Answered step by step
Verified Expert Solution
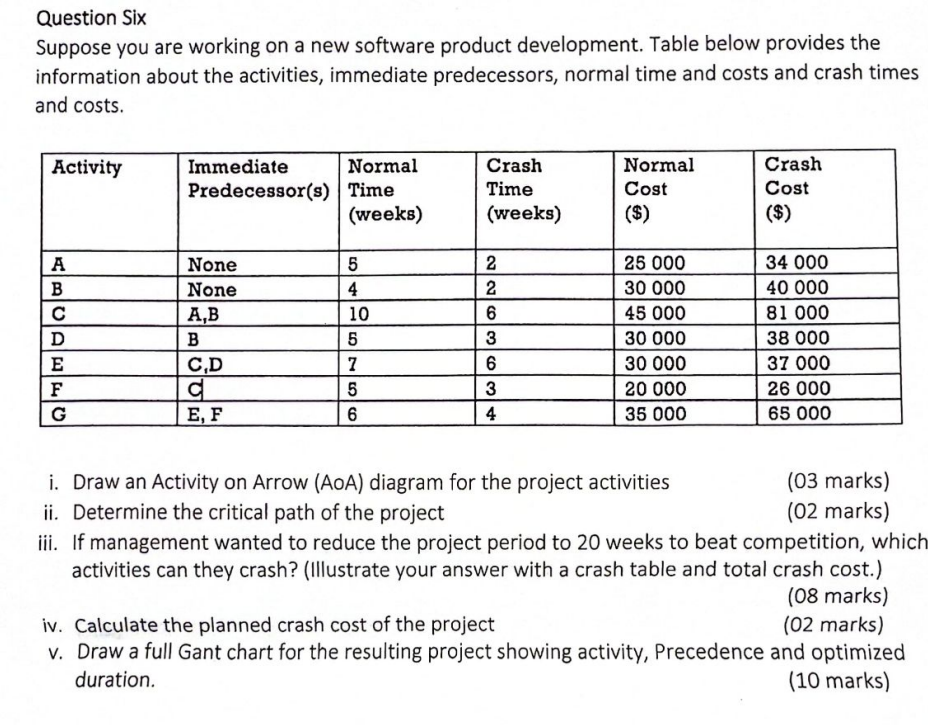
Question
1 Approved Answer
a ) Discuss how each of the following concepts contributes to harmonious living in any work place: i . Ethical decision making Privacy and Confidentiality
a Discuss how each of the following concepts contributes to harmonious living in any work place:
i Ethical decision making
Privacy and Confidentiality iii. Trending technologies iv Control of personal information
v Whistle blowing
b With a relevant example, Differentiate between the following concepts marks@ as used in computing.
i A trade name and business name.
ii The right of reproduction and the right of ownership. iii. Ethical issues and legal issues iv A profession and Professionalism
v Hacking and Cracking
d Explain what organizations can do to deal with the increasing number of computingrelated insecurity happenings around the world. marks
SECTION B
Question
An absent minded work colleague goes on holiday without sharing an important group report which needs to be submitted next week. The latest version is stored on the colleague's personal Cloud box account. Cloud box is a cloud based storage system which uses passwords to control access. Since Cloud box is beyond the reach of your IT department, you suspect that there is nothing you can do However, another colleague knows that the absent colleague always uses their children's birthdays as passwords and all the children have Friend Face accounts. It seems likely that you should be able to get the group report after all as long as the children haven't restricted access to their Friend Face pages.
Required:
With reference to any relevant code of conduct, comment on whether or not there are any legal or ethical issues involved in using Friend Face to find the children's birthdays in order to guess the right password. marks
Question
A small firm hires a recent graduate to develop a novel algorithm for intelligently selecting adverts for an ecommerce site. Part of the work is designing the website so that the generated adverts are positioned in an eye catching manner. As part of his contract, he is required not to write similar software for any competitor for the next months. The developer leaves the company after two years and is employed
to work for a rival company and releases their own version of the eadverts with almost the sa algorithms and functionalities. The original firm wishes to sue both the programmer and the r company. Required;
a With reference to IEEE code of conduct of your choice, what options does the firm have? marks
b What should you do according to consequentialism theory of ethics? As part of your answ provide a short description of consequentialism. JO marks
Question
A post graduate student notices that the Examinations manager keeps a copy of the password for t academic year exam database on his computer and shares the password with him. The stude realizes that looking at question papers with their typical answers would really help him in revision a so decide to log in as the Exams manager and take a look. Required:
Comment on whether such behavior would trespass the ethical behavior expected of such examinations manger. In addition mention whether you or any other involved party might be liable either legal or University sanction and justify your answer. marks
Question
a Define Intellectual Property. marks
b Explain briefly about following terms:
i Patents ii copyrights marks@
iii. Trade marks.
b Explain briefly the acquisition process of trade mark. marks
c Explain with The project managers are ultimately responsible for project success Marks
a What is the role of the human resource manager on the project team? marks
b Explain the process of resource allocation and management
c Give the Importance of resource management in project planning and executionmarks
d Discuss the different types of project resources and explain how they can be acquired for an IT project Marks
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


