Question
Buffer Overflow Lab Smashing the Stack One way of manipulating the stack for unintended results is to change the return address on the stack to
Buffer Overflow Lab
Smashing the Stack
One way of manipulating the stack for unintended results is to change the return address on the stack to some pre-set location, possibly containing malicious code.
When the procedure exits, it returns to whatever memory address is in the return address portion of the stack.
If a malicious user can change the values of the stack to affect this address location, they can change which instruction gets executed next.
As we have previously seen, one way of changing memory locations is through a buffer overflow.
Remember that local variables are pushed onto the stack above the return address. If one of the local variables is a string, and the user has the opportunity to input a value for the string that overflows into the return address on the stack, they can effectively change where the procedure returns.
Step through the sample program and construct the necessary input string in the procedure to affect where the procedure returns to, by skipping the last output statement. Your output window should say "*** END OF PROGRAM ***", not "*** ILLEGAL INSTRUCTION ***".
Note that only the last three hex digits of the return address are used (there is no typable ASCII character with the hex value 04). Show the string you used, your reason for using the string, and a screenshot of the code, output, and memory that illustrates the stack and your clobbered return.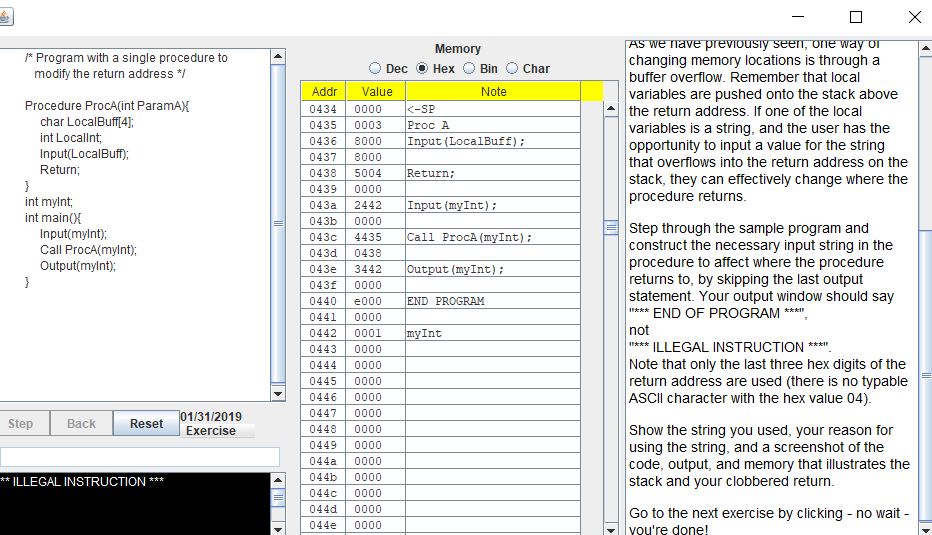
below is a copy of code
/* Program with a single procedure to modify the return address */ Procedure ProcA(int ParamA){ char LocalBuff[4]; int LocalInt; Input(LocalBuff); Return; } int myInt; int main(){ Input(myInt); Call ProcA(myInt); Output(myInt); }
This is all the information that was given. It can be done evidently.
Memory Program with a single procedure to modify the return address*/ changing memory locations is through a buffer overflow.Remember that local variables are pushed onto the stack above the return address. If one of the local variables is a string, and the user has the opportunity to input a value for the string that overflows into the return address on the stack, they can effectively change where the procedure returns DecO Hex OBin Char Note Addr Value 0434 0000 0435 0003 0436 8000 Input (LocalBuff); 0437 8000 0438 5004 0439 0000 043a 2442Input (myInt) 043b 0000 043c 4435 Call ProcA (myInt); 043d 0438 043e 3442Output (myInt) 043f 0000 0440 e000 END PR 0441 0000 0442 0001 0443 0000 0444 0000 0445 0000 0446 0000 0447 0000 0448 0000 0449 0000 044a 0000 044b 0000 044c 0000 044d 0000 044e 0000 Procedure ProcA(int ParamAXStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


