Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Below are two examples of code fragments, indicated by numbers 1 and 2. a) The above two pieces of code are examples of metamorphic software.
Below are two examples of code fragments, indicated by numbers 1 and 2.
a) The above two pieces of code are examples of metamorphic software. What is metamorphic software? Explain why metamorphic software is needed.
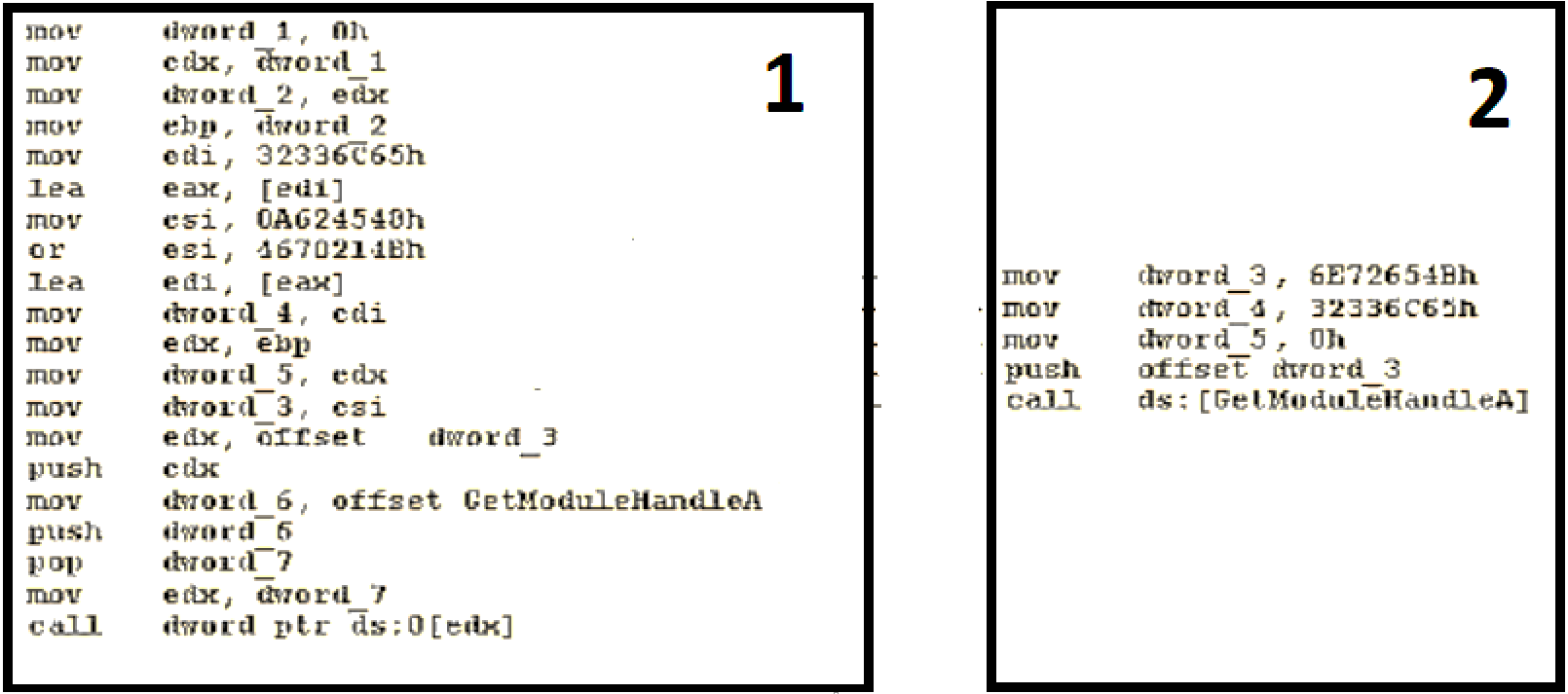 b) From the SRE (Software Reverse Engineering) point of view, can it be interpreted as "A metamorphic piece of code may also have code obfuscation"? Discuss.
b) From the SRE (Software Reverse Engineering) point of view, can it be interpreted as "A metamorphic piece of code may also have code obfuscation"? Discuss.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


