Answered step by step
Verified Expert Solution
Question
1 Approved Answer
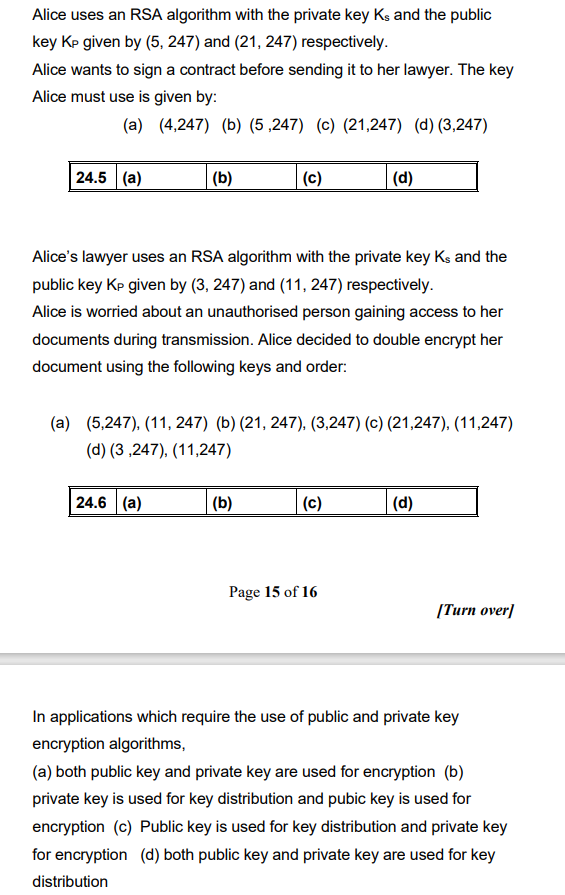
Alice uses an RSA algorithm with the private key Ks and the public key KP given by ( 5 , 2 4 7 ) and
Alice uses an RSA algorithm with the private key Ks and the public
key KP given by and respectively.
Alice wants to sign a contract before sending it to her lawyer. The key
Alice must use is given by:
abcd
Alices lawyer uses an RSA algorithm with the private key Ks and the
public key KP given by and respectively.
Alice is worried about an unauthorised person gaining access to her
documents during transmission. Alice decided to double encrypt her
document using the following keys and order:
abc
d
In applications which require the use of public and private key
encryption algorithms,
a both public key and private key are used for encryption b
private key is used for key distribution and pubic key is used for
encryption c Public key is used for key distribution and private key
for encryption d both public key and private key are used for key
distribution
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


