Answered step by step
Verified Expert Solution
Question
1 Approved Answer
311) - Word e search ngs Review View Help Assignment 3 Use Listing 1-1 in the text as a guide for the steps to complete
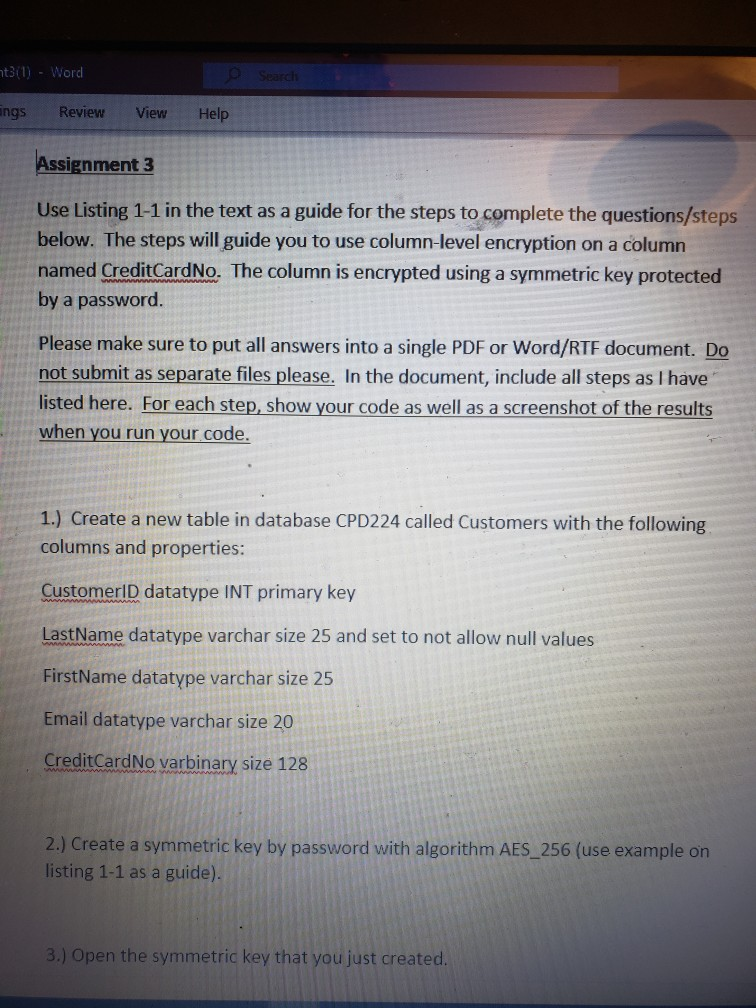
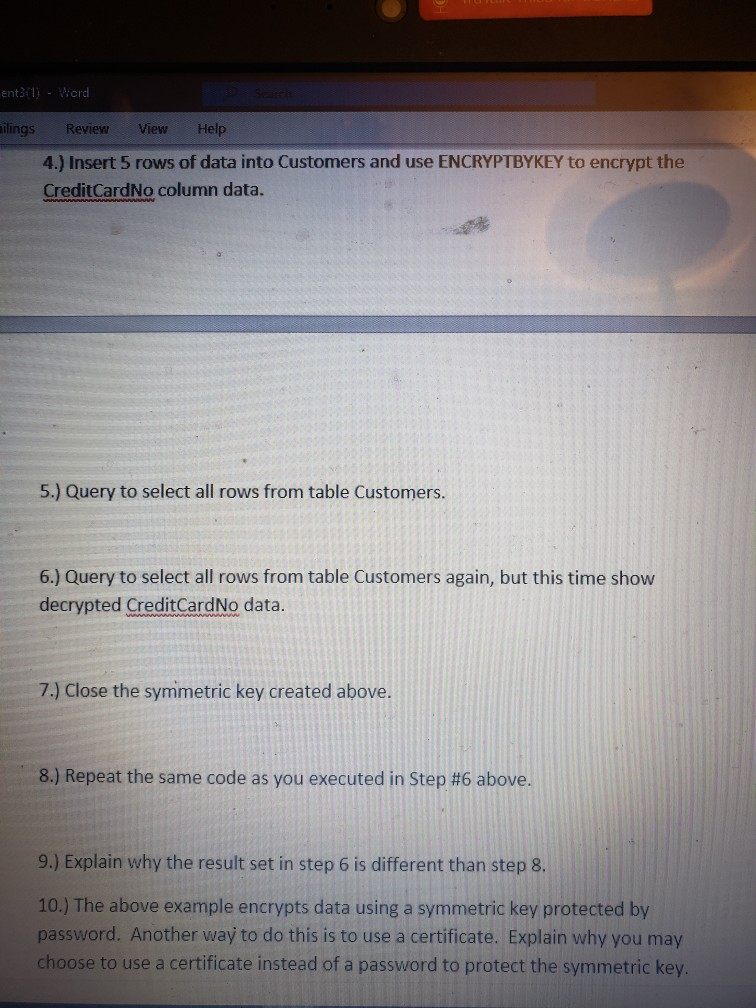
311) - Word e search ngs Review View Help Assignment 3 Use Listing 1-1 in the text as a guide for the steps to complete the questions/steps below. The steps will guide you to use column-level encryption on a column named CreditCardNo. The column is encrypted using a symmetric key protected by a password. Please make sure to put all answers into a single PDF or Word/RTF document. Do not submit as separate files please. In the document, include all steps as I have listed here. For each step, show your code as well as a screenshot of the results when you run your code. 1.) Create a new table in database CPD224 called Customers with the following columns and properties: CustomerID datatype INT primary key LastName datatype varchar size 25 and set to not allow null values First Name datatype varchar size 25 Email datatype varchar size 20 CreditCardNo varbinary size 128 2.) Create a symmetric key by password with algorithm AES 256 (use example on listing 1-1 as a guide). 3.) Open the symmetric key that you just created. ent3/1) - Word ailings Review View Help 4.) Insert 5 rows of data into Customers and use ENCRYPTBYKEY to encrypt the CreditCardNo column data. 5.) Query to select all rows from table Customers. 6.) Query to select all rows from table Customers again, but this time show decrypted Credit CardNo data. 7.) Close the symmetric key created above. 8.) Repeat the same code as you executed in Step #6 above. 9.) Explain why the result set in step 6 is different than step 8. 10.) The above example encrypts data using a symmetric key protected by password. Another way to do this is to use a certificate. Explain why you may choose to use a certificate instead of a password to protect the symmetric key
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


