Question
15. It is the KSU Fighting Owls football team's inaugural season and season tickets are in high demand. In fact, only one season ticket remains.
15.
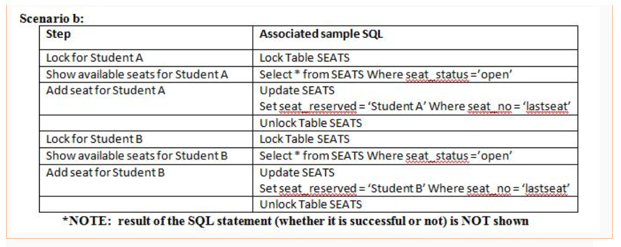
It is the KSU Fighting Owls football team's inaugural season and season tickets are in high demand. In fact, only one season ticket remains. Student A and Student B both want season tickets. Given the following, who gets the ticket?
Question options:
| A | Student A and Student B both get the ticket |
| B | Not enough information to tell. |
| C | Student B |
| D | Student A |
23.
The recommended procedure for preventing SQL injections is:
Question options:
| A | Prepared queries |
| B | Black listing |
| C | SQL mapping |
| D | White listing |
24.
The process of tracking who accesses a database and which resources are accessed is called _________________________ and the information obtained from this tracking is recorded in a ____________________.
Question options:
| A | auditing, log file |
| B | auditing, archive file |
| C | tracking, log file |
| D | tracking, archive file |
25.
Another name for a transaction is:
Question options:
| A | SQL command |
| B | Concurrency control |
| C | Logical Unit of Work |
| D | Concurrent user action |
26.
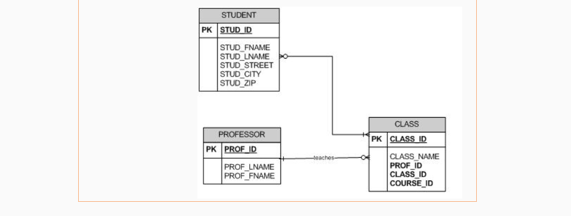
| A | A professor may teach one or more classes but a student must take one or more classes. A class must be taught by one professor but a class may or may not have students. |
| B | A professor is required to teach at least one class and students must take at least one class. |
| C | A professor must teach one or more classes and a class must be taught by one professor. A student may take one or more classes but a class must have one or more students. |
| D | A professor may teach one or more classes and a student may take one or more classes. A class must be taught by one professor and a class must have at least one student. |
27.
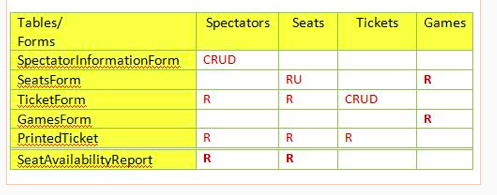
Given the following Security matrix, which is the most most complex form to implement?
Question options:
| A | PrintedTicket |
| B | TicketForm |
| C | SpectatorInformationForm |
| D | SeatsForm |
28.
Normalization answers which question:
Question options:
| A | How many candidate keys are needed? |
| B | What should the primary key be? |
| C | How many tables? |
| D | What is the cardinality? |
| E | What are the functional dependencies? |
29.
Which locking methods employs the use of making a copy of the original records and checking for changes to that record before committing an update?
Question options:
| A | pessimistic locking |
| B | optmistic locking |
| C | lost-update |
| D | deadlock |
30.
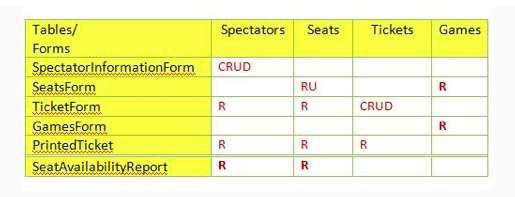
Given the following security matrix, which form(s) are not able to alter table data for any table?
Question options:
| A | SeatsForm,TicketForm,GamesForm |
| B | GamesForm, PrintedTicket , SeatAvailabilityReport |
| C | SeatsForm, SeatAvailabilityForm |
| D | TicketForm |
31.
The best method of providing access to end users to data contained in a database is:
Question options:
| A | A multi-layer architecture composed of a middle layer that communicates with the database |
| B | a Web form connected to the database |
| C | A secure user login to the database system |
| D | A client app that is installed on the end users' PC or other device that establishes an ODBC connection to the database |
32.
A database system crashes and needs to be restored to its state at the time of the crash. A complete backup of the database is done once a day. The crash occurred at 12 noon. The last full backup was done at 4:00 am. The latest full backup is restored. Then _______________________________ is done in a process known as _________________________.
Question options:
| A | reprocessing, roll forward |
| B | recovery, roll forward |
| C | reprocessing, rollback |
| D | recovery, redo |
| E | recovery, rollback |
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


