Answered step by step
Verified Expert Solution
Question
1 Approved Answer
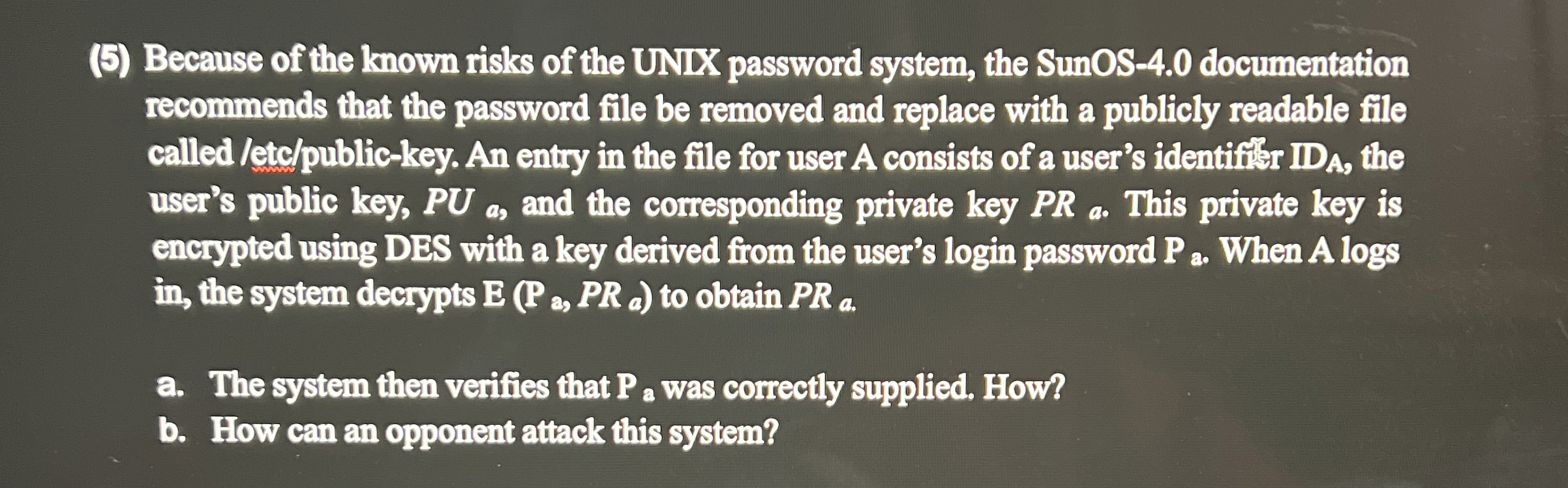
( 5 ) Because of the known risks of the UND password system, the SunOS - 4 . 0 documentation recommends that the password file
Because of the known risks of the UND password system, the SunOS documentation recommends that the password file be removed and replace with a publicly readable file called etepublickey. An entry in the file for user A consists of a user's identifiser ID the user's public key, a and the comesponding private key a This private key is encrypted using DES with a key derived from the user's login password When A logs in the system decrypts to obtain
a The system then verifies that a was correctly supplied. How?
b How can an opponent attack this system?
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


