Answered step by step
Verified Expert Solution
Question
1 Approved Answer
BIT354 Network Vulnerability Pen X M Inbox (1,306) - binodgautam 1948 x C Apps S a. online.melbournepolytechnic.edu.au/mod/quiz/attempt.php?attempt=557994&cmid=1242826 Subscene - Passion... LE LIVVT JUULUV 13
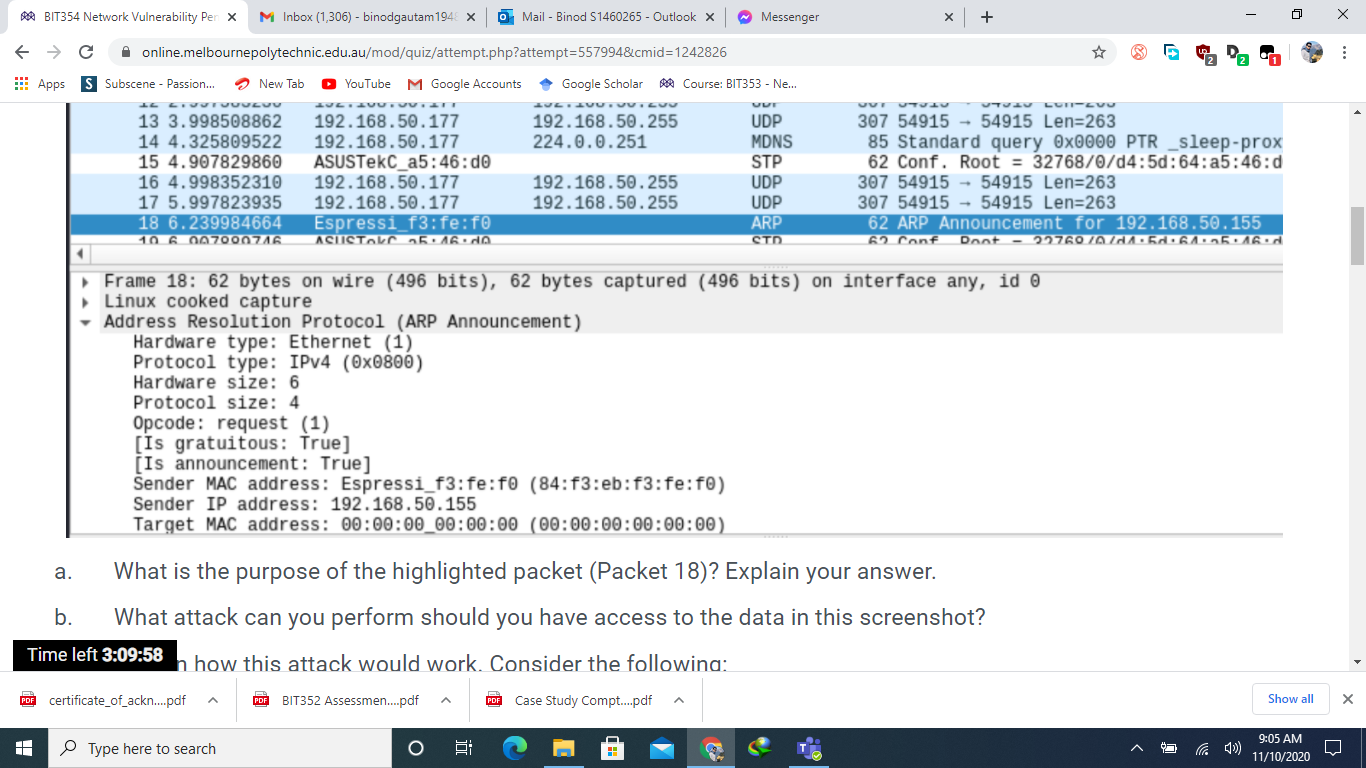
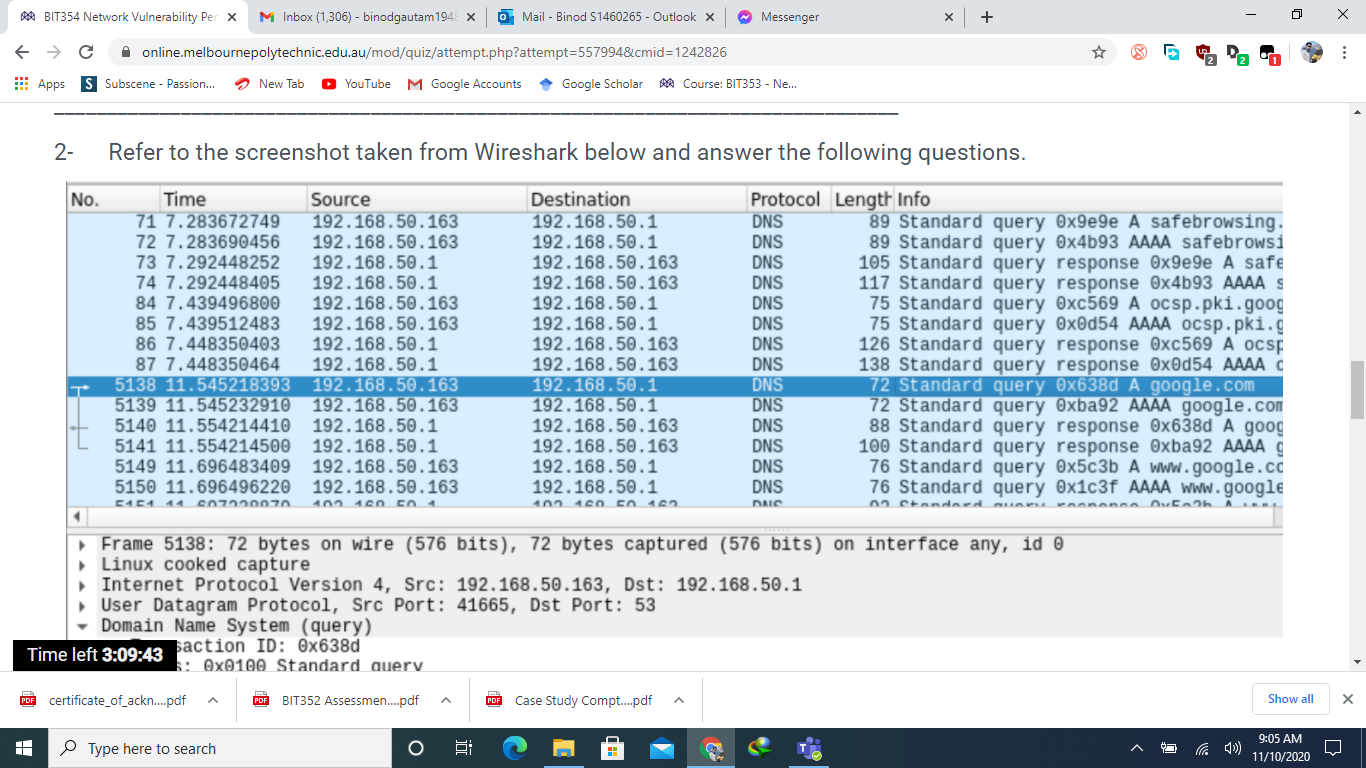
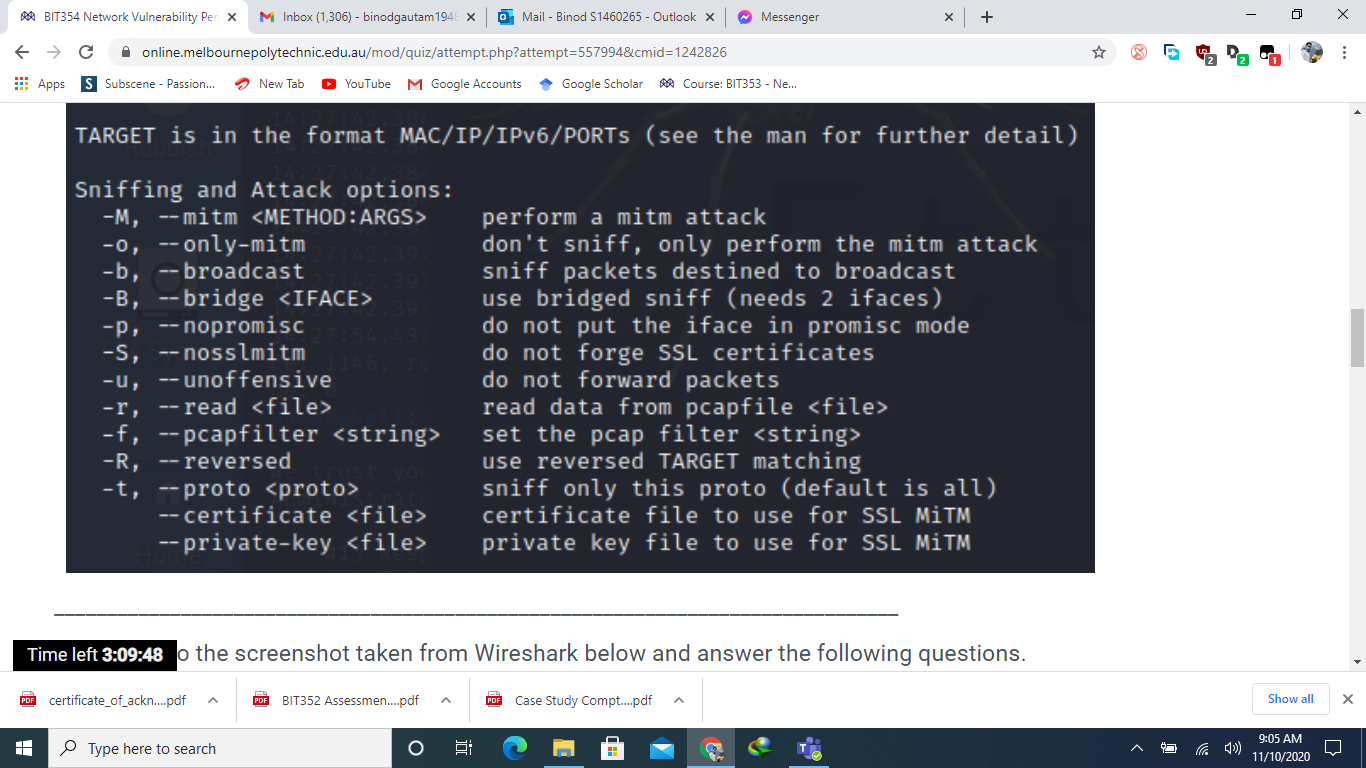
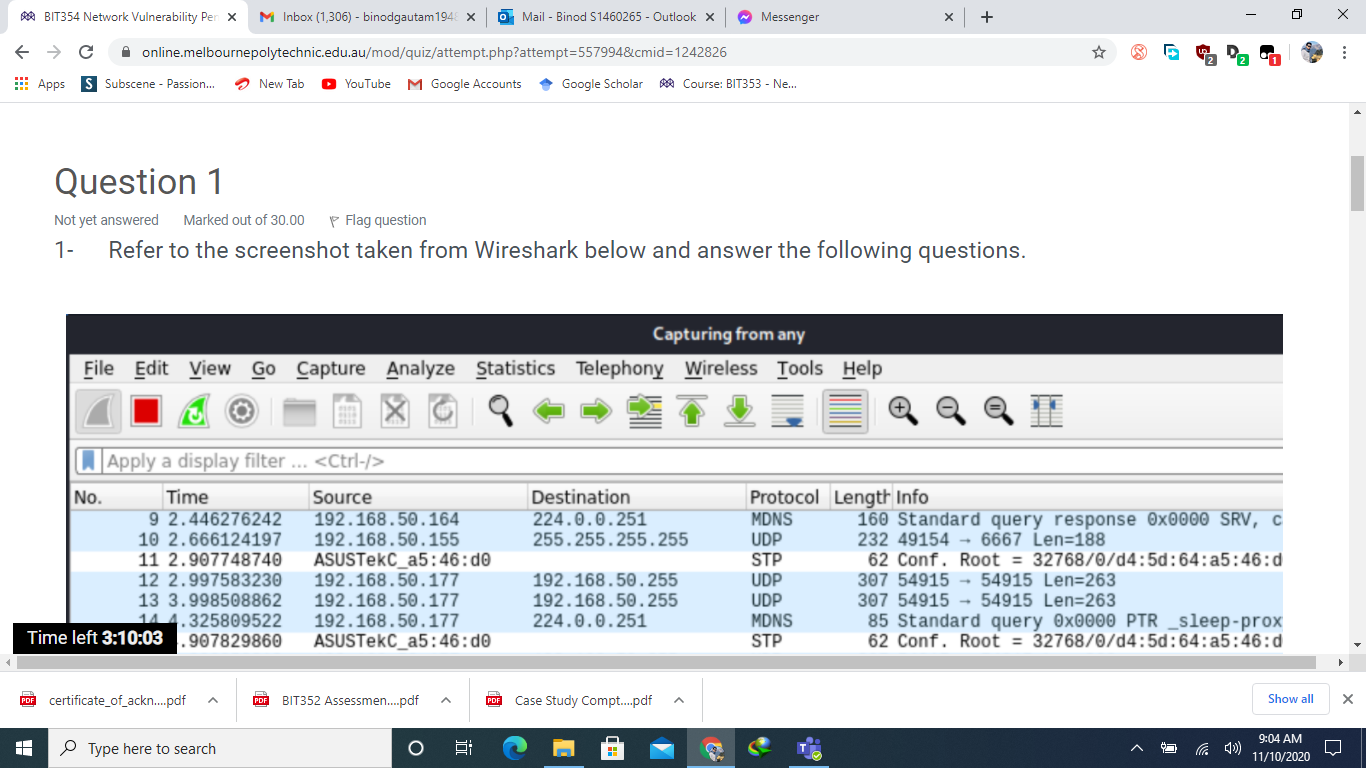
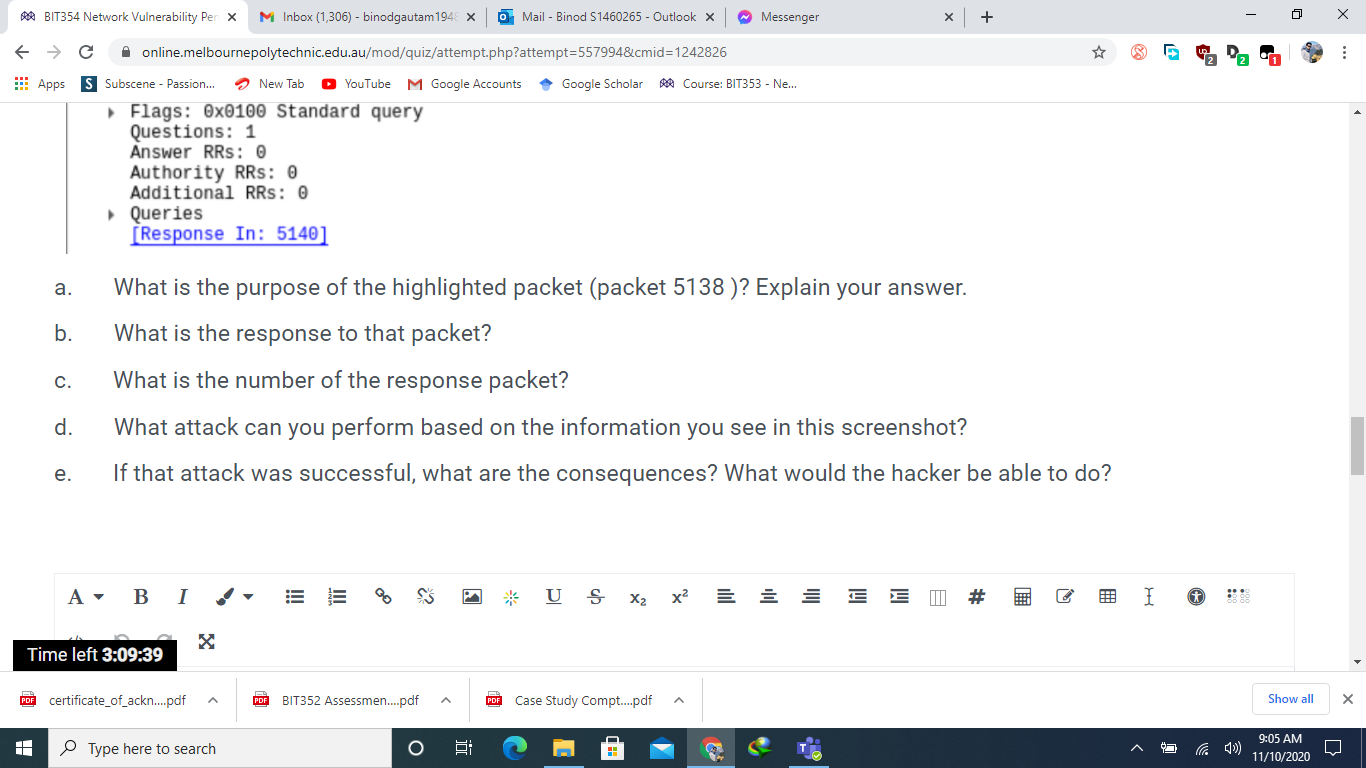
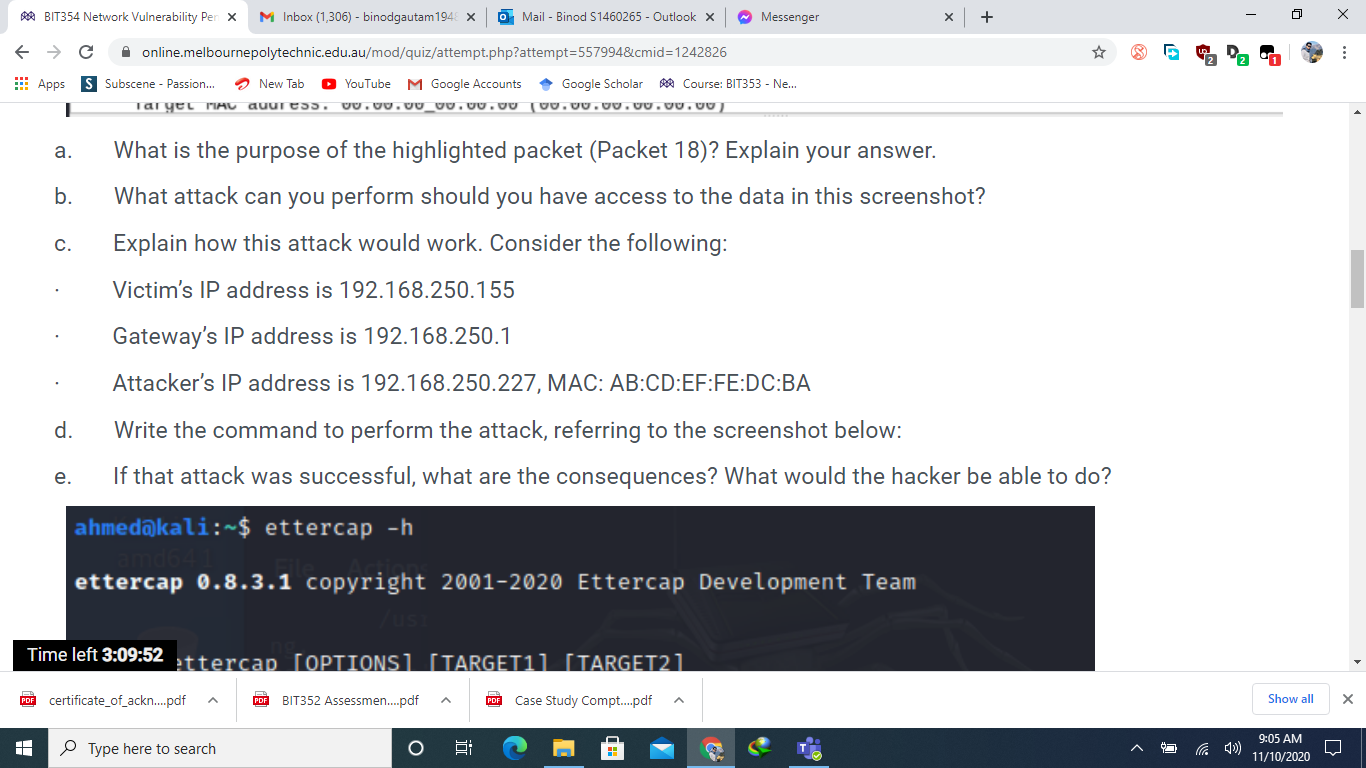
BIT354 Network Vulnerability Pen X M Inbox (1,306) - binodgautam 1948 x C Apps S a. online.melbournepolytechnic.edu.au/mod/quiz/attempt.php?attempt=557994&cmid=1242826 Subscene - Passion... LE LIVVT JUULUV 13 3.998508862 14 4.325809522 15 4.907829860 16 4.998352310 17 5.997823935 18 6.239984664 10 6 007000716 New Tab YouTube M Google Accounts LUE. AVU.0.211 192.168.50.177 192.168.50.177 ASUSTeKC_a5:46:d0 192.168.50.177 192.168.50.177 Espressi_f3:fe:f0 PDF certificate_of_ackn....pdf ASUSTOKS 25:16.do Hardware type: Ethernet (1) Protocol type: IPv4 (0x0800) Hardware size: 6 Protocol size: 4 Opcode: request (1) [Is gratuitous: True] [Is announcement: True] Type here to search Mail - Binod S1460265- Outlook X Google Scholar Course: BIT353 - Ne... UUT UDP MDNS STP UDP UDP ARP STD AVE. AVU.vu.com Sender MAC address: Espressi_f3:fe:f0 (84:f3:eb:f3:fe:f0) Sender IP address: 192.168.50.155 Target MAC address: 00:00:00 00:00:00 (00:00:00:00:00:00) O 192.168.50.255 224.0.0.251 6: 192.168.50.255 192.168.50.255 < Frame 18: 62 bytes on wire (496 bits), 62 bytes captured (496 bits) on interface any, id 0 Linux cooked capture Address Resolution Protocol (ARP Announcement) n how this attack would work. Consider the following: PDF BIT352 Assessmen....pdf FOR Case Study Compt....pdf ^ ~ Messenger What is the purpose of the highlighted packet (Packet 18)? Explain your answer. What attack can you perform should you have access to the data in this screenshot? b. Time left 3:09:58 x + LUII-LVU 5491554915 Len=263 307 85 Standard query 0x0000 PTR _sleep-prox 62 Conf. Root = 32768/0/d4:5d:64:a5:46:d 307 5491554915 Len=263 307 54915 54915 Len=263 62 ARP Announcement for 192.168.50.155 62 Conf Dont - 22760/0/11:5d:61:35:16.d 0 Show all 9:05 AM 11/10/2020 X : X BIT354 Network Vulnerability Pen X M Inbox (1,306) - binodgautam 1948 x C Apps S Subscene - Passion... Apps 2- H No. T online.melbournepolytechnic.edu.au/mod/quiz/attempt.php?attempt=557994&cmid=1242826 New Tab YouTube M Google Accounts Google ScholarCourse: BIT353 - Ne... Refer to the screenshot taken from Wireshark below and answer the following questions. Time Protocol Length Info 71 7.283672749 72 7.283690456 73 7.292448252 74 7.292448405 84 7.439496800 85 7.439512483 192.168.50.163 192.168.50.163 192.168.50.163 192.168.50.1 192.168.50.1 192.168.50.163 86 7.448350403 192.168.50.1 87 7.448350464 192.168.50.1 5138 11.545218393 192.168.50.163 5139 11.545232910 192.168.50.163 5140 11.554214410 192.168.50.1 5141 11.554214500 192.168.50.1 5149 11.696483409 192.168.50.163 5150 11.696496220 192.168.50.163 [151 11 607220070 103 160 50 1 Source PDF certificate_of_ackn....pdf Mail - Binod S1460265- Outlook X ~ Messenger User Datagram Protocol, Src Port: 41665, Dst Port: 53 Domain Name System (query) Time left 3:09:43 action ID: 0x638d s: 0x0100 Standard query PDF BIT352 Assessmen....pdf Type here to search O Destination 192.168.50.1 192.168.50.1 192.168.50.163 192.168.50.163 192.168.50.1 192.168.50.1 192.168.50.163 192.168.50.163 192.168.50.1 192.168.50.1 192.168.50.163 192.168.50.163 192.168.50.1 192.168.50.1 102 160 50 162 6: ( Frame 5138: 72 bytes on wire (576 bits), 72 bytes captured (576 bits) on interface any, id 0 Linux cooked capture Internet Protocol Version 4, Src: 192.168.50.163, Dst: 192.168.50.1 DNS DNS DNS DNS DNS DNS DNS DNS DNS DNS DNS DNS DNS DNS DUC PDF Case Study Compt....pdf x + 89 Standard query 0x9e9e A safebrowsing. 89 Standard query 0x4b93 AAAA safebrowsi 105 Standard query response 0x9e9e A safe 117 Standard query response 0x4b93 AAAA s 75 Standard query 0xc569 A ocsp.pki.goog 75 Standard query 0x0d54 AAAA ocsp.pki.g 126 Standard query response 0xc569 A ocsp 138 Standard query response 0x0d54 AAAA c 72 Standard query 0x638d A google.com 72 Standard query Oxba92 AAAA google.com 88 Standard query response 0x638d A goog 100 Standard query response Oxba92 AAAA g 76 Standard query 0x5c3b A www.google.co 76 Standard query 0x1c3f AAAA www.google 02 Standard 2 Pa Coononno Oxfo2h Ou Fath A 0 Show all 9:05 AM 11/10/2020 X : X BIT354 Network Vulnerability Pen X M Inbox (1,306) - binodgautam1948 X online.melbournepolytechnic.edu.au/mod/quiz/attempt.php?attempt=557994&cmid=1242826 Apps Subscene - Passion... YouTube M Google Accounts TARGET is in the format MAC/IP/IPv6/PORTS (see the man for further detail) Sniffing and Attack options: -M, --mitm -0, --only-mitm -b, -- broadcast -B, --bridge -p, --nopromisc 7:54.437 -S, --nosslmitm -u, -- unoffensive -r, --read -f, --pcapfilter -R, - reversed -t, --proto --certificate --private-key New Tab PDF certificate of ackn....pdf Type here to search BIT352 Assessmen....pdf Mail - Binod S1460265- Outlook X 6: Google Scholar ~ Messenger Time left 3:09:48 o the screenshot taken from Wireshark below and answer the following questions. Course: BIT353 - Ne... + perform a mitm attack don't sniff, only perform the mitm attack sniff packets destined to broadcast use bridged sniff (needs 2 ifaces) do not put the iface in promisc mode do not forge SSL certificates do not forward packets Case Study Compt....pdf read data from pcapfile set the pcap filter reversed TARGET matching sniff only this proto (default is all) certificate file to use for SSL MTM private key file to use for SSL MiTM :)) 0 Show all 9:05 AM 11/10/2020 X : X BIT354 Network Vulnerability Pen x M Inbox (1,306) - binodgautam 1948 x C Apps S online.melbournepolytechnic.edu.au/mod/quiz/attempt.php?attempt=557994&cmid=1242826 Subscene - Passion... No. Question 1 Not yet answered Marked out of 30.00 Flag question 1- Refer to the screenshot taken from Wireshark below and answer the following questions. Capturing from any File Edit View Go Capture Analyze Statistics Telephony Wireless Tools Help Apply a display filter ... Time Source 9 2.446276242 10 2.666124197 11 2.907748740 12 2.997583230 13 3.998508862 14 4.325809522 New Tab YouTube M Google Accounts Google ScholarCourse: BIT353 - Ne... 192.168.50.164 192.168.50.155 ASUSTeKC_a5:46:d0 192.168.50.177 192.168.50.177 192.168.50.177 Time left 3:10:03.907829860 ASUSTeKC_a5:46:d0 PDF certificate_of_ackn....pdf Type here to search Mail - Binod S1460265- Outlook X PDF BIT352 Assessmen....pdf O 6: Destination 224.0.0.251 255.255.255.255 Messenger 192.168.50.255 192.168.50.255 224.0.0.251 PDF Case Study Compt.....pdf (= Protocol Length Info MDNS UDP STP UDP UDP MDNS STP x + 2 Pa 160 Standard query response 0x0000 SRV, c 232 491546667 Len-188 62 Conf. Root = 32768/0/d4:5d:64:a5:46:d 307 54915 54915 Len=263 307 5491554915 Len=263 85 Standard query 0x0000 PTR _sleep-prox 62 Conf. Root = 32768/0/d4:5d:64:a5:46:d 0 Show all 9:04 AM 11/10/2020 X : X BIT354 Network Vulnerability Pen X M Inbox (1,306) - binodgautam 1948 x C Apps S a. b. H C. d. e. online.melbournepolytechnic.edu.au/mod/quiz/attempt.php?attempt=557994&cmid=1242826 Subscene - Passion... Flags: 0x0100 Standard query Questions: 1 Answer RRS: 0 Authority RRs: 0 Additional RRs: 0 Queries [Response In: 5140] A BI Time left 3:09:39 PDF certificate_of_ackn....pdf New Tab YouTube M Google Accounts Google ScholarCourse: BIT353 - Ne... What is the purpose of the highlighted packet (packet 5138 )? Explain your answer. What is the response to that packet? What is the number of the response packet? What attack can you perform based on the information you see in this screenshot? If that attack was successful, what are the consequences? What would the hacker be able to do? Type here to search Mail - Binod S1460265- Outlook X III PDF BIT352 Assessmen....pdf O 6: US Messenger X PDF Case Study Compt.....pdf x x + E E # I 2 Pa 88 0 Show all 9:05 AM 11/10/2020 X : X BIT354 Network Vulnerability Pen X M Inbox (1,306) - binodgautam 1948 x C Apps S T a. b. C. e. online.melbournepolytechnic.edu.au/mod/quiz/attempt.php?attempt=557994&cmid=1242826 Subscene - Passion... New Tab YouTube M Google Accounts Google Scholar Course: BIT353 - Ne... Taryel MAC address, 0.00.00_00.00.00 100.00.00.00.00.00 Mail - Binod S1460265- Outlook X Messenger What is the purpose of the highlighted packet (Packet 18)? Explain your answer. What attack can you perform should you have access to the data in this screenshot? Explain how this attack would work. Consider the following: Victim's IP address is 192.168.250.155 Gateway's IP address is 192.168.250.1 Attacker's IP address is 192.168.250.227, MAC: AB:CD:EF:FE:DC:BA d. Write the command to perform the attack, referring to the screenshot below: If that attack was successful, what are the consequences? What would the hacker be able to do? ahmed@kali:~$ ettercap -h ettercap 0.8.3.1 copyright 2001-2020 Ettercap Development Team /usi Time left 3:09:52 ttercap [OPTIONS] [TARGET1] [TARGET21 PDF certificate_of_ackn....pdf PDF BIT352 Assessmen....pdf FOR Case Study Compt....pdf Type here to search O x + 6: 422 0 Show all 9:05 AM 11/10/2020 X : X
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


