

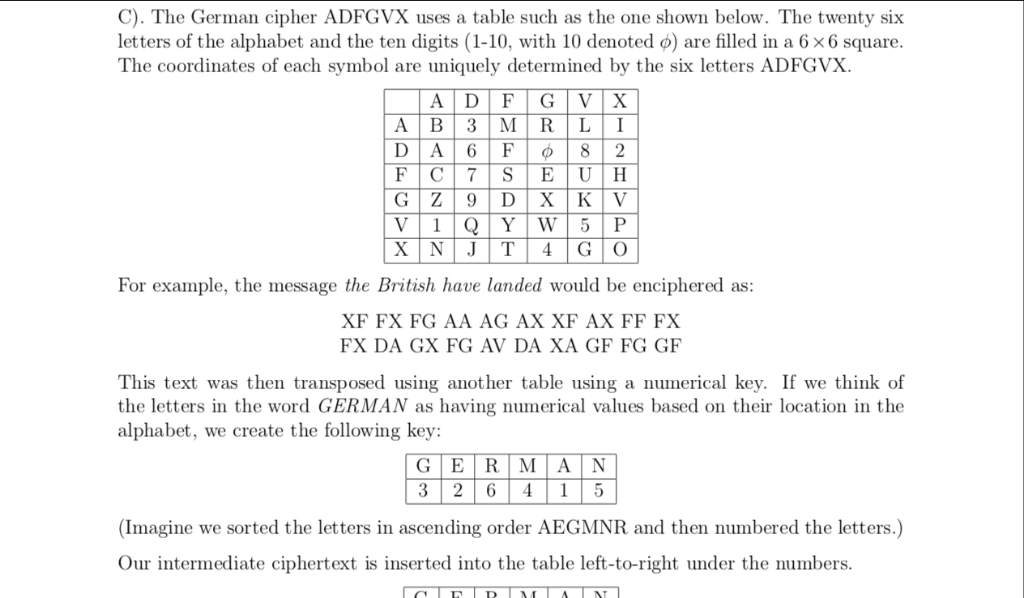

A). The following table shows the key to a Caesar cipher: Plain | N | O | P | Q | R | S | T | | V | W | X | Y | Z Decipher the following message which was enciphered with the above table NQRZOHGJH LV SRZHU B). Consider the following Digraph cipher, where the letters W and X are considered a single symbol. Pairs of letters are enciphered according to the following rules 1. If two letters are in the same row, then their ciphertext assignments are immediately to their right. OM NO 2. If two letters are in the same column, then their ciphertext assignments are immediately below them. TP KI 3. If two letters are on the corners of a diagonal formed by the letters, then their ciphertext 3. II two letters are on the corners of a diagonal formed by the letters, then their ciphertext assignments are on the opposite corner, same row. NB - QR 4. If the same letter appears as a pair in the plaintext, insert the letter Z between them and then encipher 5. If a single letter is left at the end of the enciphering, append a Z and then encipher Using these rules and the associated table, known as the Playfair cipher, decipher the follow- ing message: C). The German cipher ADFGVX uses a table such as the one shown below. The twenty six letters of the alphabet and the ten digits (1-10, with 10 denoted are filled in a 6 6 square The coordinates of each symbol are uniquely determined by the six letters ADFGVX For example, the message the British have landed would be enciphered as: XF FX FG AA AG AX XF AX FF FX FX DA GX FG AV DA XA GF FG GF This text was then transposed using another table using a numerical key. If we think of the letters in the word GERMAN as having numerical values based on their location in the alphabet, we create the following key: 3 26 415 (Imagine we sorted the letters in ascending order AEGMNR and then numbered the letters.) Our intermediate ciphertext is inserted into the table left-to-right under the numbers 249/homework-1.pd Get Homework Help With Chegg Study | Chegg.com Our intermediate ciphertext is inserted into the table left-to-right under the numbers. 3 26415 GXFGAV The final ciphertext is obtained by reading out the the columns of the table starting with the column numbered "1" and proceeding in order. Letters are grouped into chunks of five Our message is now enciphered as XGXXG AFGXF AVFFA AFFXG Decipher the following message enciphered using the above cipher: AFAXX AGFAX FFXAA XGGVX FGXFA XAAFX










