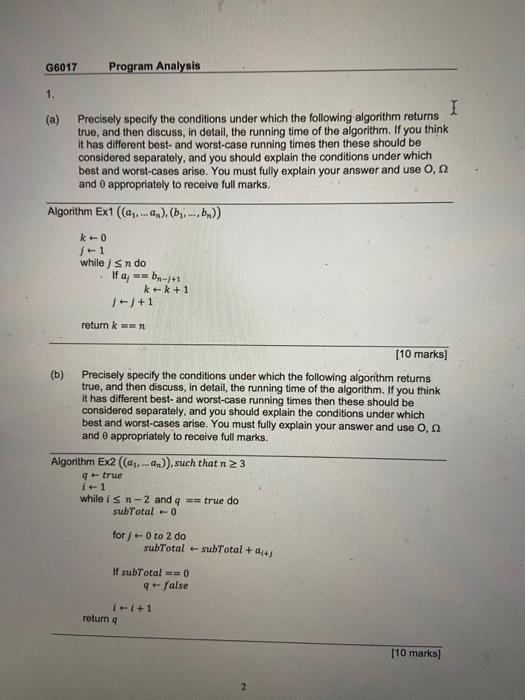
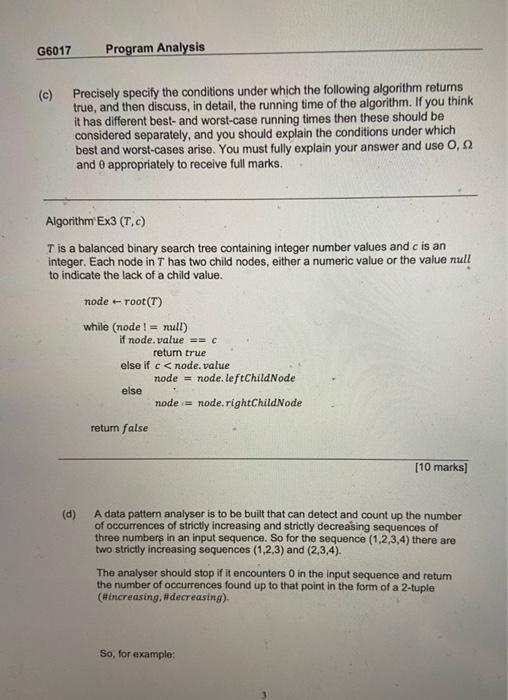
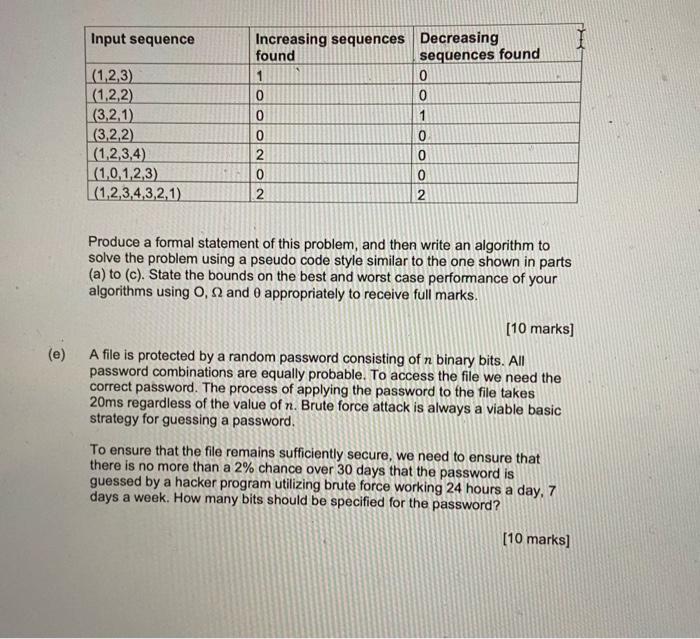
(a) Precisely specify the conditions under which the following algorithm returns true, and then discuss, in detail, the running time of the algorithm. If you think it has different best-and worst-case running times then these should be considered separately, and you should explain the conditions under which best and worst-cases arise. You must fully explain your answer and use O, and appropriately to receive full marks. Algorithm Ex1 ((a1,an),(b1,,bn)) [10 marks] (b) Precisely specify the conditions under which the following algorithm returns true, and then discuss, in detail, the running time of the algorithm. If you think it has different best- and worst-case running times then these should be considered separately, and you should explain the conditions under which best and worst-cases arise. You must fully explain your answer and use O, and appropriately to receive full marks. Algorithm Ex2 ((a1,an)), such that n3 q true i+1 while in2 and q== true do subTotal0 forj+0to2do subTotal subTotal +ai+j If subTotal =00 q+ false. return q (c) Precisely specify the conditions under which the following algorithm returns true, and then discuss, in detail, the running time of the algorithm. If you think it has different best- and worst-case running times then these should be considered separately, and you should explain the conditions under which best and worst-cases arise. You must fully explain your answer and use O, and appropriately to receive full marks. Algorithm Ex3(T,c) T is a balanced binary search tree containing integer number values and c is an integer. Each node in T has two child nodes, either a numeric value or the value null to indicate the lack of a child value. return false [10 marks] (d) A data pattern analyser is to be built that can detect and count up the number of occurrences of strictly increasing and strictly decreasing sequences of three numbers in an input sequence. So for the sequence (1,2,3,4) there are two strictly increasing sequences (1,2,3) and (2,3,4). The analyser should stop if it encounters 0 in the input sequence and return the number of occurrences found up to that point in the form of a 2-tuple (Hincreasing, \#decreasing). So, for example: Produce a formal statement of this problem, and then write an algorithm to solve the problem using a pseudo code style similar to the one shown in parts (a) to (c). State the bounds on the best and worst case performance of your algorithms using 0, and appropriately to receive full marks. [10 marks] A file is protected by a random password consisting of n binary bits. All password combinations are equally probable. To access the file we need the correct password. The process of applying the password to the file takes 20ms regardless of the value of n. Brute force attack is always a viable basic strategy for guessing a password. To ensure that the file remains sufficiently secure, we need to ensure that there is no more than a 2% chance over 30 days that the password is guessed by a hacker program utilizing brute force working 24 hours a day, 7 days a week. How many bits should be specified for the password? (a) Precisely specify the conditions under which the following algorithm returns true, and then discuss, in detail, the running time of the algorithm. If you think it has different best-and worst-case running times then these should be considered separately, and you should explain the conditions under which best and worst-cases arise. You must fully explain your answer and use O, and appropriately to receive full marks. Algorithm Ex1 ((a1,an),(b1,,bn)) [10 marks] (b) Precisely specify the conditions under which the following algorithm returns true, and then discuss, in detail, the running time of the algorithm. If you think it has different best- and worst-case running times then these should be considered separately, and you should explain the conditions under which best and worst-cases arise. You must fully explain your answer and use O, and appropriately to receive full marks. Algorithm Ex2 ((a1,an)), such that n3 q true i+1 while in2 and q== true do subTotal0 forj+0to2do subTotal subTotal +ai+j If subTotal =00 q+ false. return q (c) Precisely specify the conditions under which the following algorithm returns true, and then discuss, in detail, the running time of the algorithm. If you think it has different best- and worst-case running times then these should be considered separately, and you should explain the conditions under which best and worst-cases arise. You must fully explain your answer and use O, and appropriately to receive full marks. Algorithm Ex3(T,c) T is a balanced binary search tree containing integer number values and c is an integer. Each node in T has two child nodes, either a numeric value or the value null to indicate the lack of a child value. return false [10 marks] (d) A data pattern analyser is to be built that can detect and count up the number of occurrences of strictly increasing and strictly decreasing sequences of three numbers in an input sequence. So for the sequence (1,2,3,4) there are two strictly increasing sequences (1,2,3) and (2,3,4). The analyser should stop if it encounters 0 in the input sequence and return the number of occurrences found up to that point in the form of a 2-tuple (Hincreasing, \#decreasing). So, for example: Produce a formal statement of this problem, and then write an algorithm to solve the problem using a pseudo code style similar to the one shown in parts (a) to (c). State the bounds on the best and worst case performance of your algorithms using 0, and appropriately to receive full marks. [10 marks] A file is protected by a random password consisting of n binary bits. All password combinations are equally probable. To access the file we need the correct password. The process of applying the password to the file takes 20ms regardless of the value of n. Brute force attack is always a viable basic strategy for guessing a password. To ensure that the file remains sufficiently secure, we need to ensure that there is no more than a 2% chance over 30 days that the password is guessed by a hacker program utilizing brute force working 24 hours a day, 7 days a week. How many bits should be specified for the password