Answered step by step
Verified Expert Solution
Question
1 Approved Answer
2. 3. 4. A is a collection of interconnected access points with a software protocol structure that enables communication. A. network B. I/O channel





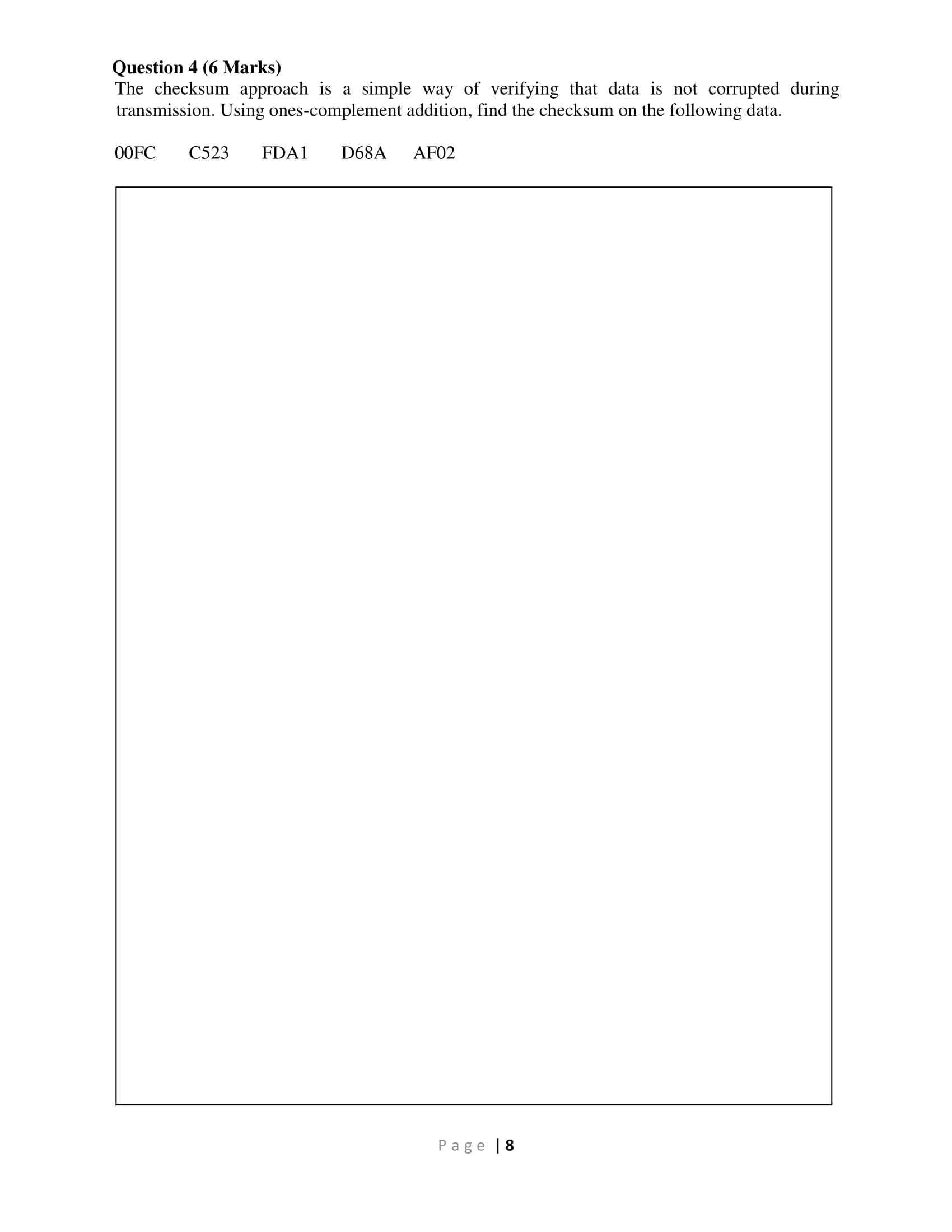



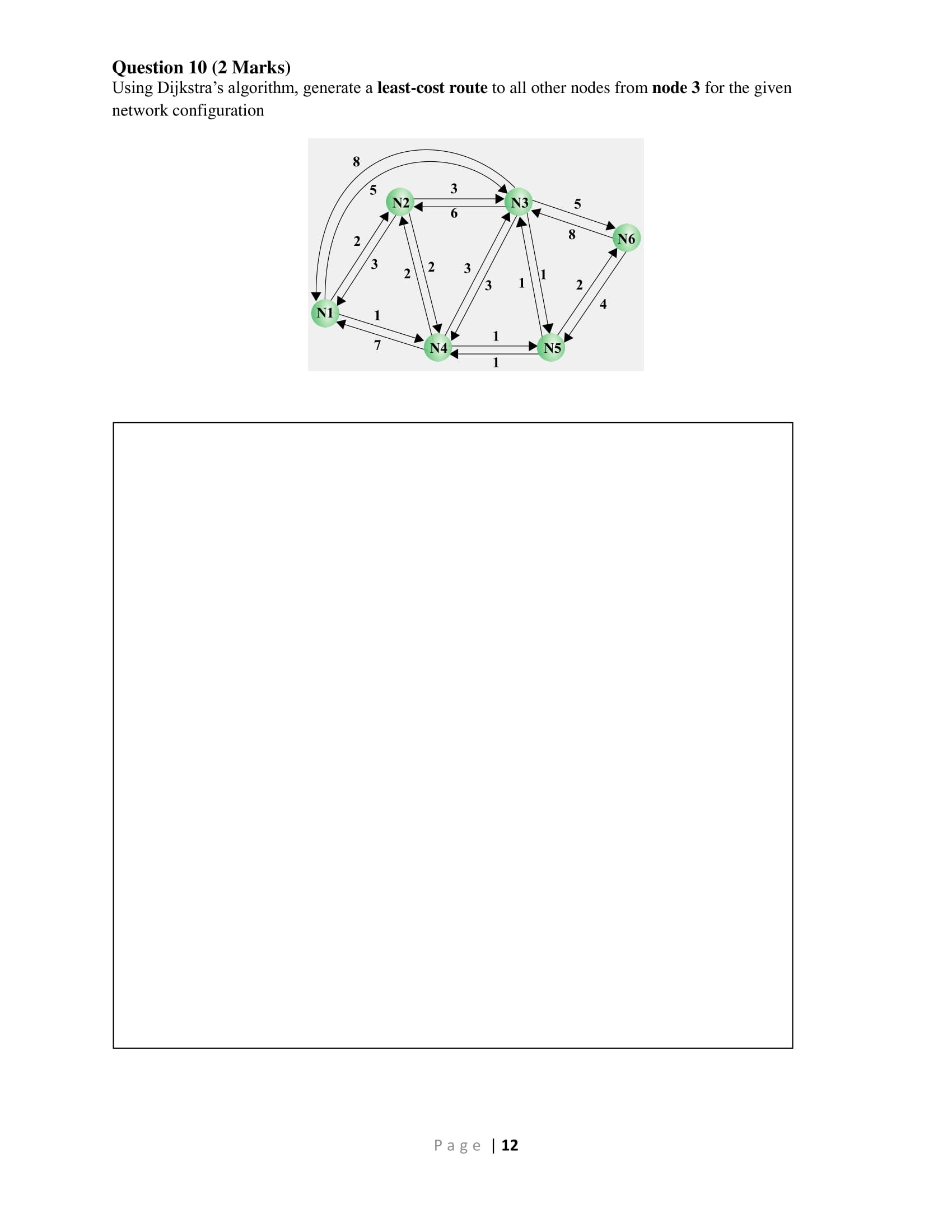
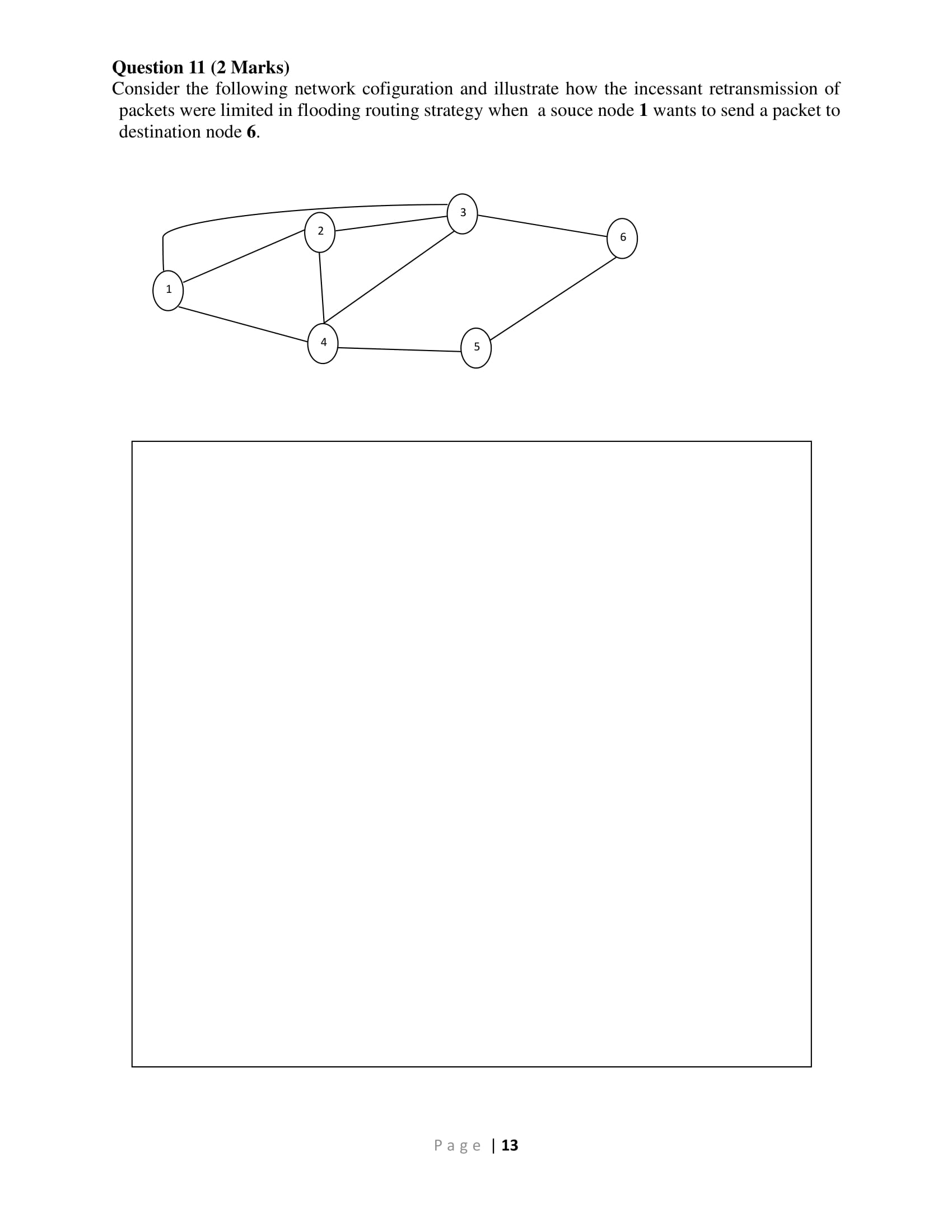
2. 3. 4. A is a collection of interconnected access points with a software protocol structure that enables communication. A. network B. I/O channel C. carrier access station D. Fibre channel If the has to do with the ability of the network to deliver packets via some route in the face of localized failures and overloads. A. correctness B. robustness C. efficiency D. optimality is determined by whether the routing decision is made on a packet or virtual circuit basis. A. Place B. Update timing C. Decision time D. VCC With routing decisions that are made change as conditions on the network change. A. fixed routing B. flooding C. adaptive routing D. random routing 5. A switching center that directly supports subscribers is known as A. a subscriber loop B. a subscriber center C. a branch exchange D. an end office 6. The element represents the functions and hardware needed to connect digital devices such as data processing devices and digital telephones to the network. A. media gateway B. digital switch C. control unit D. network interface Page 2 7. Dynamic use of bandwidth is utilized with A. virtual circuit packet switching and circuit switching B. datagram packet switching and virtual circuit packet switching C. circuit switching and datagram packet switching D. space division switching and circuit switching 8. A A. softswitch B. node C. LAPF D. virtual circuit 9. Circuit switching was developed to handle A. voice B. A/V C. video D. data A. hub B. bridge C. switch D. gateway can convert a stream of digitized voice bits into packets. 10. The simplest approach to interconnecting multiple LANs within an organization is to use a 11. A A. bus B. star C. tree D. ring A. MAC B. LLC C. LAN D. PDU LAN includes a central node to which stations are attached. 12. The specifies the mechanisms for addressing stations across the medium and for controlling the exchange of data between two users. traffic. 13. The IEEE 802.3 standard is known as A. Ethernet B. layer 2 switching C. fibre channel D. subnetworking Page 13 14. Two frames interfering with each other at the receiver so that neither gets through is known as 15. A problem with is that capacity is wasted because the medium will generally remain idle following the end of a transmission, even if there are one or more stations waiting to transmit. A. a collision B. a backlog C. a backoff D. scrambling 16. One of the rules for CSMA/CD states, "after transmitting the jamming signal, wait a random amount of time, then attempt to transmit again". This random amount of time is referred to as the 18. 19. A. p-persistent CSMA B. nonpersistent CSMA C. 1-persistent CSMA D. slotted ALOHA 20. 17. a system's access controls to exploit a legitimate user's account. A. precursor B. backlog C. carrier time D. backoff A. Hacker B. Masquerader C. Misfeasor D. Clandestine user A. Transport B. Tunnel C. Protected D. None of the above mode provides protection to the entire IP packet. inbound or outbound. A. Service B. User C. Behaviour D. Direction is an individual who is not authorized to use the computer and who penetrates TCP connections. control determines the types of Internet services that can be accessed, firewall tightens up the rules for TCP traffic by creating a directory of outbound A. Application level gateway B. Circuit level gateway C. Packet filtering D. Stateful inspection Page 14 Section B: Short & Long Answers Question 1 (2 Marks) Convert the following binary IP Address to Decimal IP Address. 11000000.10101000.00101101.01111001 30 Marks Question 2 (4 Marks) With the aid of diagram(s), explain what you understand by Multipath interference. Page 6 Question 3 (4 Marks) th Twelve packets are to be transmitted using "Stop & Wait" protocol and every 5 packet is lost in the transmission. The packets are numbered as below. Show the full transmission between the sender and the receiver using "Stop & Wait" protocol. (show the full transmission including the retransmitted packets). 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14 Question 4 (6 Marks) The checksum approach is a simple way of verifying that data is not corrupted during transmission. Using ones-complement addition, find the checksum on the following data. 00FC C523 FDA1 D68A AF02 Page 8 Question 5 (4 Marks) Given a class A network address of 29.0.0.0, you have been asked to create at least 20 networks each supporting a maximum of 160 hosts. Show your calculations that these two subnet masks would work. Subnet masks - 255.255.0.0 and 255.255.255.0 Page 9 Question 6 (1 Mark) How do VLANs facilitate network segmentation? Question 7 (2 Marks) Aloha, Slotted Aloha, CSMA and CSMA/CD are examples of how multiple access is facilitated in Ethernet. Identify the main issue with each version of Ethernet and state how the successive version improves of it. Page | 10 Question 8 (2 Marks) Compare and contrast how your phone call and your email packets are switched? Question 9 (1 Mark) A station on a LAN that includes an attached bridge sends out a frame to a device that is not present on any of the segments of the total network. What does the bridge do with this frame? Page 11 Question 10 (2 Marks) Using Dijkstra's algorithm, generate a least-cost route to all other nodes from node 3 for the given network configuration 8 2 5 3 1 7 2 N N4 3 6 3 1 Page | 12 N5 5 8 2 4 N6 Question 11 (2 Marks) Consider the following network cofiguration and illustrate how the incessant retransmission of packets were limited in flooding routing strategy when a souce node 1 wants to send a packet to destination node 6. 4 3 5 Page 13
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


