Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Chat over a TCP connection Assumption: the information required to create a TCP socket (IP address and port number of the TCP server) is
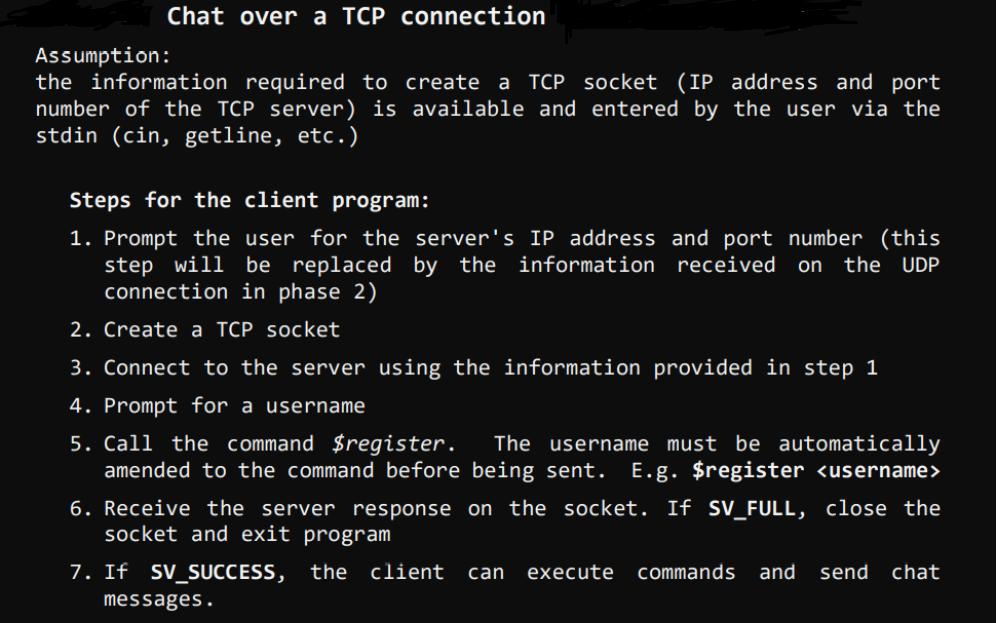
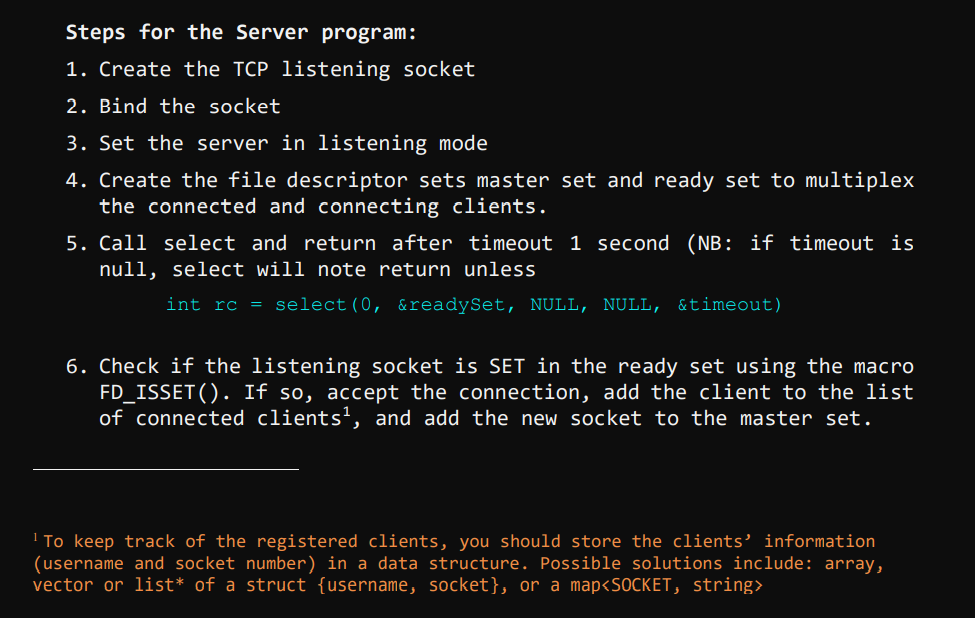
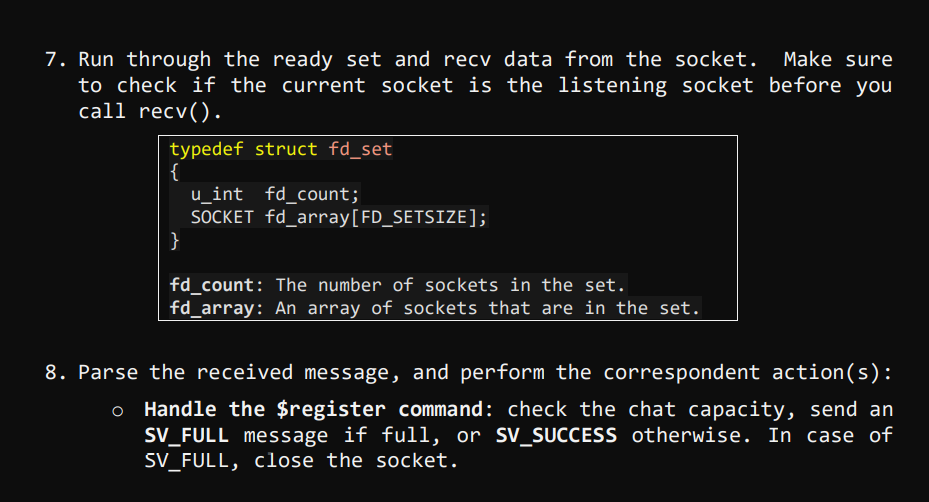
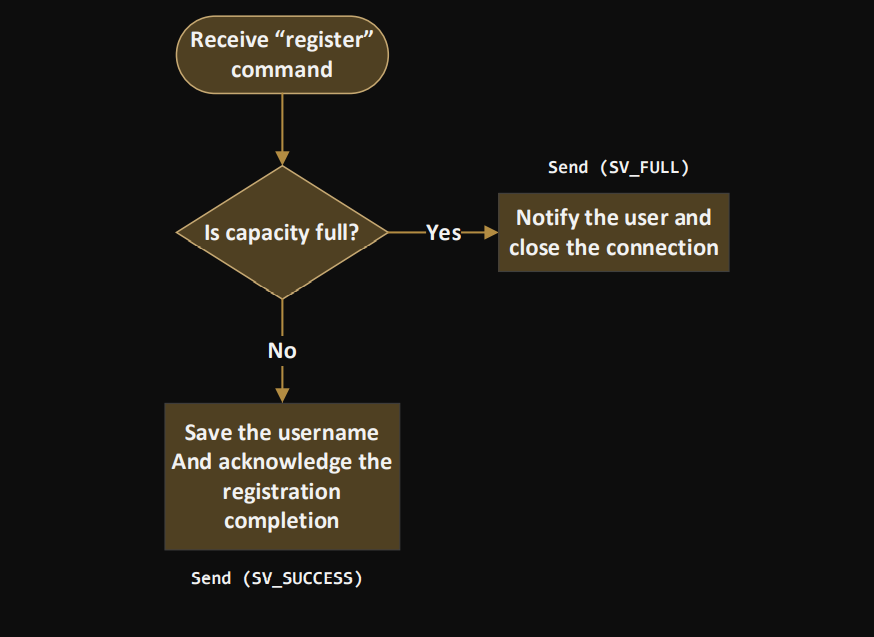
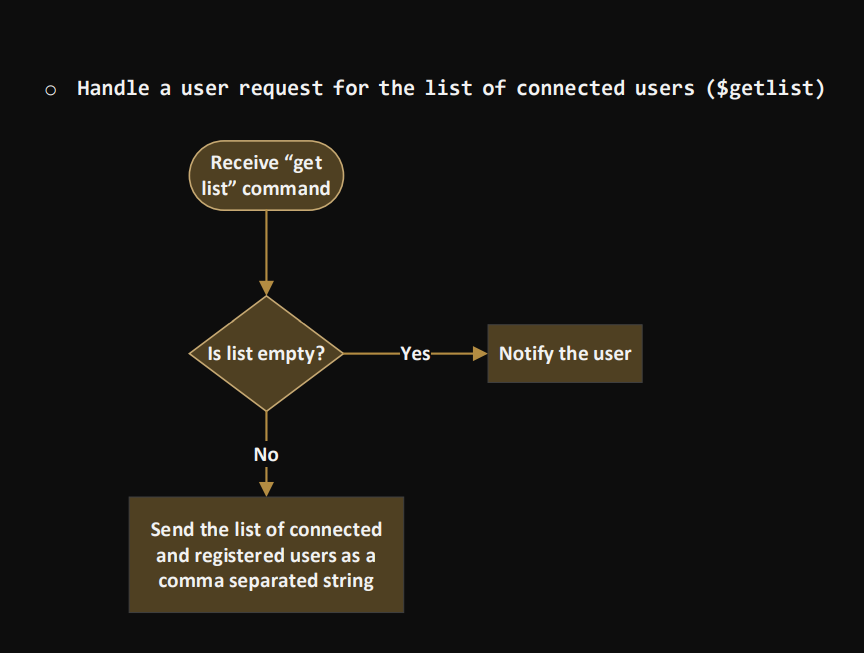
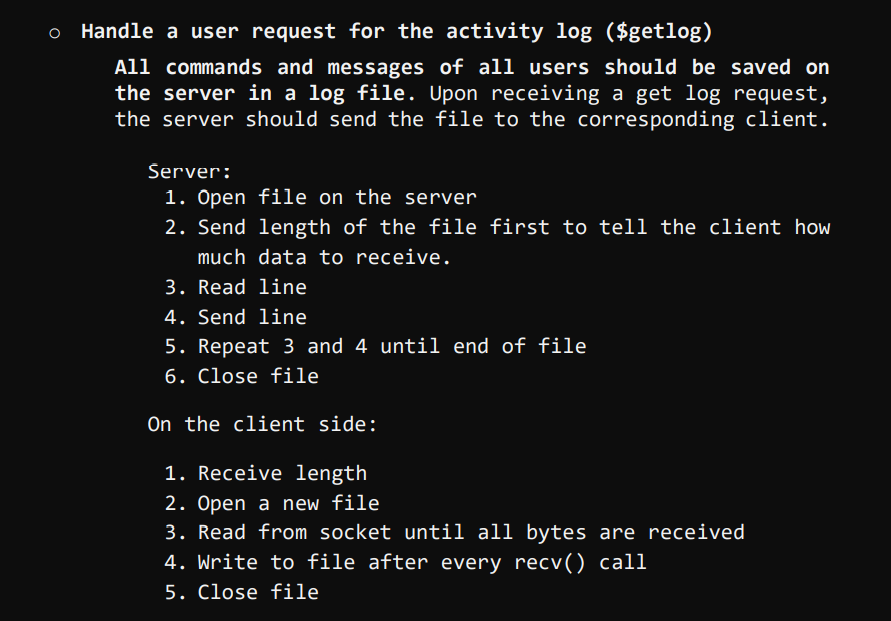
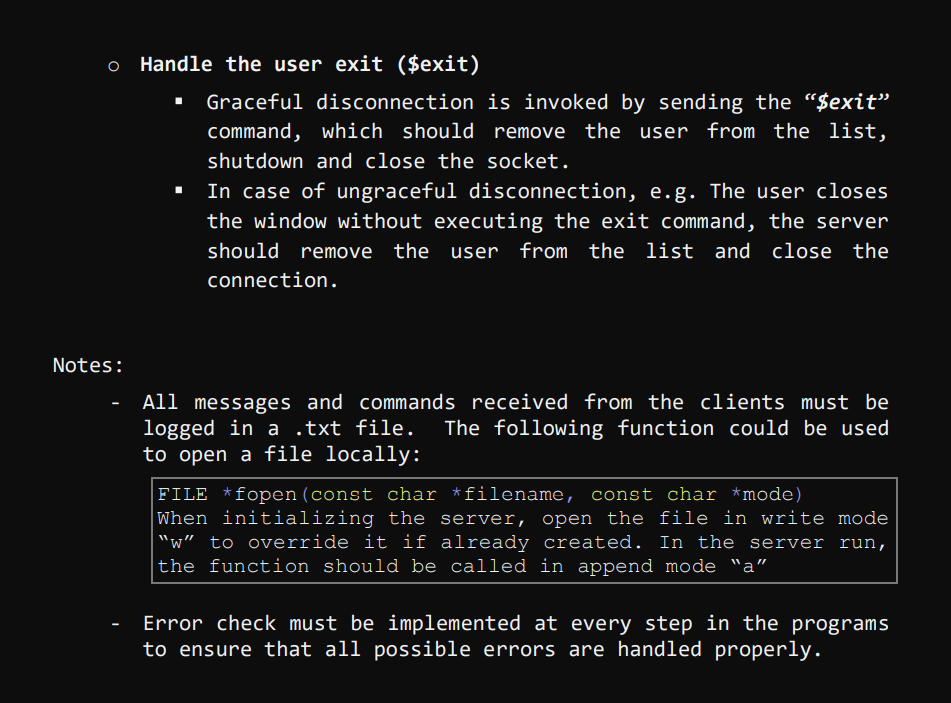
Chat over a TCP connection Assumption: the information required to create a TCP socket (IP address and port number of the TCP server) is available and entered by the user via the stdin (cin, getline, etc.) Steps for the client program: 1. Prompt the user for the server's IP address and port number (this step will be replaced by the information received on the UDP connection in phase 2) 2. Create a TCP socket 3. Connect to the server using the information provided in step 1 4. Prompt for a username 5. Call the command $register. The username must be automatically amended to the command before being sent. E.g. $register 6. Receive the server response on the socket. If SV_FULL, close the socket and exit program 7. If SV_SUCCESS, the client can execute commands and send chat messages. Steps for the Server program: 1. Create the TCP listening socket 2. Bind the socket 3. Set the server in listening mode 4. Create the file descriptor sets master set and ready set to multiplex the connected and connecting clients. 5. Call select and return after timeout 1 second (NB: if timeout is null, select will note return unless int rc = select(0, &readySet, NULL, NULL, &timeout) 6. Check if the listening socket is SET in the ready set using the macro FD_ISSET(). If so, accept the connection, add the client to the list of connected clients, and add the new socket to the master set. To keep track of the registered clients, you should store the clients' information (username and socket number) in a data structure. Possible solutions include: array, vector or list* of a struct {username, socket}, or a map 7. Run through the ready set and recv data from the socket. to check if the current socket is the listening socket before you call recv(). typedef struct fd_set { } u_int fd_count; SOCKET fd_array[FD_SETSIZE]; fd_count: The number of sockets in the set. fd_array: An array of sockets that are in the set. 8. Parse the received message, and perform the correspondent action(s): o Handle the $register command: check the chat capacity, send an SV_FULL message if full, or SV_SUCCESS otherwise. In case of SV_FULL, close the socket. Receive "register" command Is capacity full? No Save the username And acknowledge the registration completion Send (SV_SUCCESS) -Yes- Send (SV_FULL) Notify the user and close the connection o Handle a user request for the list of connected users ($getlist) Receive "get list" command Is list empty? No Send the list of connected and registered users as a comma separated string -Yes- Notify the user o Handle a user request for the activity log ($getlog) All commands and messages of all users should be saved on the server in a log file. Upon receiving a get log request, the server should send the file to the corresponding client. Server: 1. Open file on the server 2. Send length of the file first to tell the client how much data to receive. 3. Read line 4. Send line 5. Repeat 3 and 4 until end of file 6. Close file On the client side: 1. Receive length 2. Open a new file 3. Read from socket until all bytes are received 4. Write to file after every recv() call 5. Close file o Handle the user exit ($exit) Notes: Graceful disconnection is invoked by sending the $exit command, which should remove the user from the list, shutdown and close the socket. In case of ungraceful disconnection, e.g. The user closes the window without executing the exit command, the server should remove the user from the list and close the connection. All messages and commands received from the clients must be logged in a .txt file. The following function could be used to open a file locally: FILE *fopen (const char *filename, const char *mode) When initializing the server, open the file in write mode "w" to override it if already created. In the server run, the function should be called in append mode a" Error check must be implemented at every step in the programs to ensure that all possible errors are handled properly.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


