Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Study & evaluate the extract below and answer the following questions. Today more and more softwares are developing and people are getting more and
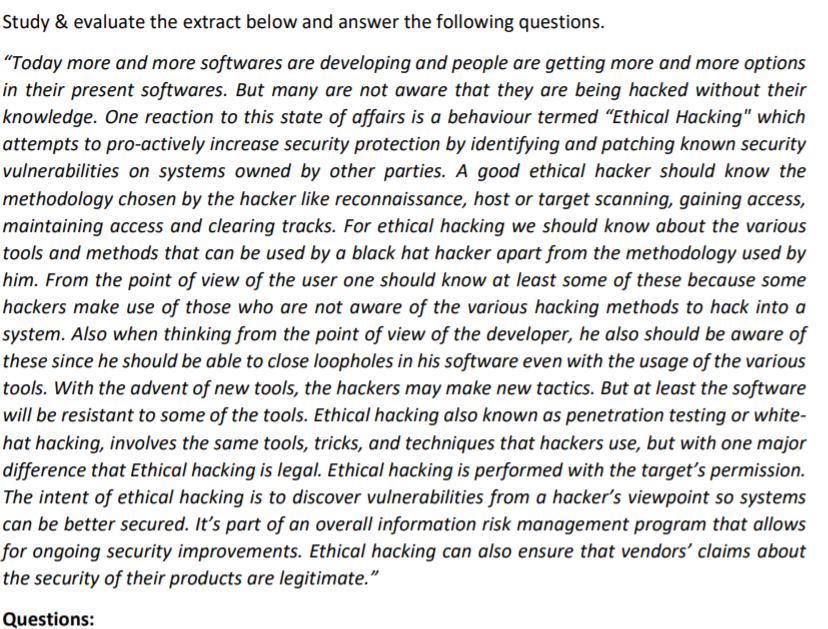
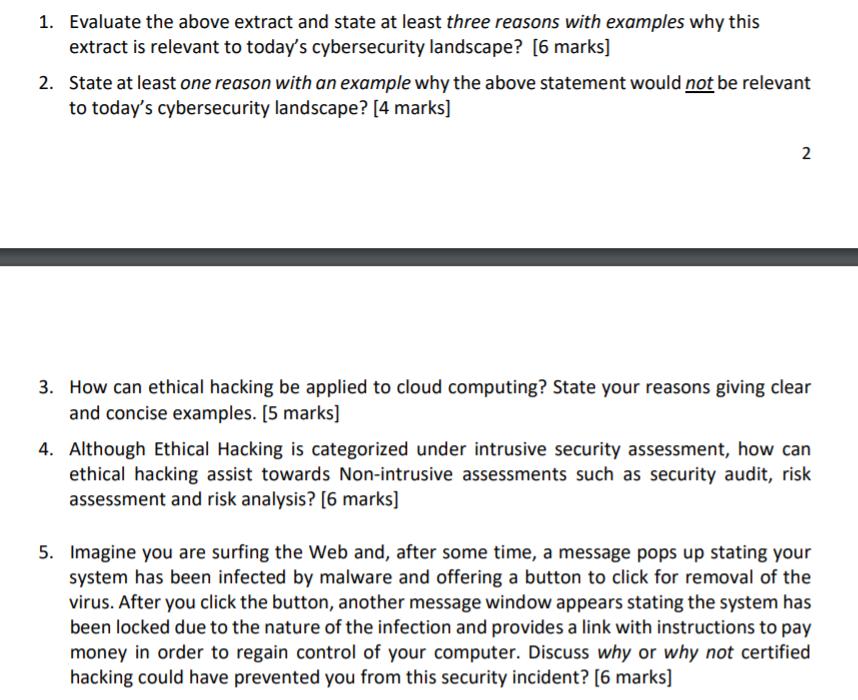
Study & evaluate the extract below and answer the following questions. "Today more and more softwares are developing and people are getting more and more options in their present softwares. But many are not aware that they are being hacked without their knowledge. One reaction to this state of affairs is a behaviour termed "Ethical Hacking" which attempts to pro-actively increase security protection by identifying and patching known security vulnerabilities on systems owned by other parties. A good ethical hacker should know the methodology chosen by the hacker like reconnaissance, host or target scanning, gaining access, maintaining access and clearing tracks. For ethical hacking we should know about the various tools and methods that can be used by a black hat hacker apart from the methodology used by him. From the point of view of the user one should know at least some of these because some hackers make use of those who are not aware of the various hacking methods to hack into a system. Also when thinking from the point of view of the developer, he also should be aware of these since he should be able to close loopholes in his software even with the usage of the various tools. With the advent of new tools, the hackers may make new tactics. But at least the software will be resistant to some of the tools. Ethical hacking also known as penetration testing or white- hat hacking, involves the same tools, tricks, and techniques that hackers use, but with one major difference that Ethical hacking is legal. Ethical hacking is performed with the target's permission. The intent of ethical hacking is to discover vulnerabilities from a hacker's viewpoint so systems can be better secured. It's part of an overall information risk management program that allows for ongoing security improvements. Ethical hacking can also ensure that vendors' claims about the security of their products are legitimate." Questions: 1. Evaluate the above extract and state at least three reasons with examples why this extract is relevant to today's cybersecurity landscape? [6 marks] 2. State at least one reason with an example why the above statement would not be relevant to today's cybersecurity landscape? [4 marks] 2 3. How can ethical hacking be applied to cloud computing? State your reasons giving clear and concise examples. [5 marks] 4. Although Ethical Hacking is categorized under intrusive security assessment, how can ethical hacking assist towards Non-intrusive assessments such as security audit, risk assessment and risk analysis? [6 marks] 5. Imagine you are surfing the Web and, after some time, a message pops up stating your system has been infected by malware and offering a button to click for removal of the virus. After you click the button, another message window appears stating the system has been locked due to the nature of the infection and provides a link with instructions to pay money in order to regain control of your computer. Discuss why or why not certified hacking could have prevented you from this security incident? [6 marks]
Step by Step Solution
★★★★★
3.51 Rating (164 Votes )
There are 3 Steps involved in it
Step: 1
2 Q1 The three reasons why this extract is relevant to todays cybersecurity landscape are 1 Variety ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started