Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Explain why this protocol is or is not subject to a man-in-the-middle attack for Trudy to get the session key.n [g mod p, {R1}BobJAlice [gb
Explain why this protocol is or is not subject to a man-in-the-middle attack for Trudy to get the session key.n
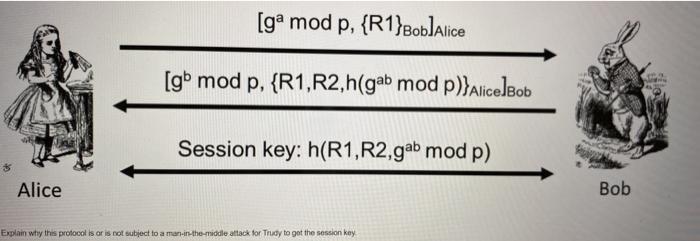
[g mod p, {R1}BobJAlice [gb mod p, {R1,R2,h(gab mod p)}AlicelBob Session key: h(R1,R2,gab mod p) Alice Bob Explain why this profocol is ar is not subject to a man-in-the-middle attack for Trudy to get the session key.
Step by Step Solution
★★★★★
3.36 Rating (152 Votes )
There are 3 Steps involved in it
Step: 1
A man in the middle MITM attack is a general term for when a perpetrator positions himself in a conversation between a user and an applicationeither to eavesdrop or to impersonate one of the parties m...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


