A | Adding /sql onto the end of the Web form URL |
| B | Entering /sql?=' onto the end of the Web form URL |
| C | Entering a single quote into a username entry field on a web form |
| D | Entering 1=1 into a username entry field on a web form |
19.
Database inference is easily solved by:
Question options:
| A | Allowing users only access to aggregated data results |
| B | White listing |
| C | Prepared queries |
| D | There is not an easily implemented technology solution to prevent database inference |
20.
The most common form of database security is implemented by:
Question options:
| A | Pessimistic record locking |
| B | Table encryption |
| C | Complex SQL processing |
| D | Username/password |
21.
SELECT ALL THAT APPLY. Relationships when mapped to tables are expressed by: Remember: SELECT ALL THAT APPLY.
Question options:
| A | foreign keys |
| B | duplicate columns |
| C | data types |
| D | primary keys |
22.
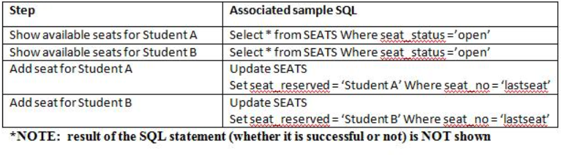
It is the KSU Fighting Owls football team's inaugural season and season tickets are in high demand. In fact, only one season ticket remains. Student A and Student B both want season tickets. From the following scenario, who gets the ticket?
Question options:
| A | Both Student A and student B get the ticket |
| B | Student B |
| C | Student A |
| D | Not enough information to tell |
23.
The recommended procedure for preventing SQL injections is:
Question options:
| A | Prepared queries |
| B | Black listing |
| C | SQL mapping |
| D | White listing |
24.
The process of tracking who accesses a database and which resources are accessed is called _________________________ and the information obtained from this tracking is recorded in a ____________________.
Question options:
| A | auditing, log file |
| B | auditing, archive file |
| C | tracking, log file |
| D | tracking, archive file |
25.
Another name for a transaction is:
Question options:
| A | SQL command |
| B | Concurrency control |
| C | Logical Unit of Work |
| D | Concurrent user action |
26.
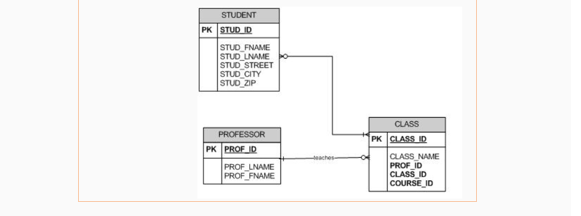
| A | A professor may teach one or more classes but a student must take one or more classes. A class must be taught by one professor but a class may or may not have students. |
| B | A professor is required to teach at least one class and students must take at least one class. |
| C | A professor must teach one or more classes and a class must be taught by one professor. A student may take one or more classes but a class must have one or more students. |
| D | A professor may teach one or more classes and a student may take one or more classes. A class must be taught by one professor and a class must have at least one student. |
27.
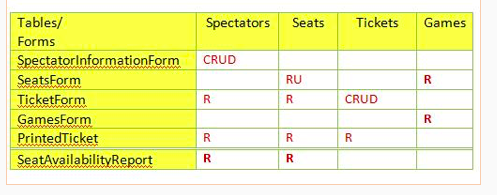
Given the following Security matrix, which is the most most complex form to implement?
Question options:
| A | PrintedTicket |
| B | TicketForm |
| C | SpectatorInformationForm |
| D | SeatsForm |
28.
Normalization answers which question:
Question options:
| A | How many candidate keys are needed? |
| B | What should the primary key be? |
| C | How many tables? |
| D | What is the cardinality? |
| E | What are the functional dependencies? |
29.
Which locking methods employs the use of making a copy of the original records and checking for changes to that record before committing an update?
Question options:
| A | pessimistic locking |
| B | optmistic locking |
| C | lost-update |
| D | deadlock |
30.
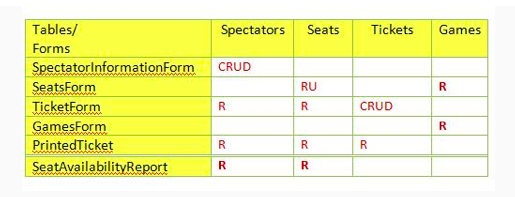
Given the following security matrix, which form(s) are not able to alter table data for any table?
Question options:
| A | SeatsForm,TicketForm,GamesForm |
| B | GamesForm, PrintedTicket , SeatAvailabilityReport |
| C | SeatsForm, SeatAvailabilityForm |
| D | TicketForm |
31.
The best method of providing access to end users to data contained in a database is:
Question options:
| A | A multi-layer architecture composed of a middle layer that communicates with the database |
| B | a Web form connected to the database |
| C | A secure user login to the database system |
| D | A client app that is installed on the end users' PC or other device that establishes an ODBC connection to the database |
32.
A database system crashes and needs to be restored to its state at the time of the crash. A complete backup of the database is done once a day. The crash occurred at 12 noon. The last full backup was done at 4:00 am. The latest full backup is restored. Then _______________________________ is done in a process known as _________________________.
Question options:
| A | reprocessing, roll forward |
| B | recovery, roll forward |
| C | reprocessing, rollback |
| D | recovery, redo |
| E | recovery, rollback |
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


