Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Checkpoint 2 - Advanced Caesar Cipher When encrypted, each letter in the message steps forward multiple letters in the alphabet (A encrypted by five
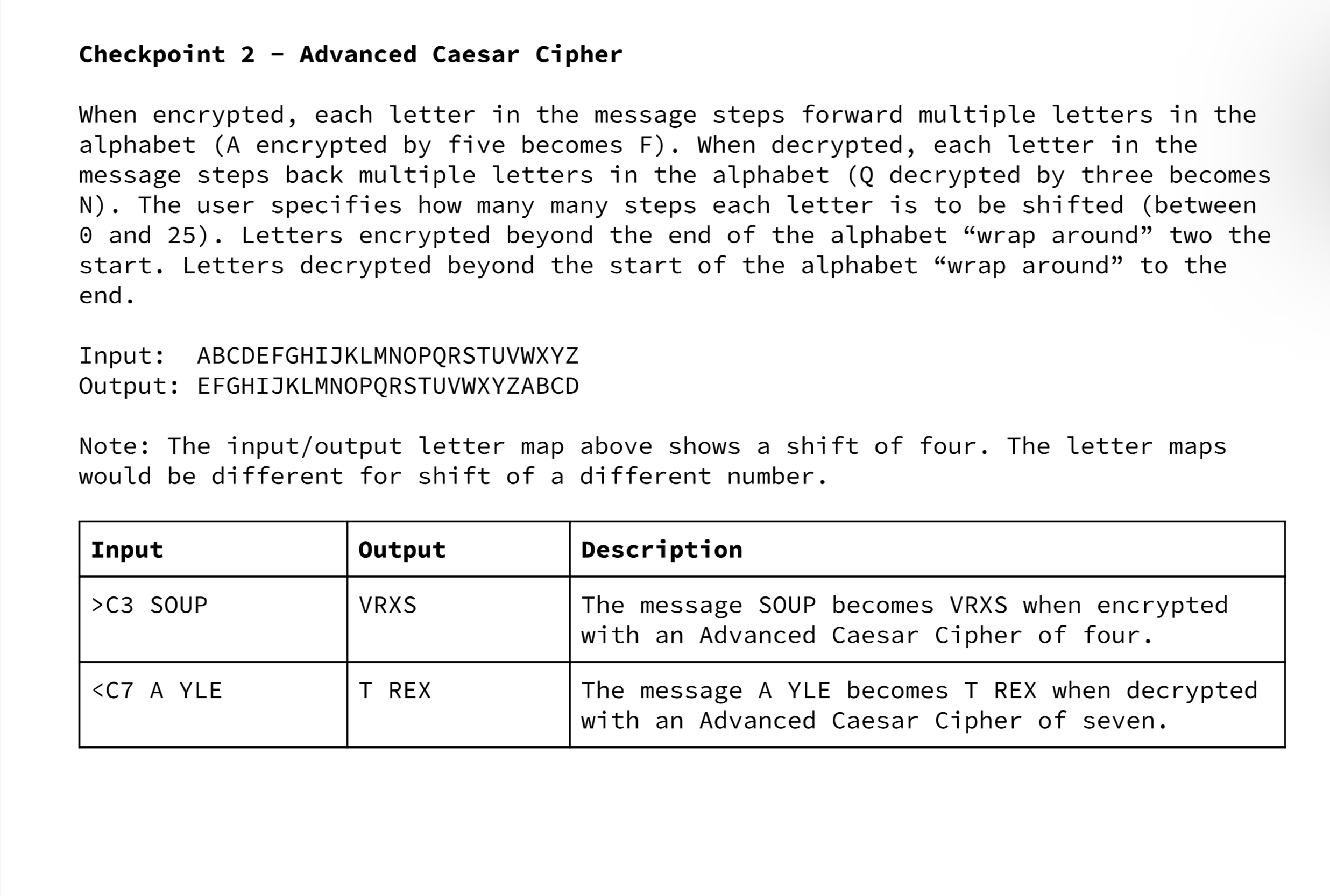
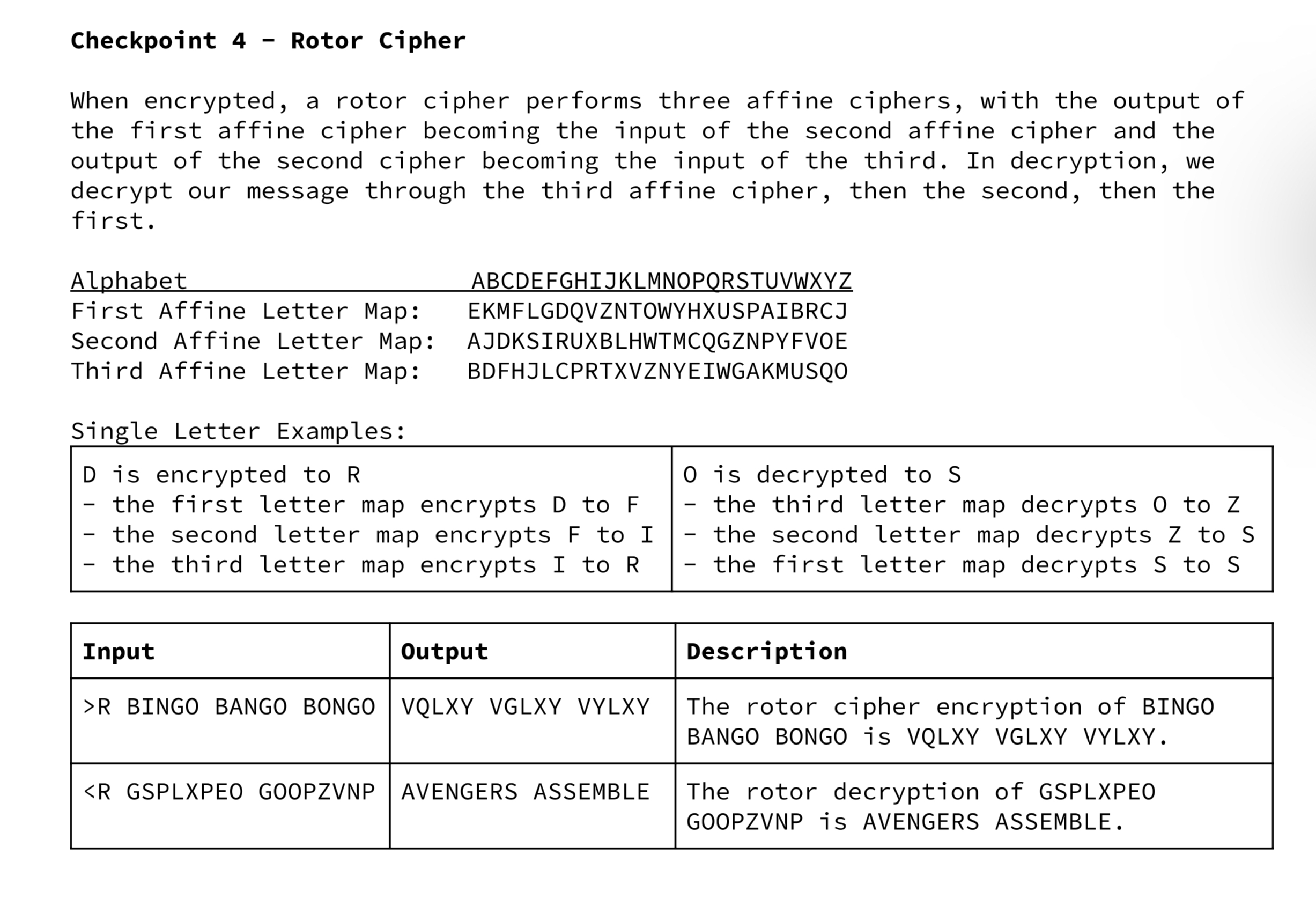
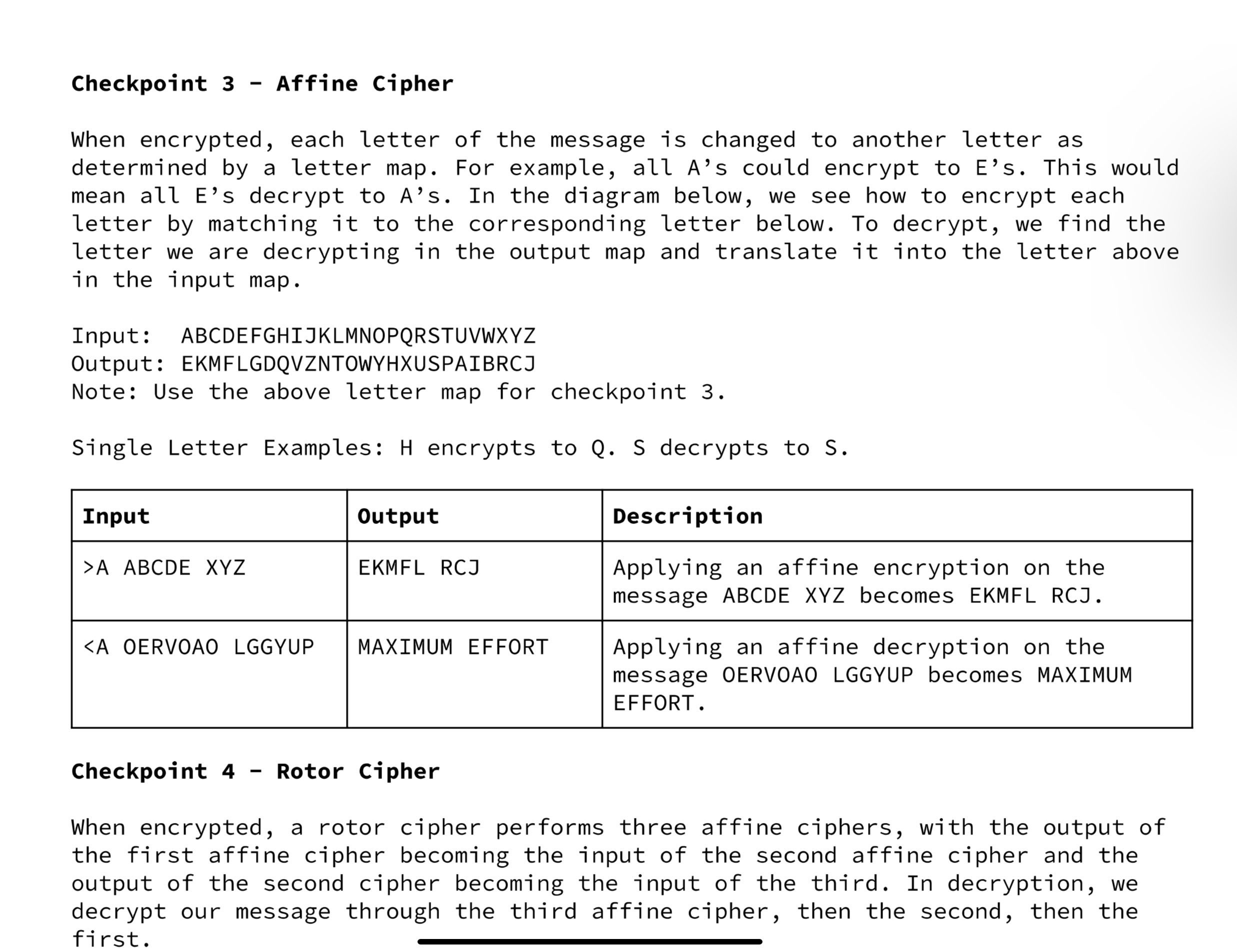
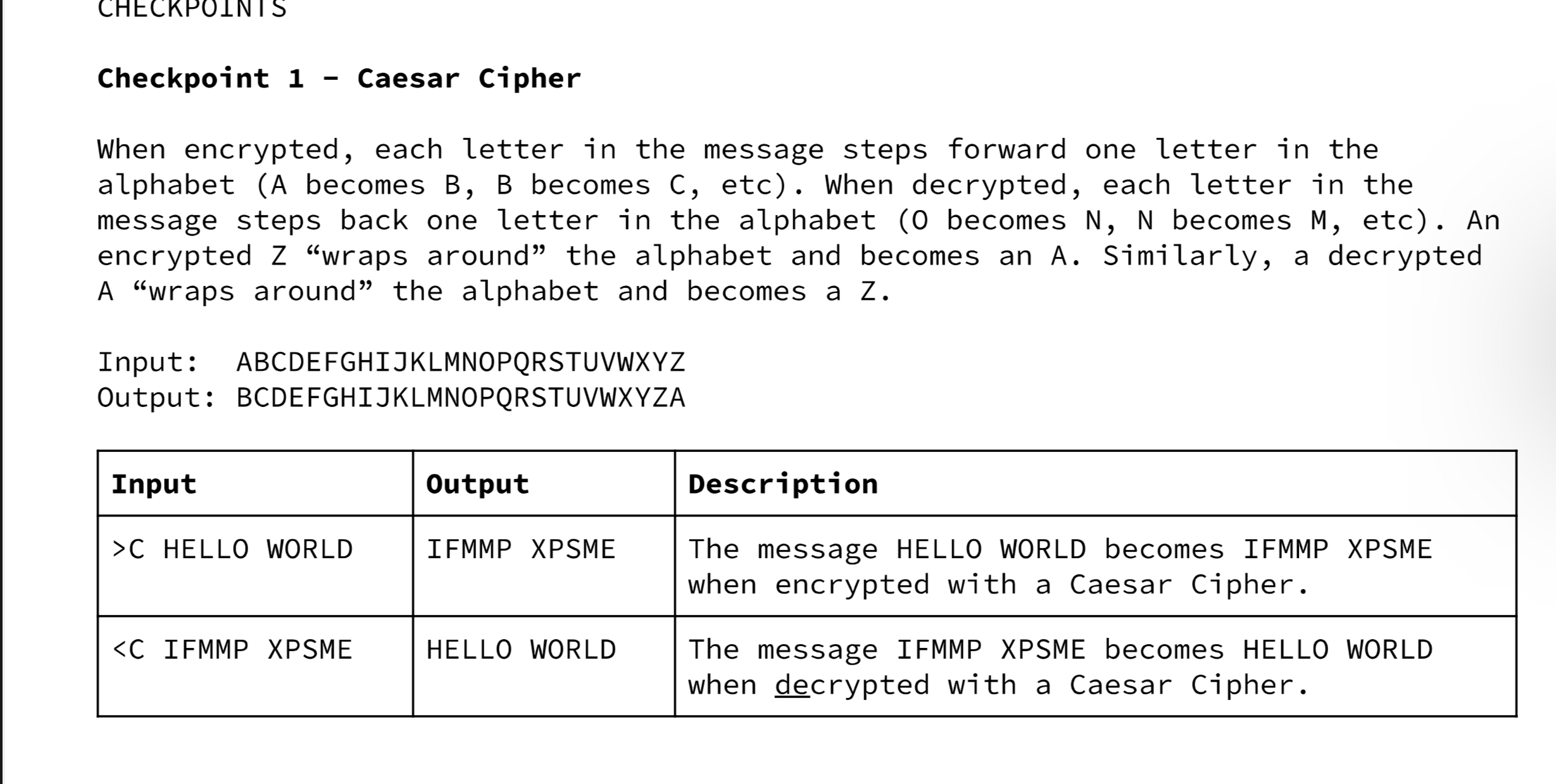
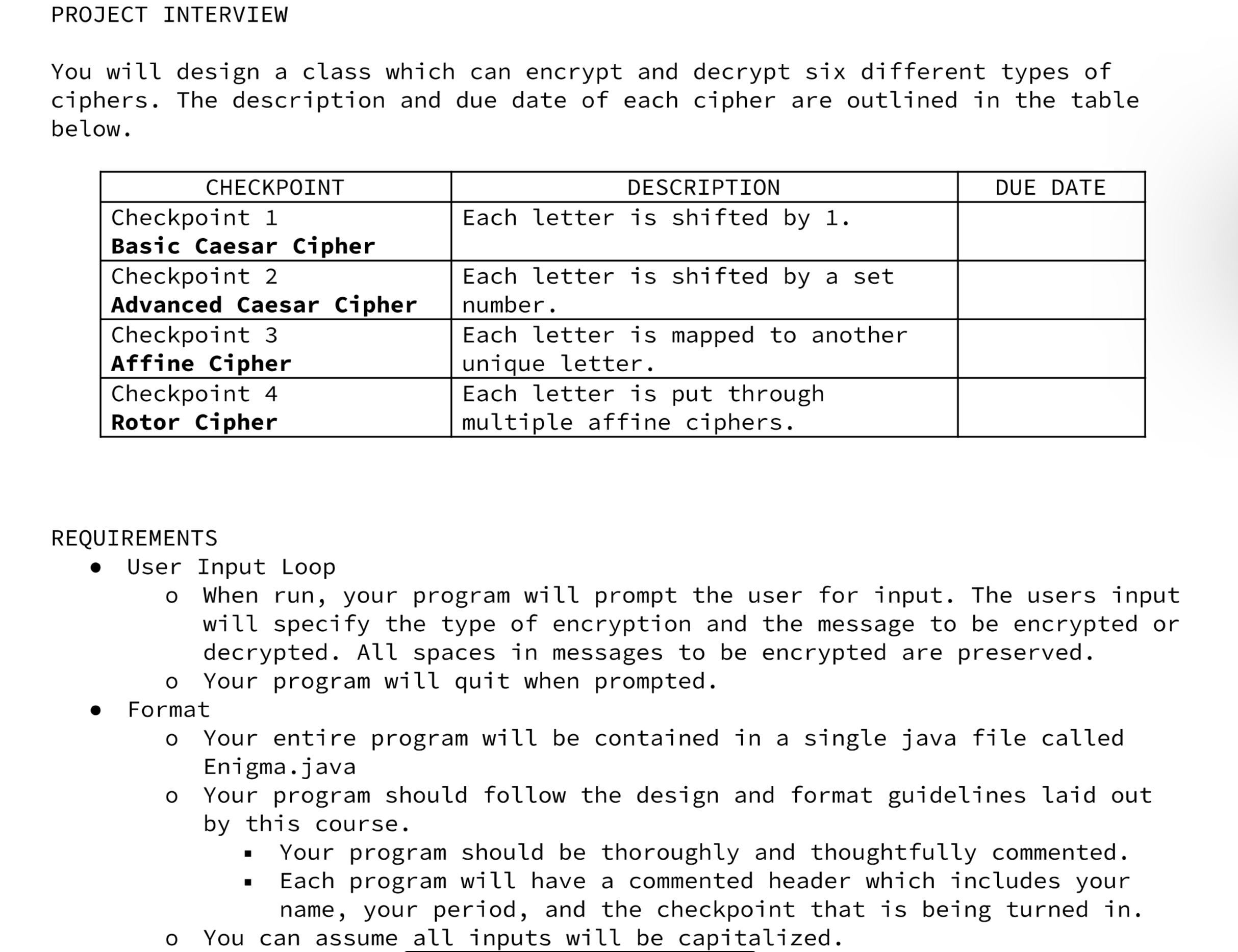
Checkpoint 2 - Advanced Caesar Cipher When encrypted, each letter in the message steps forward multiple letters in the alphabet (A encrypted by five becomes F). When decrypted, each letter in the message steps back multiple letters in the alphabet (Q decrypted by three becomes N). The user specifies how many many steps each letter is to be shifted (between 0 and 25). Letters encrypted beyond the end of the alphabet "wrap around" two the start. Letters decrypted beyond the start of the alphabet "wrap around" to the end. Input: ABCDEFGHIJKLMNOPQRSTUVWXYZ Output: EFGHIJKLMNOPQRSTUVWXYZABCD Note: The input/output letter map above shows a shift of four. The letter maps would be different for shift of a different number. Input Output >C3 SOUP VRXS - Checkpoint 4 Rotor Cipher When encrypted, a rotor cipher performs three affine ciphers, with the output of the first affine cipher becoming the input of the second affine cipher and the output of the second cipher becoming the input of the third. In decryption, we decrypt our message through the third affine cipher, then the second, then the first. Alphabet First Affine Letter Map: ABCDEFGHIJKLMNOPQRSTUVWXYZ EKMFLGDQVZNTOWYHXUSPAIBRCJ Second Affine Letter Map: AJDKSIRUXBLHWTMCQGZNPYFVOE Third Affine Letter Map: Single Letter Examples: BDFHJLCPRTXVZNYEIWGAKMUSQO D is encrypted to R O is decrypted to S - the first letter map encrypts D to F - - the second letter map encrypts F to I the third letter map encrypts I to R Input Output >R BINGO BANGO BONGO VQLXY VGLXY VYLXY Checkpoint 3 - Affine Cipher When encrypted, each letter of the message is changed to another letter as determined by a letter map. For example, all A's could encrypt to E's. This would mean all E's decrypt to A's. In the diagram below, we see how to encrypt each letter by matching it to the corresponding letter below. To decrypt, we find the letter we are decrypting in the output map and translate it into the letter above in the input map. Input: ABCDEFGHIJKLMNOPQRSTUVWXYZ Output: EKMFLGDQVZNTOWYHXUSPAIBRCJ Note: Use the above letter map for checkpoint 3. Single Letter Examples: H encrypts to Q. S decrypts to S. Input Output >A ABCDE XYZ EKMFL RCJ CHECKPOINTS Checkpoint 1 - Caesar Cipher When encrypted, each letter in the message steps forward one letter in the alphabet (A becomes B, B becomes C, etc). When decrypted, each letter in the message steps back one letter in the alphabet (0 becomes N, N becomes M, etc). An encrypted Z "wraps around the alphabet and becomes an A. Similarly, a decrypted A "wraps around" the alphabet and becomes a Z. Input: ABCDEFGHIJKLMNOPQRSTUVWXYZ Output: BCDEFGHIJKLMNOPQRSTUVWXYZA Input Output >C HELLO WORLD IFMMP XPSME PROJECT INTERVIEW You will design a class which can encrypt and decrypt six different types of ciphers. The description and due date of each cipher are outlined in the table below. CHECKPOINT Checkpoint 1 Basic Caesar Cipher Checkpoint 2 Advanced Caesar Cipher Checkpoint 3 Affine Cipher Checkpoint 4 Rotor Cipher DESCRIPTION DUE DATE Each letter is shifted by 1. Each letter is shifted by a set. number. Each letter is mapped to another unique letter. Each letter is put through multiple affine ciphers. REQUIREMENTS User Input Loop o When run, your program will prompt the user for input. The users input will specify the type of encryption and the message to be encrypted or decrypted. All spaces in messages to be encrypted are preserved. o Your program will quit when prompted. Format Your entire program will be contained in a single java file called Enigma.java Your program should follow the design and format guidelines laid out by this course. Your program should be thoroughly and thoughtfully commented. Each program will have a commented header which includes your name, your period, and the checkpoint that is being turned in. You can assume all inputs will be capitalized.
Step by Step Solution
There are 3 Steps involved in it
Step: 1
Based on your project requirements and the descriptions provided for the different types of ciphers Caesar Cipher Advanced Caesar Cipher Affine Cipher ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


