Answered step by step
Verified Expert Solution
Question
1 Approved Answer
5. Consider the attack on TCP authentication illustrated in Figure 9.28. Suppose that Trudy cannot guess the initial sequence number 62 exactly. Instead, Trudy can
5. Consider the attack on TCP authentication illustrated in Figure 9.28. Suppose that Trudy cannot guess the initial sequence number 62 exactly. Instead, Trudy can only narrow 62 down to one of, say, 1,000 possible values. How can Trudy conduct an attack so that she is likely to succeed?
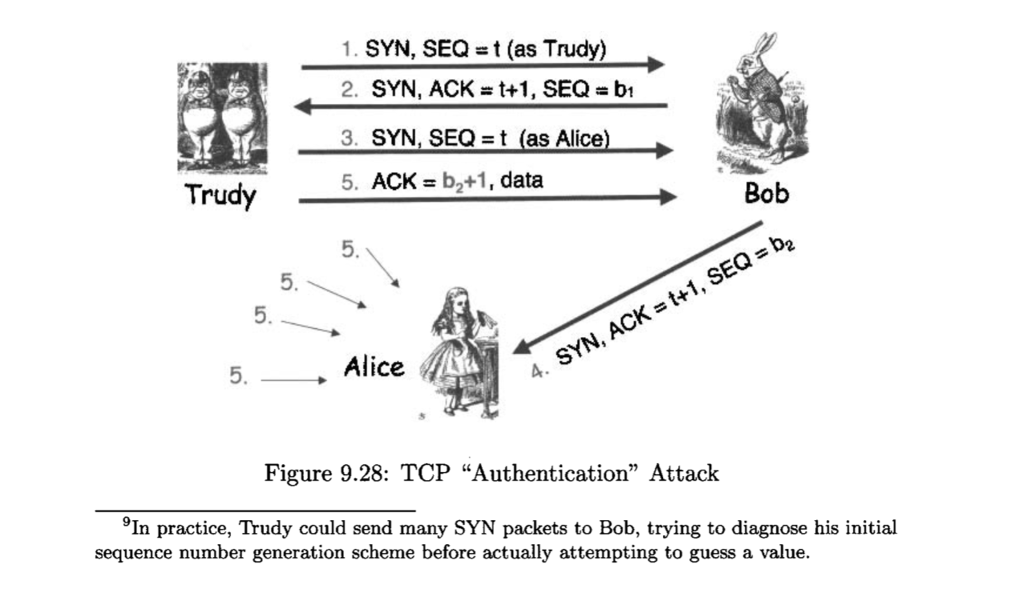
1. SYN, SEQt (as Trudy) 2. SYN, ACK # t+1, SEQ bi 3, SYN, SEQt (as Alice) 5. ACK b2+1, data 5. Trudy Bob 5. 5. 5 , Alice 4. SYN, ACK +1, SEQ b2 Figure 9.28: TCP "Authentication" Attack 9In practice, Trudy could send many SYN packets to Bob, trying to diagnose his initial sequence number generation scheme before actually attempting to guess a value. 1. SYN, SEQt (as Trudy) 2. SYN, ACK # t+1, SEQ bi 3, SYN, SEQt (as Alice) 5. ACK b2+1, data 5. Trudy Bob 5. 5. 5 , Alice 4. SYN, ACK +1, SEQ b2 Figure 9.28: TCP "Authentication" Attack 9In practice, Trudy could send many SYN packets to Bob, trying to diagnose his initial sequence number generation scheme before actually attempting to guess a value
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


