Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Can someone please help me with this? Problem 1. (30 points) In this problem, I want to show you an example of the challenges that
Can someone please help me with this?
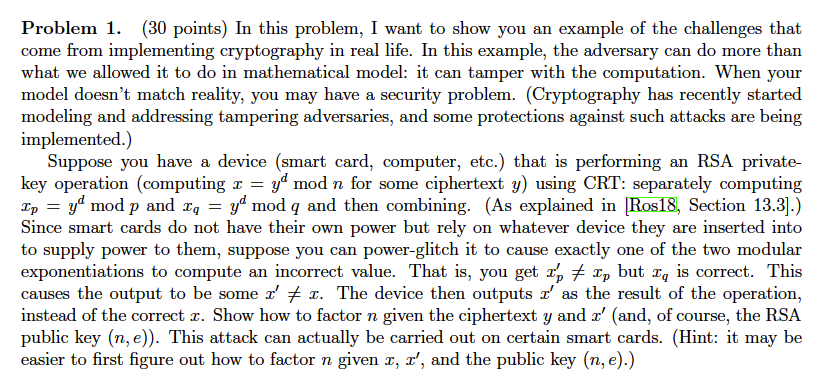
Problem 1. (30 points) In this problem, I want to show you an example of the challenges that come from implementing cryptography in real life. In this example, the adversary can do more than what we allowed it to do in mathematical model: it can tamper with the computation. When your model doesn't match reality, you may have a security problem. (Cryptography has recently started modeling and addressing tampering adversaries, and some protections against such attacks are being implemented.) Suppose you have a device (smart card, computer, etc.) that is performing an RSA private- key operation (computing x = yd mod n for some ciphertext y) using CRT: separately computing Zp yd mod p and zq-yd mod q and then combining. (As explained in 10S18, section 13.3].) Since smart cards do not have their own power but rely on whatever device they are inserted into to supply power to them, suppose you can power-glitch it to cause exactly one of the two modular exponentiations to compute an incorrect value. That is, you getxp but 2, is correct. This causes the output to be some z'x. The device then outputs z' as the result of the operation, instead of the correct r. Show how to factor n given the ciphertext y and z' (and, of course, the RSA public key (n, e)). This attack can actually be carried out on certain smart cards. (Hint: it may be easier to first figure out how to factor n given x, x', and the public key (n, e).) Problem 1. (30 points) In this problem, I want to show you an example of the challenges that come from implementing cryptography in real life. In this example, the adversary can do more than what we allowed it to do in mathematical model: it can tamper with the computation. When your model doesn't match reality, you may have a security problem. (Cryptography has recently started modeling and addressing tampering adversaries, and some protections against such attacks are being implemented.) Suppose you have a device (smart card, computer, etc.) that is performing an RSA private- key operation (computing x = yd mod n for some ciphertext y) using CRT: separately computing Zp yd mod p and zq-yd mod q and then combining. (As explained in 10S18, section 13.3].) Since smart cards do not have their own power but rely on whatever device they are inserted into to supply power to them, suppose you can power-glitch it to cause exactly one of the two modular exponentiations to compute an incorrect value. That is, you getxp but 2, is correct. This causes the output to be some z'x. The device then outputs z' as the result of the operation, instead of the correct r. Show how to factor n given the ciphertext y and z' (and, of course, the RSA public key (n, e)). This attack can actually be carried out on certain smart cards. (Hint: it may be easier to first figure out how to factor n given x, x', and the public key (n, e).)Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


