Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Birthday collision attack implementation Implement the given algorithm in C/C++ or Python to search for collisions in a toy example of a cryptographic hash function
Birthday collision attack implementation
Implement the given algorithm in C/C++ or Python to search for collisions in a toy example of a cryptographic hash function with n-but output where n are the first n bits of the SHA-1 message digest. Specifically, write the program which searches for collisions in the first 4,8,12,16... bits of the SHA-1 digest. Work with the hex representation of the digest. Search for a pair of SHA-1 digests with the first 1,2,3... symbols (in hex) being the same. Stop at the number of bits which takes a long time (over 15 mins).
For each output length, count the timing which the birthday attack takes. 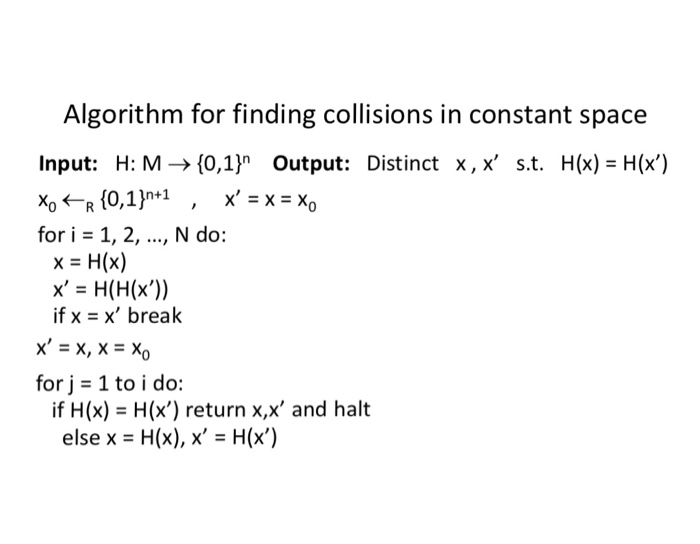

Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


