Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Alice and Bob communicate over an insecure network and want to securely exchange information. They decided to use a Caesar cipher for encryption and the
Alice and Bob communicate over an insecure network and want to securely exchange
information. They decided to use a Caesar cipher for encryption and the DiffieHellman
key exchange for secure key generation. Alice and Bob decide to use the DiffieHellman
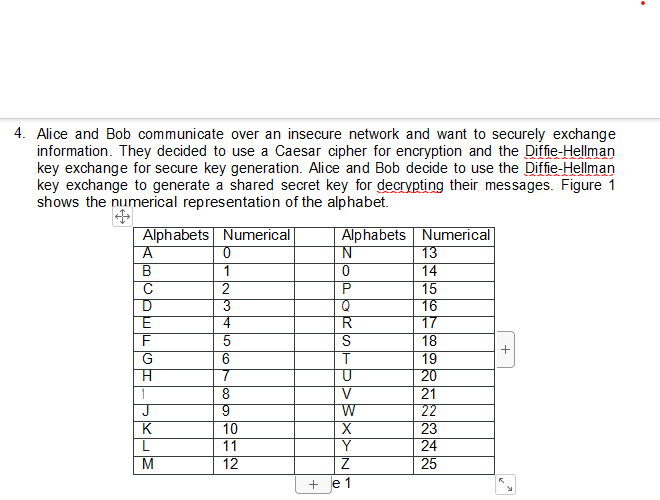
key exchange to generate a shared secret key for decrypting their messages. Figure
shows the numerical representation of the alphabet.
aIf Alice chooses a private key a and Bob chooses a private key b and the agreedupon base g with a prime modulus p Compute the shared secret key for Bob and Alice.
bDecrypt the following encrypted terms.
iDVC
iiUOBLOBYC
iii.WPK
ivFSBEC
vSZ
cExplain each of the decrypted terms in b
Marks
Marks
Marks
dExplain how the DiffieHellman key exchange is vulnerable to a maninthemiddle attack.
Marks
eProvide TWO possible solutions to overcome the vulnerability of the Diffie Hellman key exchange to maninthemiddle attacks.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


