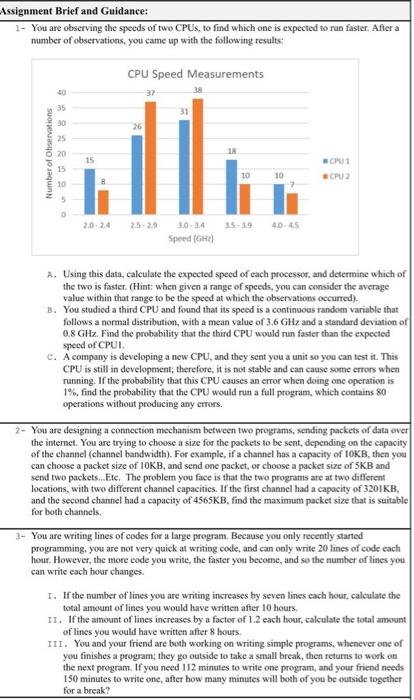
Assignment Brief and Guidance: 1 - You are observing the speeds of two CPUs, to find which one is expected to run faster. After a number of observations, you came up with the following results: CPU Speed Measurements 20 37 35 31 30 26 25 Number of Observations 20 18 15 15 CPU 1 CPUZ 10 10 10 B 20-24 23-29 35-19 40-45 Speed (GH) A. Using this data, calculate the expected speed of each processor, and determine which of the two is faster. (Hint: when given a range of speeds, you can consider the average value within that range to be the speed at which the observations occurred). B. You studied a third CPU and found that its speed is a continuous random variable that follows a normal distribution, with a mean value of 3.6 GHz and a standard deviation of 0.8 GHz. Find the probability that the third CPU would run faster than the expected speed of CPUL. c. A company is developing a new CPU, and they sent you a unit so you can test it. This CPU is still in development; therefore, it is not stable and can cause some errors when running. If the probability that this CPU causes an error when doing one operation is 1%, find the probability that the CPU would run a full program, which contains 80 operations without producing any errors. 2- You are designing a connection mechanism between two programs, sending packets of data over the internet. You are trying to choose a size for the packets to be sent, depending on the capacity of the channel (channel bandwidth). For example, if a channel has a capacity of 10KB, then you can choose a packet size of IOKB, and send onc packet, or choose a packet size of SKB and send two packets... Etc. The problem you face is that the two programs are at two different locations, with two different channel capacities. If the first channel had a capacity of 3201 KB. and the second channel had a capacity of 4565KB, find the maximum packet size that is suitable for both channels. 3- You are writing lines of codes for a large program. Because you only recently started programming, you are not very quick at writing code, and can only write 20 lines of code cach hour. However, the more code you write, the faster you become, and so the number of lines you can write each hour changes 1. If the number of lines you are writing increases by seven lines each hour, calculate the total amount of lines you would have written after 10 hours. II. If the amount of lines increases by a factor of 1.2 each hour, calculate the total amount of lines you would have written after 8 hours. III. You and your friend are both working on writing simple programs, whenever one of you finishes a program; they go outside to take a small break, then returns to work on the next program. If you need 112 minutes to write one program, and your friend needs 150 minutes to write one, after how many minutes will both of you be outside together for a break? 4- You developed a new social media website. The website is cross-platform (can be used on both computers and mobile phones). You conducted a study about the users and obtained the following results: 47% of users were Males .84% of Female users are using the website on a mobile (not on a computer) Find the following: A. The probability that a user is a Female. B. The probability that a Female user is using the website on a computer c. The probability that a random user is both Female and using the website on a computer. 5- A simple encryption method is being used to encrypt a small number (called the secret number). The method by which this encryption works is as follows: I. Choose a random seed number II. Calculate the key by multiplying the seed with the secret under modulus 7 III. Finally, multiply the key with the secret to get the encrypted secret Example: If our secret number was 45 Randomly choose seed = 6 key - secret x seed (mod 7) = 45 x 6 (mod 7) = 4 Encrypted Secret = key x secret = 45 x 4 = 180 Based on this encryption method, when choosing the random seed, show which number should not be used, because it would result in the Secret and the Encrypted Secret being the same. 6- Prime numbers have recently grabbed the attention of, not only mathematicians but also computer scientists and engineers. Compose a research report and present your findings in a report, highlighting the reasons behind this interest, and presenting an application where Prime Numbers are being used in the industry of Computing. In your research, include the reason why prime numbers, and not any other number, are used in that application. 7- Hashing and Load balancing are two related applications that govern the work of distributed load systems. The core idea of load balancing is having a system with multiple copies of the same resource, then distributing the work among these resources. During this stage, the load balancer uses the probability theories we studied during this course. Assess, through some research, the reasoning behind the relevance of probabilities in this application. Include in your assessment the method of usage and benefit within this specific application