Question
An information system uses username and password for users authentication. The system. differentiates between three types of users: basic (regular) users, power users and administrators.
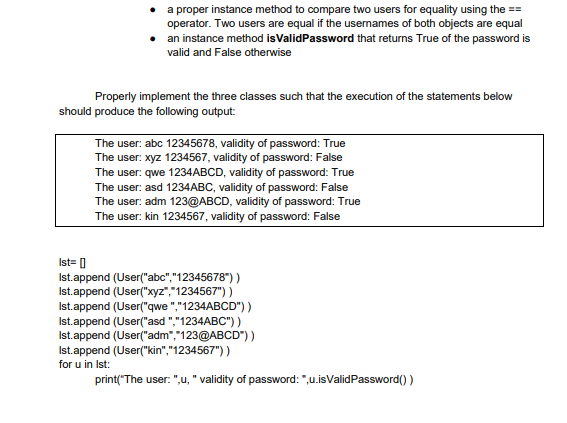
An information system uses username and password for users authentication. The system. differentiates between three types of users: basic (regular) users, power users and administrators. Consider the class hierarchy diagram below that represents the relation between user types Each user has a username and password. For security reasons the following password validity rules used: Valid passwords for basic users should be at least 8 characters long Valid passwords for power users should: be at least 8 characters long and has at least 2 digits and has at least 2 letters. Valid password for administrators should: meet all the requirements for valid passwords of power users and has at least 1 special character (non alphanumeric). Properly implement the three classes. Make sure to include the constructor for each class, the setter and getter for each instance variable the instance method __repr__ as necessary ( see output below) a proper instance method to compare two users for equality using the == operator. Two users are equal if the usernames of both objects are equal an instance method isValidPassword that returns True of the password is valid and False otherwise Properly implement the three classes such that the execution of the statements below should produce the following output: The user: abc 12345678, validity of password: True The user: xyz 1234567, validity of password: False The user: qwe 1234ABCD, validity of password: True The user: asd 1234ABC, validity of password: False The user: adm 123@ABCD, validity of password: True The user: kin 1234567, validity of password: False lst= [] lst.append (User("abc","12345678") ) lst.append (User("xyz","1234567") ) lst.append (User("qwe ","1234ABCD") ) lst.append (User("asd ","1234ABC") ) lst.append (User("adm","123@ABCD") ) lst.append (User("kin","1234567") ) for u in lst: print(The user: ",u, " validity of password: ",u.isValidPassword() )
use python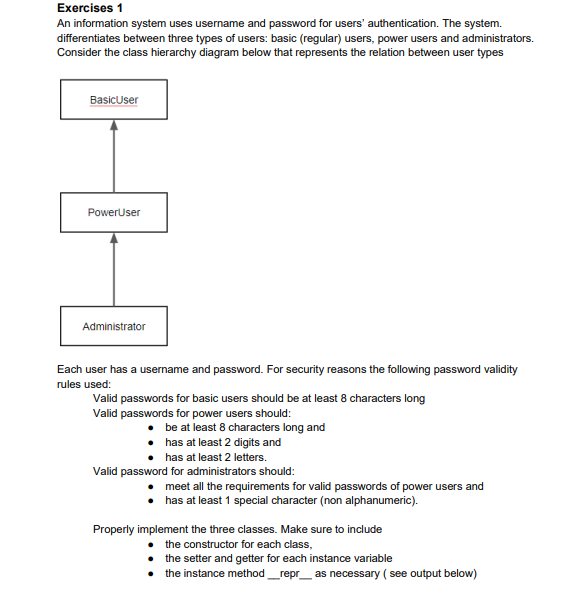
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


