Answered step by step
Verified Expert Solution
Question
1 Approved Answer
An IS auditor is auditing the change management process for a financial application. The auditor has two primary pieces of evidence: change logs and a
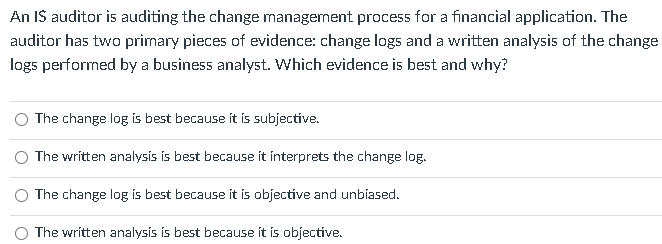

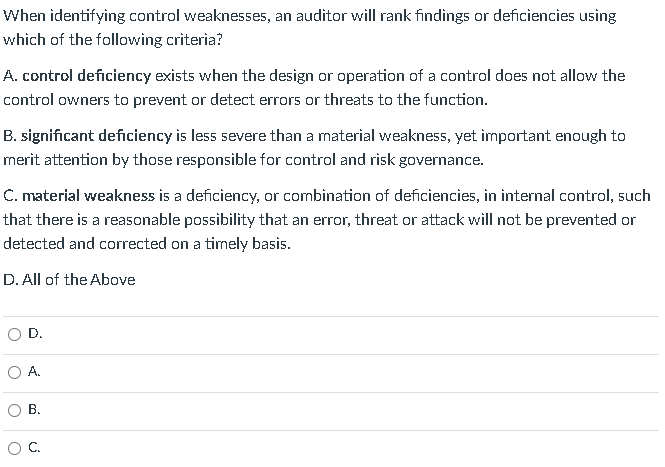
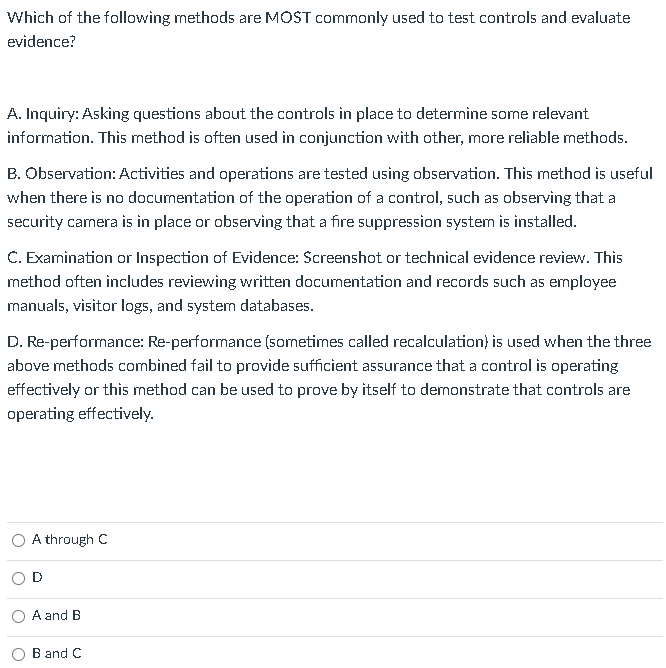
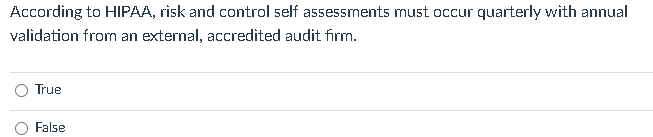 An IS auditor is auditing the change management process for a financial application. The auditor has two primary pieces of evidence: change logs and a written analysis of the change logs performed by a business analyst. Which evidence is best and why? The change log is best because it is subjective. The written analysis is best because it interprets the change log. The change log is best because it is objective and unbiased. The written analysis is best because it is objective. What is the appropriate role of an IS auditor in a control self-assessment? The IS auditor should participate as a subject matter expert. The IS auditor should act as facilitator. The IS auditor should not be involved. The IS auditor should design the control self-assessment. When identifying control weaknesses, an auditor will rank findings or deficiencies using which of the following criteria? A. control deficiency exists when the design or operation of a control does not allow the control owners to prevent or detect errors or threats to the function. B. significant deficiency is less severe than a material weakness, yet important enough to merit attention by those responsible for control and risk governance. C. material weakness is a deficiency, or combination of deficiencies, in internal control, such that there is a reasonable possibility that an error, threat or attack will not be prevented or detected and corrected on a timely basis. D. All of the Above D. A. B. c. Which of the following methods are MOST commonly used to test controls and evaluate evidence? A. Inquiry: Asking questions about the controls in place to determine some relevant information. This method is often used in conjunction with other, more reliable methods. B. Observation: Activities and operations are tested using observation. This method is useful when there is no documentation of the operation of a control, such as observing that a security camera is in place or observing that a fire suppression system is installed. C. Exarnination or Inspection of Evidence: Screenshot or technical evidence review. This method often includes reviewing written documentation and records such as employee manuals, visitor logs, and system databases. D. Re-performance: Re-performance (sometimes called recalculation) is used when the three above methods combined fail to provide sufficient assurance that a control is operating effectively or this method can be used to prove by itself to demonstrate that controls are operating effectively. A through C D A and B B and C According to HIPAA, risk and control self assessments must occur quarterly with annual validation from an external, accredited audit firm. True False
An IS auditor is auditing the change management process for a financial application. The auditor has two primary pieces of evidence: change logs and a written analysis of the change logs performed by a business analyst. Which evidence is best and why? The change log is best because it is subjective. The written analysis is best because it interprets the change log. The change log is best because it is objective and unbiased. The written analysis is best because it is objective. What is the appropriate role of an IS auditor in a control self-assessment? The IS auditor should participate as a subject matter expert. The IS auditor should act as facilitator. The IS auditor should not be involved. The IS auditor should design the control self-assessment. When identifying control weaknesses, an auditor will rank findings or deficiencies using which of the following criteria? A. control deficiency exists when the design or operation of a control does not allow the control owners to prevent or detect errors or threats to the function. B. significant deficiency is less severe than a material weakness, yet important enough to merit attention by those responsible for control and risk governance. C. material weakness is a deficiency, or combination of deficiencies, in internal control, such that there is a reasonable possibility that an error, threat or attack will not be prevented or detected and corrected on a timely basis. D. All of the Above D. A. B. c. Which of the following methods are MOST commonly used to test controls and evaluate evidence? A. Inquiry: Asking questions about the controls in place to determine some relevant information. This method is often used in conjunction with other, more reliable methods. B. Observation: Activities and operations are tested using observation. This method is useful when there is no documentation of the operation of a control, such as observing that a security camera is in place or observing that a fire suppression system is installed. C. Exarnination or Inspection of Evidence: Screenshot or technical evidence review. This method often includes reviewing written documentation and records such as employee manuals, visitor logs, and system databases. D. Re-performance: Re-performance (sometimes called recalculation) is used when the three above methods combined fail to provide sufficient assurance that a control is operating effectively or this method can be used to prove by itself to demonstrate that controls are operating effectively. A through C D A and B B and C According to HIPAA, risk and control self assessments must occur quarterly with annual validation from an external, accredited audit firm. True False Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


