Answered step by step
Verified Expert Solution
Question
1 Approved Answer
5. (20 marks) What is the possible situation(s) of the following screenshot referred to? What the attacker is trying to get? List 2 well
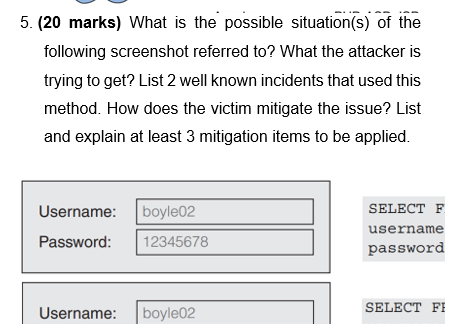
5. (20 marks) What is the possible situation(s) of the following screenshot referred to? What the attacker is trying to get? List 2 well known incidents that used this method. How does the victim mitigate the issue? List and explain at least 3 mitigation items to be applied. Username: boyle02 Password: 12345678 SELECT F username password Username: boyle02 SELECT FI
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


