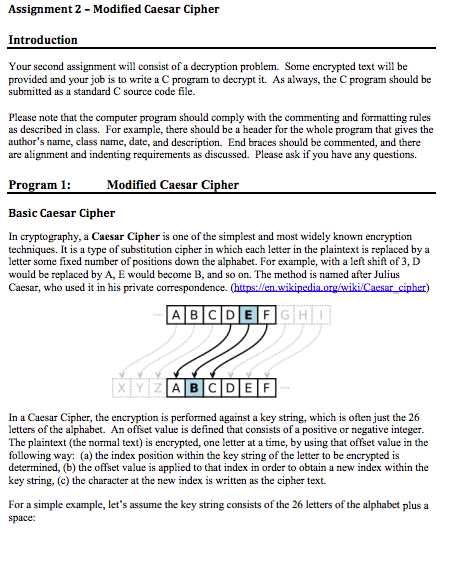



Assignment 2 - Modified Caesar Cipher Introduction Your second assignment will consist of a decryption problem. Some encrypted text will be provided and your job is to write a C program to decrypt it. As always, the C program should be submitted as a standard C source code file. Please note that the computer program should comply with the commenting and formatting rules as described in class. For example, there should be a header for the whole program that gives the author's name, class name, date, and description. End braces should be commented, and there are alignment and indenting requirements as discussed. Please ask if you have any questions. Program 1: Modified Caesar Cipher Basic Caesar Cipher In cryptography, a Caesar Cipher is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on. The method is named after Julius Caesar, who used it in his private correspondence. (httns-enwikinedia org/wiki Caesar cinher) ABICIDIEIF In a Caesar Cipher, the encryption is performed against a key string, which is often just the 26 letters of the alphabet. An offset value is defined that consists of a positive or negative integer. The plaintext (the normal text) is encrypted, one letter at a time, by using that offset value in the following way: (a) the index position within the key string of the letter to be encrypted is determined, (b) the offset value is applied to that index in order to obtain a new index within the key string, (c) the character at the new index is written as the cipher text. For a simple example, let's assume the key string consists of the 26 letters of the alphabet plus a space Assignment 2 - Modified Caesar Cipher Introduction Your second assignment will consist of a decryption problem. Some encrypted text will be provided and your job is to write a C program to decrypt it. As always, the C program should be submitted as a standard C source code file. Please note that the computer program should comply with the commenting and formatting rules as described in class. For example, there should be a header for the whole program that gives the author's name, class name, date, and description. End braces should be commented, and there are alignment and indenting requirements as discussed. Please ask if you have any questions. Program 1: Modified Caesar Cipher Basic Caesar Cipher In cryptography, a Caesar Cipher is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a left shift of 3, D would be replaced by A, E would become B, and so on. The method is named after Julius Caesar, who used it in his private correspondence. (httns-enwikinedia org/wiki Caesar cinher) ABICIDIEIF In a Caesar Cipher, the encryption is performed against a key string, which is often just the 26 letters of the alphabet. An offset value is defined that consists of a positive or negative integer. The plaintext (the normal text) is encrypted, one letter at a time, by using that offset value in the following way: (a) the index position within the key string of the letter to be encrypted is determined, (b) the offset value is applied to that index in order to obtain a new index within the key string, (c) the character at the new index is written as the cipher text. For a simple example, let's assume the key string consists of the 26 letters of the alphabet plus a space










