Answered step by step
Verified Expert Solution
Question
1 Approved Answer
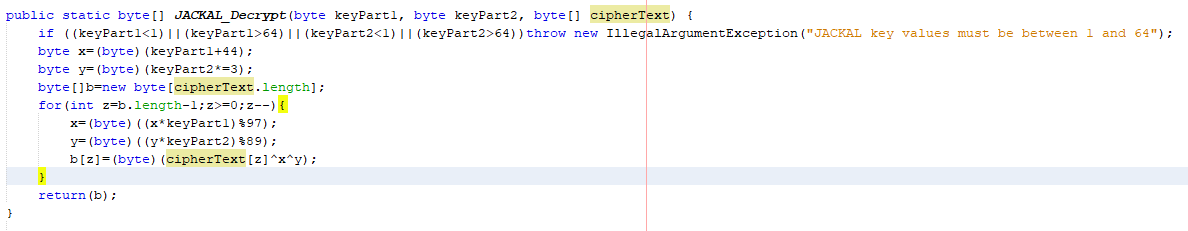
Brute Force Problem byte[] of cipher3.bin: B@5c647e05 public static byte[] JACKAL_Decrypt (byte keyParti, byte keyPart2, byte[] cipherText) { if ((keyParticl) || (keyPartl>64) II (keyPart264)) throw

Brute Force Problem
byte[] of cipher3.bin: B@5c647e05
public static byte[] JACKAL_Decrypt (byte keyParti, byte keyPart2, byte[] cipherText) { if ((keyParticl) || (keyPartl>64) II (keyPart264)) throw new IllegalArgumentException ("JACKAL key values must be between 1 and 64"); byte x= (byte) (keyPart1+44); byte v= (byte) (keyPart2*=3); byte[]b=new byte[cipherText.length); for (int z=b.length-1;z>=0;Z--) { x= (byte) ((x keyPartl) $97); y= (byte) ((y* keyPart2) 289); b[2]= (byte) (cipherText[z] *x*y); return (b); After decrypting the message, you immediately fly to New York and prepare to intercept the exchange. With the element of surprise on your side, you easily defeat the agents of P.H.A.N.T.O.M. You expect to retrieve the secret plans from them; unfortunately, all you find is a USB drive with a single encrypted file (cipher3.bin). Back at your headquarters, Q gives you an implementation of the JACKAL decryption algorithm (JACKAL_Decrypt), but he has no clue what the secret key might be. Notice that the number of possible keys is fairly low for the Jackal cipher: both parts of the key are numbers between 1 and 64. Further, you know that the plaintext is a BMP image file, which means that the value of the first byte is 66 (character 'B' in ASCII) and the value of the second byte is 77 (character 'M'). Can you find the correct key and decrypt the ciphertext? public static byte[] JACKAL_Decrypt (byte keyParti, byte keyPart2, byte[] cipherText) { if ((keyParticl) || (keyPartl>64) II (keyPart264)) throw new IllegalArgumentException ("JACKAL key values must be between 1 and 64"); byte x= (byte) (keyPart1+44); byte v= (byte) (keyPart2*=3); byte[]b=new byte[cipherText.length); for (int z=b.length-1;z>=0;Z--) { x= (byte) ((x keyPartl) $97); y= (byte) ((y* keyPart2) 289); b[2]= (byte) (cipherText[z] *x*y); return (b); After decrypting the message, you immediately fly to New York and prepare to intercept the exchange. With the element of surprise on your side, you easily defeat the agents of P.H.A.N.T.O.M. You expect to retrieve the secret plans from them; unfortunately, all you find is a USB drive with a single encrypted file (cipher3.bin). Back at your headquarters, Q gives you an implementation of the JACKAL decryption algorithm (JACKAL_Decrypt), but he has no clue what the secret key might be. Notice that the number of possible keys is fairly low for the Jackal cipher: both parts of the key are numbers between 1 and 64. Further, you know that the plaintext is a BMP image file, which means that the value of the first byte is 66 (character 'B' in ASCII) and the value of the second byte is 77 (character 'M'). Can you find the correct key and decrypt the ciphertextStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


