Question: 5. In modern networks, including the Internet, the source host segments long, application-layer messages (e.g. an image or a music file) into smaller packets
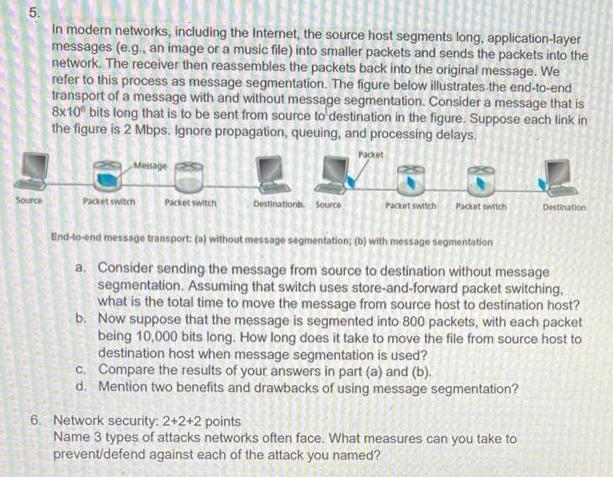
5. In modern networks, including the Internet, the source host segments long, application-layer messages (e.g. an image or a music file) into smaller packets and sends the packets into the network. The receiver then reassembles the packets back into the original message. We refer to this process as message segmentation. The figure below illustrates.the end-to-end transport of a message with and without message segmentation. Consider a message that is 8x10 bits long that is to be sent from source to destination in the figure. Suppose each link in the figure is 2 Mbps. Ignore propagation, queuing, and processing delays. Packet Message Source Pacet switch Packet switch Destinationa. Source Pacet switch Packet switch Destination End-to-end message transport: (a) without message segmentation; (b) with message segmentation a. Consider sending the message from source to destination without message segmentation. Assuming that switch uses store-and-forward packet switching, what is the total time to move the message from source host to destination host? b. Now suppose that the message is segmented into 800 packets, with each packet being 10,000 bits long. How long does it take to move the file from source host to destination host when message segmentation is used? c. Compare the results of your answers in part (a) and (b). d. Mention two benefits and drawbacks of using message segmentation? 6. Network security: 2+2+2 points Name 3 types of attacks networks often face. What measures can you take to prevent/defend against each of the attack you named?
Step by Step Solution
3.38 Rating (170 Votes )
There are 3 Steps involved in it
a The time taken to send message from source host to first packet switch By store an... View full answer

Get step-by-step solutions from verified subject matter experts


