Question: a) Consider you are a network administrator at OSY and you have been given the 198.168.156.0/24 address space to design the network below, with
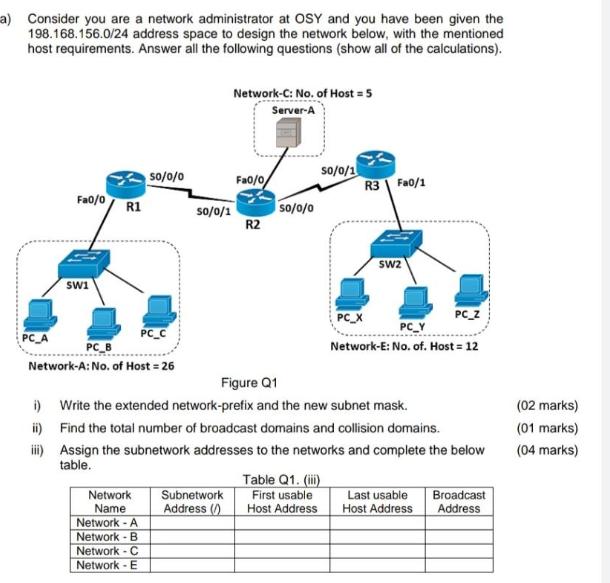

a) Consider you are a network administrator at OSY and you have been given the 198.168.156.0/24 address space to design the network below, with the mentioned host requirements. Answer all the following questions (show all of the calculations). Fa0/0 PC_A SW1 R1 PC_C PC_B Network-A: No. of Host = 26 50/0/0 Network Name Network - A Network B Network C Network - E so/0/1 Network-C: No. of Host = 5 Server-A Subnetwork Address() Fa0/0/ R2 50/0/0 so/0/1 Table Q1. (iii) First usable Host Address R3 Fa0/1 SW2 Figure Q1 i) Write the extended network-prefix and the new subnet mask. ii) Find the total number of broadcast domains and collision domains. iii) Assign the subnetwork addresses to the networks and complete the below table. PC_X PC_Y Network-E: No. of. Host = 12 PC_Z Last usable Host Address Broadcast Address (02 marks) (01 marks) (04 marks) v) PC-A is looking for a way to communicate with PC-X. List down all the IP addresses you used to configure PC-A and PC-X. 2 vi) A Newly configured PC-B wants to communicate with Server-A. 1. Will PC-B perform an ARP query to find Server-A's MAC address? Justify your answer. 2. List down all the network nodes that will receive the ARP request sent by the PC-B. 3. Identify whether the Ethernet addresses used in the standard ARP request are unicast, broadcast, or multicast. 4. State the addresses in the ARP reply packet. vii) Explain the following entry in the routing table in respect to router R1. "Gateway of last resort is 192.168.156.34 to network 0.0.0.0" viii) Explain what happens if the size of an IP datagram exceeds the maximum transmission unit of the network (MTU). ix) How does the switch SW2 handle packet forwarding in the case of an unidentified node. x) Discuss the differences between connection-oriented and connection-less protocols with two applications in each. (02 marks) (04 marks) (02 marks) (01 marks) (02 marks) (03 marks)
Step by Step Solution
There are 3 Steps involved in it
Given network address 192168156024 Here we have 3 networks each need 5 12 26 respectively So subnett... View full answer

Get step-by-step solutions from verified subject matter experts


