Answered step by step
Verified Expert Solution
Question
1 Approved Answer
a) Examine the protocol type and time to live fields in the IP packet that carries the first ICMP Echo Request. ICMP packet doesn't
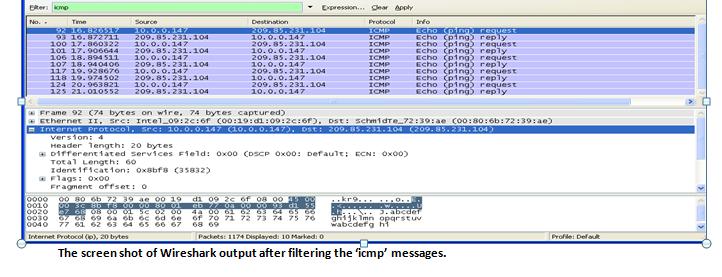
a) Examine the protocol type and time to live fields in the IP packet that carries the first ICMP Echo Request. ICMP packet doesn't have source and destination port numbers. Why? b) Study the ICMP message and what are the fields does ICMP packet have? Check the number of bytes for the checksum, sequence number and identifier fields. c) Identify the data bytes in request message and note the corresponding character sequence in third pane of Wireshark window. What is contained in this data field? (10 marks) ICMP echo reply: a) Compare the message identifier and sequence number in the reply message with the equivalent numbers in the request message. (5 marks) b) Recognize the data bytes in the reply message and compare the data sequence with that in the request message. (5 marks) c)To support the above questions 1 & 2, please provide screen dumps of the Wireshark packets you have captured. i.e. Like the screen dumps shown above in the procedure.(10 marks) ter kmp No.. Time 92 10.826517 93 10.872711 100 17.860322 101 17.906644 106 18.894 511 107 18.940406 117 19.928676 118 19.974502 124 20.963821 125 21.010552 Source 10.0.0.147 209.85.231.104 10.0.0.147 209.85.231.104 10.0.0.147 209.85.231.104 10.0.0.147 209.85.231.104 10.0.0.147 209.85.231.104 Total Length: 60 Identification: 0x8bf8 (35832) Flags: 0x00 Fragment offset: 0 Destination 0000 90 80 6b 72 39 ae 00 19 0010 00 3c 8b 18 00 00 80 01 0020 e7 68 08 00 01 5 02 00 0030 67 68 69 6a ob 6c od de 0040 77 61 62 63 64 65 66 67 Internet Protocol (p), 20 bytes Expression... Cear Apply Protocol TCMP ICMP 209.85.231.104 10.0.0.147 209.85.231.104 10.0.0.147 209.85.231.104 10.0.0.147 209.85.231.104 10.0.0.147 209.85.231.104 10.0.0.147 Frame 92 (74 bytes on wire, 74 bytes captured) Ethernet II, Sec: Intel 09:20:6f (00:19:d1:09:2c:6f), Dst: Schmidre 72:39:ae (00:80:6b:72:39:ae) Internet Protocol, Sec: 10.0.0.147 (10.0.0.147), Dst: 209.85.231.104 (209.85.231.104) version: 4 Header length: 20 bytes Differentiated services Field: 0x00 (DSCP 0x00: Default: ECN: 0X00) 45 00 di 09 2c of 08 eb 77-03 4a 00 61 65 66 of 70 71 72 73 74 75 76 68 69 ICMP ICMP ICMP ICMP ICMP ICMP ICMP ICMP Info Echo (ping) request Echo (ping) reply Echo (ping) request Echo (ping) reply Echo (ping) request Echo (ping) reply Echo (ping) request Echo (ping) reply Echo (ping) request Echo (ping) reply kro........ Keep. W ghijk imn opqrstuv wabcdefg hi Packets: 1174 Displayed: 10 Marked: 0 The screen shot of Wireshark output after filtering the 'icmp' messages. Profile: Defau
Step by Step Solution
★★★★★
3.58 Rating (151 Votes )
There are 3 Steps involved in it
Step: 1
The questions are related to the analysis of Internet Control Message Protocol ICMP packets using the Wireshark network protocol analyzer Unfortunately I cant perform interactive actions such as using ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


